
A ransomware threat known as Pay2Key is targeting Israeli corporate networks. Researchers at the security company CheckPoint report that since it was first spotted in late October 2020, the new ransomware strain has successfully attacked several Israeli companies.
According to the CheckPoint report, the attacks usually happen after midnight when fewer IT employees maintain the targeted networks.
“The investigation so far indicates the attacker may have gained access to the organizations’ networks before the attack, but presented an ability to make a rapid move of spreading the ransomware within an hour to the entire network,” says CheckPoint.
The attackers follow a strict procedure to gain a foothold, propagate, and remotely control the infection within the compromised network.
About Pay2Key Ransomware
According to the research, Pay2Key is a unique ransomware, made from scratch, with no overlaps with other ransomware strains. The ransomware is written in C++ and compiled using MSVC++ 2015.
Pay2Key’s code is based on Object-Oriented Programming that implements well-designed operation classes and third-party libraries.
Interestingly, it appears that older variants of the ransomware were called “Cobalt” (not related to the infamous Cobalt Strike).
The identity of Pay2Key’s author is currently unknown. Inconsistent English wording within various strings suggests that the attackers are not native English speakers.
Pay2Key Operations
Pay2Key ransomware is an efficient ransomware threat, capable of corrupting the target network and encrypting the data stored on connected devices within hours. The ransomware uses clever tricks to stay under the radar while the encryption procedure runs in the background.
To camouflage their malicious operations and reduce their detectable network footprint, Pay2Key operators channel all C&C (command and control) communication through a pivot point, set on the local network.
Pay2Key’s encryption appears to follow a standard combination of AES and RSA algorithms, which, so far, cannot be broken.
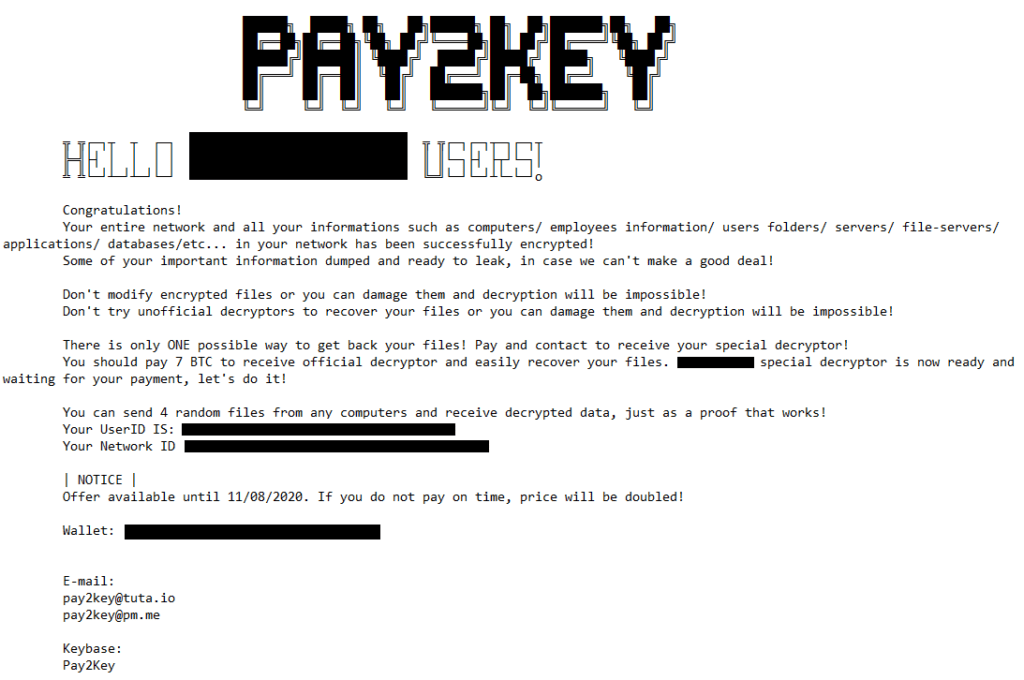
Upon completing the infection phase, the threat will present its victims with a customized ransom note, demanding a ransom between 7 to 9 BitCoin (about $110,000 to $140,000), which is a relatively low ransom for a threat of this caliber.
Figure 1: Ransom Note





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.