The ColdLock attacks started this month and the malware analysis showed similarities with the LockerGoga, Freezing, and EDA2 educational ransomware kit. According to the security firm Trend Micro, this malware is considered as rather destructive since the ColdLock ransomware encrypts users’ databases and email servers.
ColdLock's Distribution Vector Is Currently Unknown
At this point, there is no information about the initial arrival vector of ColdLock into the victim’s network. Nevertheless, security researchers say that cybercriminals have gained access to several Taiwanese organization’s Active Directory servers.
Yet the malware analysts managed to set Group Policies leading to the ransomware file that was downloaded and run onto computers within the affected domain.
The ColdLock payload arrives as a ,NET executable (as a .DLL file) and uses PowerShell reflective loading to run this file.
ColdLock Encryption Routine
The ColdLock ransomware performs some preparatory routines before encrypting users’ files. First, it terminates the Exchange mail server and the Outlook process, as well as services used by different databases such as MariaDB, MSExchangeIs, MySQL, and Oracle Service.
After terminating these processes ColdLock checks the Windows version running on the system. If it is Windows 10, the ransomware performs several Windows 10-specific routines. Among these is disabling the push notifications as well as Windows Defender and the ability to send malware samples to Microsoft.
The infection avoids encrypting the following directories:
- %System Root%\Program Files
- %System Root%\Program Files (x86)
- %System Root%\ProgramData
- %System Root%\Users\all users
- %System Root%\Users\default
- {malware directory}
- {drive letter}:\System Volume Information
- {drive letter}:\$Recycle.bin
At the same time, the following directories would still be encrypted:
- %System Root%\ProgramData\Microsoft\Windows\Start Menu
- %System Root%\Program Files\Microsoft\Exchange Server
- %System Root%\Program Files (x86)\Microsoft\Exchange Server
- Directories in Program Files, Program Files (x86), and ProgramData containing SQL, MariaDB, or Oracle strings.
Whether files in other directories are encrypted depends on a set of three conditions:
- Number of files on the target directory is less than 100
- Directory’s last write time is newer than January 1, 2018.
- The directory name should not contain any of the following strings:
-
- .git
- appdata
- cache
- image
- lib
- log
- logs
- microsoft
- reference
- res
- resource
- script
- setup
- skin
- temp
- theme
- third_party
- thirdparty
If all of the above conditions are met, the ransomware will encrypt all the files in the given directory except those with the following extensions:
-
- .avi
- .dll
- .gif
- .iso
- .m2ts
- .mkv
- .mov
- .mp3
- .msi
- .ocx
- .tmp
- .wmv
If some of the conditions are not met, the ColdLock ransomwere will only encrypt files with the following extensions:
- .7z
- .aspx
- .bak
- .cpp
- .csv
- .doc
- .docx
- .gz
- .hwp
- .java
- .jpg
- .jsp
- .lnk
- .odt
- .one
- .php
- .ppt
- .pptx
- .pst
- .rar
- .sh
- .sql
- .txt
- .xls
- .xlsx
- .xml
- .zip
During the encryption process, the AES function is in CBC mode. The needed key and initialization vector (IV) are generated using salt and secret key. Then, the former is embedded in the code, and the latter is generated dynamically using the SHA-256 hash of a randomly generated 32-byte long string. After that, this is encrypted using a hard-coded public RSA key and embedded in the ransom note.
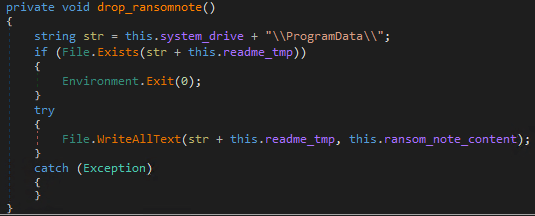
When the encryption process is completed, the encrypted files receive the .locked extension and a ransom note is kept in different locations on the system, such as:
- %Desktop%\How To Unlock Files.Txt
- %System Root%\ProgramData\readme.tmp
- %User Startup%\How To Unlock Files.Txt
- {Encrypted Drive}:\How To Unlock Files.Txt
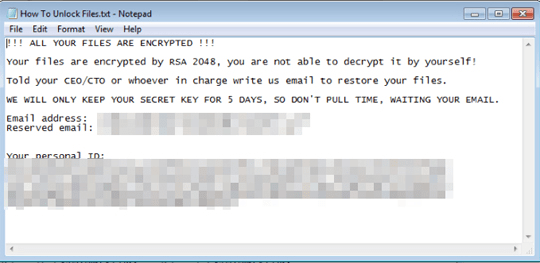
As shown in Figure 4 below, the ransom note content is similar to other ransomware notes.
Figure 4: Image: ColdLock ransom note
To Instill a sense of urgency, the cybercriminals warn victims that they will only keep the key needed to decrypt the files for five days. Source: Threat Post
Protect your PC from ColdLock
To protect your computer from ColdLock and other ransomware infections, you should use legitimate antimalware software and keep it enabled at all times. Also, make regular backups of your data and follow the experts’ advice listed below:
- Do not open emails sent by unknown or suspicious-looking senders.
- Be aware that malware can be distributed not only via executive files but also by different types of documents, images, etc. For that reason, security experts recommend scanning the downloaded files with reliable antivirus software before opening them.
- Do not try to obtain copyrighted materials for free! Cybercriminals often use them as a trap for computer users. Downloading “cracked” software can result in data loss which will be impossible to fix.
In any case, you should be aware that malware infections are very dangerous and you’d better protect your system before it’s too late.





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.