
The National Security Agency (NSA) and Microsoft have come together to warn Microsoft Windows Administrators of a potential vulnerability within Windows 10. The NSA urges everyone who uses Windows to ensure they are using an updated and patched system in the face of looming cyber threats.
Microsoft themselves have issued several warnings about the importance of installing patches recently. The warnings are related to a potential protocol vulnerability in earlier versions of Windows in particular. Microsoft warns that the vulnerability could be “wormable”; meaning that it could spread without any direct action from users. These computer worms have done irreparable damage to computer systems in the past, and that is why the NSA and Microsoft are so adamant about everyone getting protected as soon as possible.
The latest vulnerability – CVE-2019-0708 (called “BlueKeep” – is a vulnerability in the Remote Desktop Protocol (RDP). The vulnerability can be found on Windows 7, Windows XP, Server 2003 and 2008. Microsoft has pushed out a patch for the vulnerability, but millions of systems are still at risk because they haven’t been patched.
Figure 1.1: BlueKeep Exploits Diagram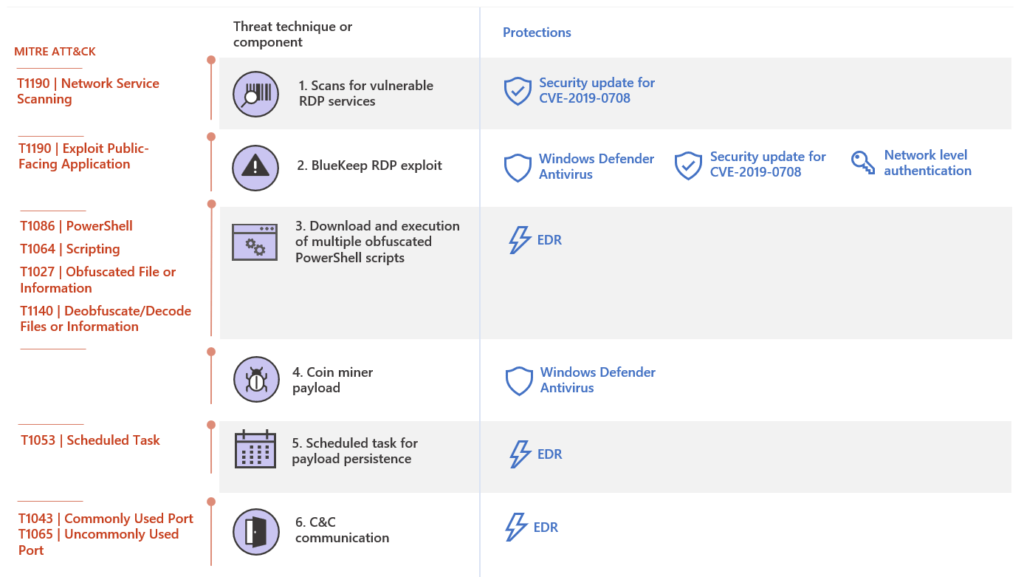
Diagram showcasing the various ways hackers use BlueKeep to compromise a system. Source: Microsot.com
Hackers exploit this kind of vulnerability by using software code that specifically targets the vulnerability. They could potentially use the exploit for denial of service attacks. It won’t be long at all before remote exploitation code becomes available to use the vulnerability for malicious acts. The NSA is concerned that malicious hackers could use the vulnerability to create ransomware or compile it with exploit kits that contain other exploits to make them more dangerous.
The NSA urges everyone to spend the resources and time necessary to update their systems and run supported operating systems, not just big-name corporations and government agencies. There are some things that administrators can do to protect their system during the patching process;
- Block TPC Port 3389 at firewalls, especially perimeter firewalls that connect to the internet. The port is used for RDP protocol and so blocking it can potentially block the exploit.
- Enable Network Level Authentication. This security step requires an attack to have valid credentials to authorize remote code.
- Disable Remote Desktop Services if they aren’t needed. Given that the exploit uses Remote Desktop services, the easiest way to prevent it would be to block remote desktop if no one is using it anyway.
Update: Another Windows 10 Vulnerability Discovered
Things are looking even worse for Windows 10 with the discovery of a new vulnerability. This latest vulnerability (CVE-2020-0601) affects the cryptographic functionality of Windows 10 operating systems on both Windows-32 bit and x64-based architectures along with specific versions of the Windows Server. It basically exists within the cryptographic programming interface (or CryptoAPI/Crypto32.dll), and it affects how the system validates elliptic curve cryptography (EEC) certificates.
What the vulnerability does is allow cybercriminals to create fake websites that look just like the real thing by spoofing digital certificates. The world got a fantastic example of how it works thanks to Saleem Rashid. The security researcher tweeted out versions of NSA.com and GitHub.com that he had created that Rickrolled users. He did it by causing Edge and Chrome web browsers to spoof the websites despite their HTTPS verification that should make such things impossible.
CVE-2020-0601 pic.twitter.com/8tJsJqvnHj
— Saleem Rashid (@saleemrash1d) January 15, 2020
These “attacks” are humorous, of course, but they show just how serious this problem could become if left unchecked. By spoofing the digital certificate and exploiting CryptoAPI as it does, it means anyone online can pretend to be someone else – including a governmental or other official authority.
The CryptoAPI is a vital part of the Microsoft Windows operating system. CryptoAPI allows developers to secure software through cryptography. It’s also the system responsible for validating the legitimacy of websites and software, which it does by using X.509 certificates (SSL/TLS certificates, email signing certificates, code signing certificates, etc.). It basically causes problems with the part of the operating system responsible for determining if an application or email is secure and whether or not a computer (and by extension, a user) has a legitimate secure connection to a genuine website.
The new vulnerability allows for threat actors to bypass the trust store by using forged and spoofed EEC certificates (which makes something appear to be signed by a trusted authority or organization). It means that users would download compromised malicious software without realizing it because their computer tells them it comes from a trusted source. There’s no reason for them to be suspicious.
The vulnerability could also cause other potential issues according to the Cybersecurity and Infrastructure Security Agency (CISA):
“This could deceive users or thwart malware detection methods such as antivirus. Additionally, a maliciously crafted certificate could be issued for a hostname that did not authorize it, and a browser that relies on Windows CryptoAPI would not issue a warning, allowing an attacker to decrypt, modify, or inject data on user connections without detection.”
-CISA statement on CVE-2020-0601 vulnerability.
This isn’t to say that ECC isn’t secure anymore. The vulnerability has nothing to do with the integrity of these ECC certificates. What it does is show how flawed the Windows cryptographic application programming interface is. It highlights an issue in the validation process that could put millions of users in danger.
The vulnerability is a flaw to do with Windows CryptoAPI. It does not mean that there is anything inherently wrong with ECC certificates. If you are using ECC certificates still, then it won’t impact the actual security of your actual certificates. It just means that someone else can copy your certificates and pretend to be you.
Microsoft has released a patch to the vulnerability to ensure that Windows CryptoAPI works appropriately. It is recommended that users update their machines as soon as possible.





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.