Sodinokibi (also known as REvil or Sodin) is a ransomware threat that was discovered in April 2019. Although Sodinokibi acts like a typical ransomware program, it is a completely new malware strain that has already extensive use by cybercriminals.
Table of Contents
What is Sodinokibi Ransomware
Sodinokibi was first used by hackers about a year ago in a cyberattack that exploited a software vulnerability in Oracle WebLogic Server. The exploit allowed the remote execution of code without any of the otherwise required authentication credentials. Although the malware developers did not provide an official name to the threat, security researchers have dubbed it Sodinokibi.
Generally, there is nothing new in using the Ransomware-as-a-Service (RaaS) model, apart from the fact that Sodinokibi is backed up by an underground affiliate program with quality at its core. By now, the threat has taken thousands of high-profile victims such as healthcare facilities and local governments, and its creators’ toolkit has expanded far beyond software vulnerabilities.
How is Sodinokibi Ransomware Distributed
Just like other ransomware threats, Sodinokibi is usually spread through malicious spam campaigns, fake software updaters, untrusted file sharing websites , software 'cracking' tools, and Trojans.
- Spam campaigns - Threat actors send emails with malicious attachments (or web links that download malicious files) in them such as Office documents, PDFs, archive files, executable files, or JavaScript files. When the victim opens the file, embedded code is executed that infects the system with the malware.
- Untrusted file sharing websites - Hackers distribute ransomware by hosting malicious files across questionable file sharing services such as Peer-to-Peer networks, unofficial websites, free file hosting, freeware websites, third party downloaders, etc.). The malicious files are disguised as legitimate and when executed, they infect systems with malware.
- Fake software updaters – Malware can infect systems either by exploiting flaws of outdated programs installed on a targeted machine or by installing malicious software instead of legitimate updates. Untrustworthy sources for software downloads include be Peer-to-peer networks, freeware download, third party downloaders, free file hosting web pages, etc. Hackers use them as tools to host malicious files and disguise these files as legitimate. When downloaded and opened, they infect victims' computers with malicious software.
- Software 'cracking' tools - Some people use unofficial programs to bypass paid activation of licensed software. Unfortunately, these tools are dangerous as hackers often use them for distributing malware.
- Trojans - Cybercriminals are well aware that if installed onto a system, trojans can cause severe chain infections. Trojans can be used to either drop a malware payload, or leave a backdoor to the system for future infections. For that reason, hackers often use programs of this type for installing malware.
How Does Sodinokibi Ransomware Work
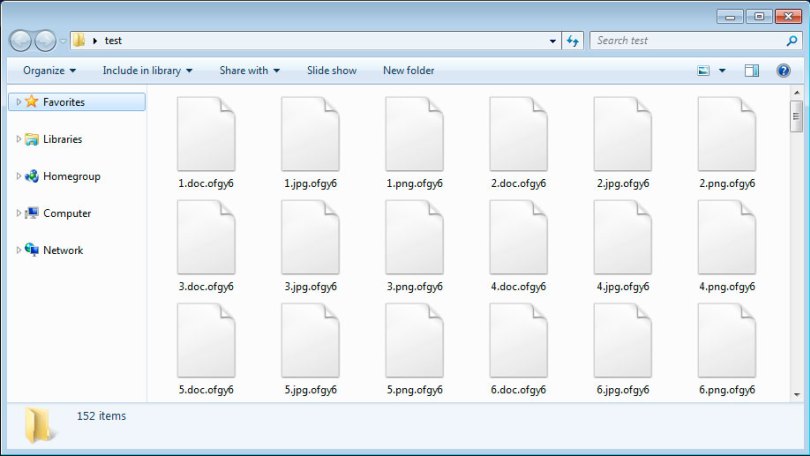
After being installed, Sodinokibi begins the encryption process and drops ransom messages in each folder that containing encrypted files. The names of the text files depend on the extensions added to the encrypted files. For instance, if the extension is ".686l0tek69", the encrypted file is renamed from "1.jpg" to "1.jpg.686l0tek69", and the ransom message is called "686l0tek69-HOW-TO-DECRYPT.txt".
Figure 1: Image: Files Encrypted by Sodinokibi Ransomware
Sodinokibi appends the ".686l0tek69" extension to all locked files and adds a ransom note with instructions on how to decrypt them. Source: howtofix.guide
Sodinokibi ransomware encrypts all files with the following extensions:
.jpg, .jpeg, .raw, .tif, .gif, .png, .bmp, .3dm, .max, .accdb, .db, .dbf, .mdb, .pdb, .sql, .dwg, .dxf, .cpp, .cs, .h, .php, .asp, .rb, .java, .jar, .class, .py, .js, .aaf, .aep, .aepx, .plb, .prel, .prproj, .aet, .ppj, .psd, .indd, .indl, .indt, .indb, .inx, .idml, .pmd, .xqx, .xqx, .ai, .eps, .ps, .svg, .swf, .fla, .as3, .as, .txt, .doc, .dot, .docx, .docm, .dotx, .dotm, .docb, .rtf, .wpd, .wps, .msg, .pdf, .xls, .xlt, .xlm, .xlsx, .xlsm, .xltx, .xltm, .xlsb, .xla, .xlam, .xll, .xlw, .ppt, .pot, .pps, .pptx, .pptm, .potx, .potm, .ppam, .ppsx, .ppsm, .sldx, .sldm, .wav, .mp3, .aif, .iff, .m3u, .m4u, .mid, .mpa, .wma, .ra, .avi, .mov, .mp4, .3gp, .mpeg, .3g2, .asf, .asx, .flv, .mpg, .wmv, .vob, .m3u8, .dat, .csv, .efx, .sdf, .vcf, .xml, .ses, .qbw, .qbb, .qbm, .qbi, .qbr , .cnt, .des, .v30, .qbo, .ini, .lgb, .qwc, .qbp, .aif, .qba, .tlg, .qbx, .qby , .1pa, .qpd, .txt, .set, .iif, .nd, .rtp, .tlg, .wav, .qsm, .qss, .qst, .fx0, .fx1, .mx0, .fpx, .fxr, .fim, .ptb, .ai, .pfb, .cgn, .vsd, .cdr, .cmx, .cpt, .csl, .cur, .des, .dsf, .ds4, , .drw, .eps, .ps, .prn, .gif, .pcd, .pct, .pcx, .plt, .rif, .svg, .swf, .tga, .tiff, .psp, .ttf, .wpd, .wpg, .wi, .raw, .wmf, .txt, .cal, .cpx, .shw, .clk, .cdx, .cdt, .fpx, .fmv, .img, .gem, .xcf, .pic, .mac, .met, .pp4, .pp5, .ppf, .nap, .pat, .ps, .prn, .sct, .vsd, .wk3, .wk4, .xpm, .zip, .rar.
After encrypting users' files, Sodinokibi drops a ransom message to explain to the victims that they can decrypt their files only by following the malware developers' instructions. Instead of putting the instructions in a ransom note, the attackers direct their victims towards two websites - a .onion site hosted on the TOR network and one on the public part of the Internet at the domain "decryptor[.]top."
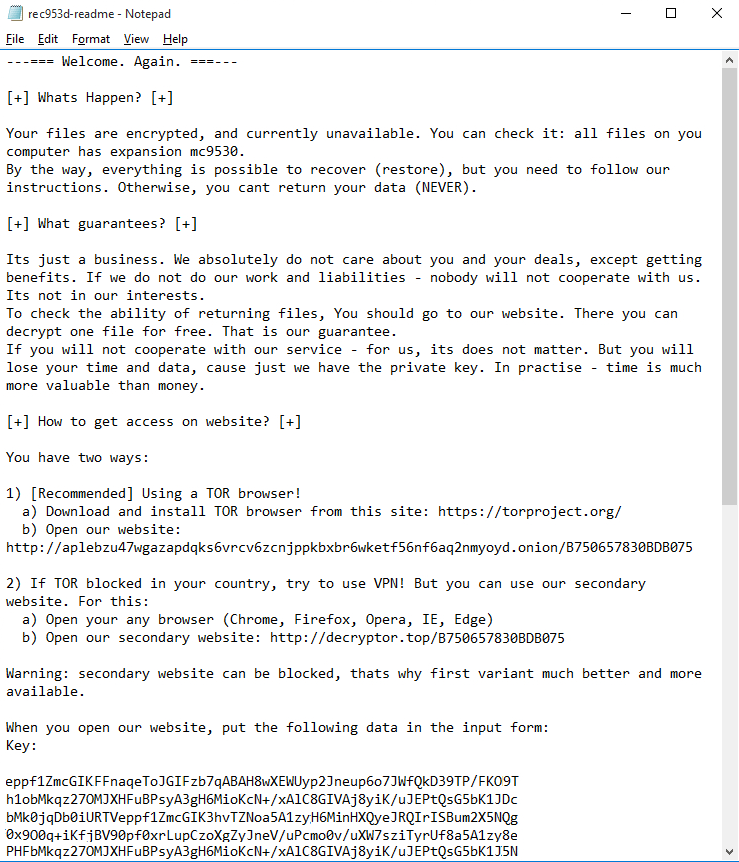
To release their files, the affected users must follow the instructions laid out in the ransom message as shown in Figure 2 below.
Figure 2: Image: Sodinokibi Ransom Message
Sodinokibi's ransom note instructs the user to visit a webpage in the deep web by using the TOR browser to prove the attacker's ability to decrypt the files. Source: geeksadvice.com
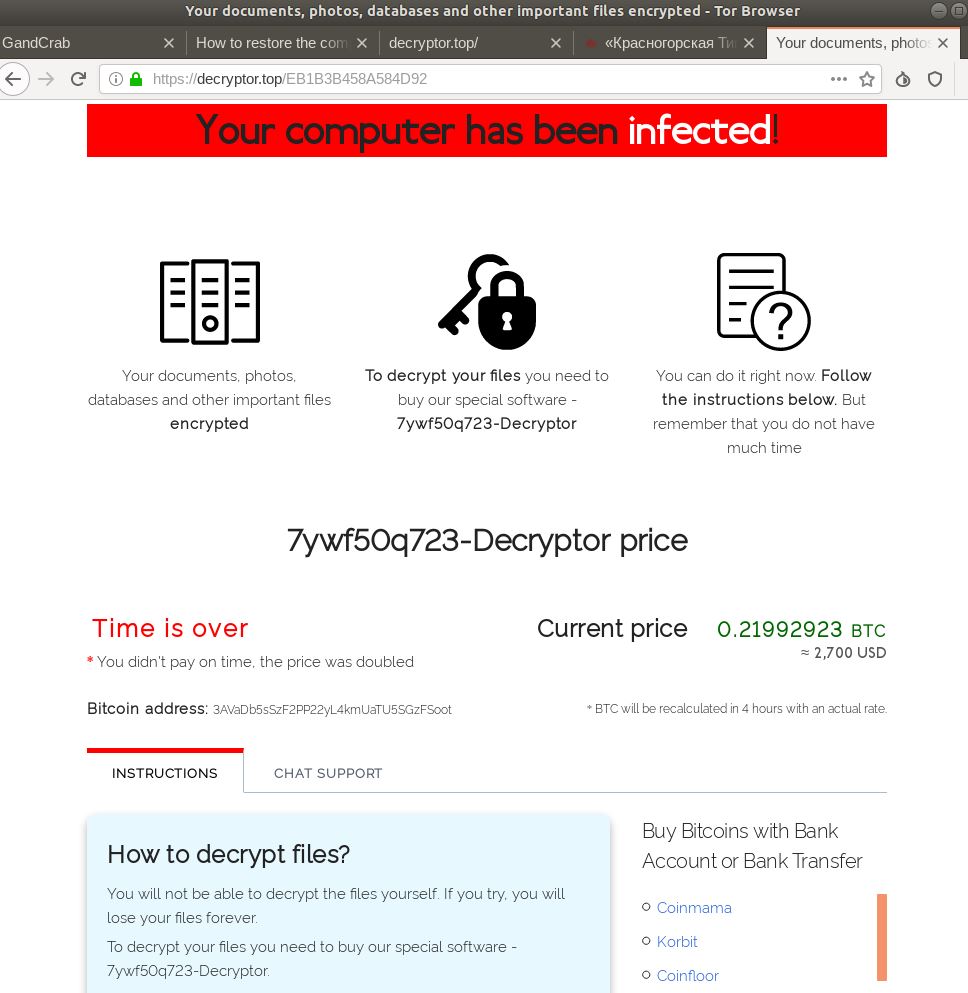
To access the websites provided by the attackers, victims must provide a unique key that written in the victim's ransom note. After entering the code, users will be taken to the following landing page that will show the specific extension ID code and a countdown timer showing that in two days the ransom payment will be doubled - from $2500 to $5000, payable in the Bitcoin cryptocurrency. The Bitcoin/USD rate is recalculated every 3 hours and the numbers are updated.
Figure 3: Image: Sodinokibi Decryptor Cost
Hackers try to instill a sense of urgency in the user by threatening to double the ransom cost. Source: https://krebsonsecurity.com/
Victims of Sodinokibi should be aware that this ransomware is capable of utilizing "cmd.exe" to execute the vssadmin utility to prevent decrypting the encrypted data via the default Windows backup mechanism. Sodinokibi also uses the following commands to delete the Shadow Volume Copies of the affected files and disable the Windows startup repair:
C:\Windows\System32\cmd.exe" /c vssadmin.exe Delete Shadows /All /Quiet & bcdedit /set {default} recoveryenabled No & bcdedit /set {default} bootstatuspolicy ignoreallfailures
Cases Involving Sodinokibi Ransomware Just Keep Coming
Unfortunately, Sodinokibi ransomware doesn't show any signs of slowing down its assault . On the contrary, after the massive attack against the foreign exchange company Travelex in 2019, the threat continues its rage at full speed.
After hitting a New Jersey Synagogue in January, this year, the criminals behind Sodinokibi said they would "keep promises" as they uploaded links to approximately 337MB of allegedly stolen victim files on a Russian malware forum.
"This is a small part of what we have. If there are no movements, we will sell the remaining, more important and interesting commercial and personal data to third parties, including financial details..." Statement by Cyberattackers
The criminals said the stolen data belongs to Artech Information Systems whose website was down at that time and any information on the issue was missing.
Meanwhile, security researchers say that the practice of using stolen data as leverage is going to get worse and Sodinokibi is just one of the numerous active ransomware operators currently operating.
Sodinokibi Ransom Payments Switched to Monero to Hide Money Trail
A report has emerged that says the hacking group behind Sodinokibi posted on a hacker forum that they would make the switch from Bitcoin to Monero. The cybercriminals noted that the move was to make it harder for the authorities to track payments sent to them. As per the announcement;
“In this regard, we inform you that after a while, the BTC will be removed as a payment method. Victims need to begin to understand the new cryptocurrency, as well as other interested parties who work with us.”
The Sodinokibi payment website has already started to deter people from using bitcoin payments. The group has done this by charging 10% more for bitcoin ransoms than Monero ransoms. The group is looking for partners who can offer discounts to users who make Monero payments too.
Cybersecurity experts say that the use of anoncoin for ransomware payments is surprisingly uncommon. Researchers also believe that other ransomware actors could follow suit and switch to other cryptocurrencies given that bitcoin isn’t as anonymous as some people think.
There have been several instances of groups demanding ransom payments in alternative currencies, but this is the first time a significant group has switched away from Bitcoin. Criminal enterprises, like any other kind of enterprise, will adopt strategies that have worked for others. If the Sodinokibi group sees success, it’s only natural that other groups will make the switch too.





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.