
With the Oscars finally over, many viewers online to catch up on the best movies of 2019. Online scammers are very much aware of this trend and have launched a phishing campaign that exploits people’s craving to watch these award-winning movies.
An Opportunistic Spearphishing Campaign
Cybersecurity researchers warn that hundreds of online scams are taking advantage of the new trend, luring users with promises for free streams of the hottest Hollywood films of the year. The cybersecurity company Kaspersky found a total of 925 malicious files that are presented as free, Oscar-winner and nominee films. The phishing campaign spreads infected files through spoofed websites that trick users into giving their credentials or downloading malware.
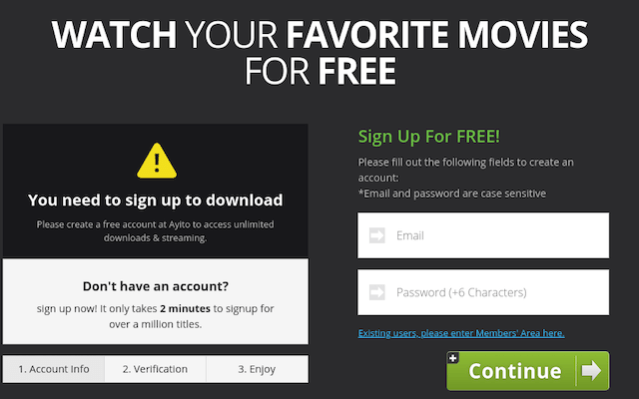
Figure 1: Phishing Website Example
One of the many phishing websites that dupe users by promising free Oscar movie streams Source: backendnews.net
Hundreds of these phishing websites that offer free movie streams have been spotted on the web by cybersecurity analysts. By luring their visitors into filling fake surveys or subscribing to a newsletter, these malicious websites harvest data such as contact details, email addresses, phone numbers, and even credit card details. Researchers also warn that some webpages also push malicious downloads. On the pretext of having to update your software or installing a necessary app/codec pack, these malicious websites push adware and other malware.
And it's not just malicious websites. The crooks turn to social media as well. Fake Twitter accounts spread malicious links that redirect to phishing websites and dangerous pages that promote malware.
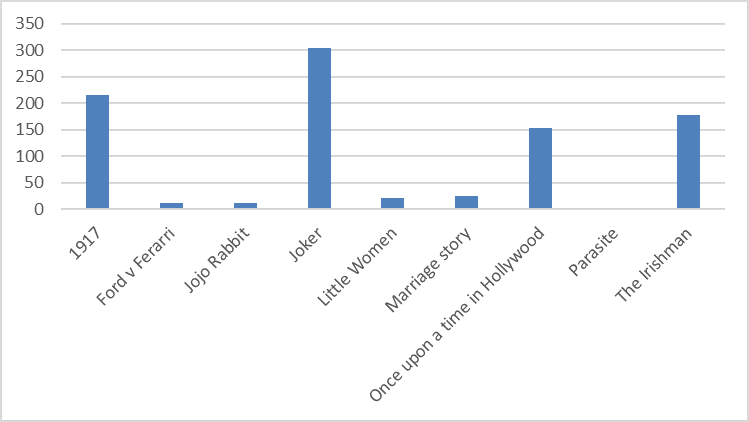
The company reports that "Joker" was the winner of the cyber-crime award, with researchers detecting 304 malicious files named after the blockbuster. A close second nominee for the most malicious files is the film "1917" with 215 malicious files. Lastly, "The Irishman" takes the third place with 179 associated malicious files.
Interestingly enough, the Korean movie "Parasite," which won the Academy Award for best picture, is not on the criminals' list. It won't be a surprise when this changes, though. Given how cybercriminals love to capitalize on the current trends, It's just a matter of time for malicious files associated with the Oscar-winning title to emerge.
Figure 2: Number of Infected Video Files
Most popular malicious files disguised as movies. Joker tops the amount of downloads with “1917” and “The Irishman” closely behind. Source: Kaspersky
Researchers recommend vigilance
Users should not allow themselves to get caught up in the buzz. Websites that promise early or free access in exchange for surveys are usually bad news. If a title is not available on an official streaming platform, but it's offered for free on a small, unknown website, chances are that it is a trap.
When it comes to downloading a movie, users should first make sure that the source is legitimate. A good first indication of a safe website is the URL of the page. It should start with "https" which is much safer data encryption than the standard "http" variant. A quick check of the online reviews could also help mitigate the risk of falling into online traps. One, however, should always keep in mind that there are myriads of fake reviews. Therefore, checking the website's registration data is essential.
Researchers also highlight the importance of the file format. If you download a movie, the file should have an extension that is associated with video formats such as .avi, .mp4, or .mkv. Video files that end with .exe should definitely to be avoided.





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.