Shootlock is a new Makop ransomware variant that encrypts users’ personal data and demands a ransom payment to regain access to their files. The file-encrypting malware is highly destructive as it uses a strong encryption algorithm to lock the victims’ files and makes them unable to open them again.
Table of Contents
How Does Shootlock Ransomware Infect Computers
Ransomware and other malware are usually distributed using spam campaigns, untrusted sources for download, fake software updaters, unofficial software activation tools, and trojans.
- Spam campaigns - The attackers send emails with malicious attachments (or web links that download malicious files) in them. Usually, hackers attach files like Microsoft Office, PDF documents, archive files, executable files, or JavaScript files. Once the victims open these files, the malware will be installed on their computers.
- Untrusted sources for download - Hackers distribute ransomware by hosting malicious files in various unsecure sources such as Peer-to-Peer networks, unofficial websites, free file hosting, freeware websites, third party downloaders, etc.). The malicious files are disguised as legitimate and when executed, they infect systems with malware.
- Fake software updaters – These updaters spread malware by infecting systems either by exploiting flaws of outdated programs installed on a targeted machine or by installing malicious software instead of legitimate updates.
- Unofficial software activation tools - Some people use unofficial programs to bypass paid activation of licensed software. Unfortunately, these tools are dangerous as hackers often use them for distributing malware.
- Trojans - Cybercriminals are well aware that if installed onto a system, trojans can cause severe chain infections. For that reason, hackers often use programs of this type for installing malware.
How Does Shootlock Ransomware Operate
As soon as Shootlock infects the targeted machine, it will scan it for images, videos, and other files such as .doc, .docx, .xls, .pdf, etc. Once detected, the ransomware will encrypt these files by changing their extension to “.shootlock”, so that users are no longer able to access them. For instance, the file "1.jpg" would turn into something similar to "1.jpg.[E38D7F03].[n0pr0blems@protonmail.com].shootlock", as shown in Figure 1 below.
After the encryption process is completed, the Shootlock ransomware will display the "readme-warning.txt" ransom note on the desktop. The note contains instructions on how the victim to contact the malware creators via the n0pr0blems@protonmail.com and troubleshooter@cock.li email addresses and get further details on paying the ransom.
Figure 2: Image: Shootlock Ransom Note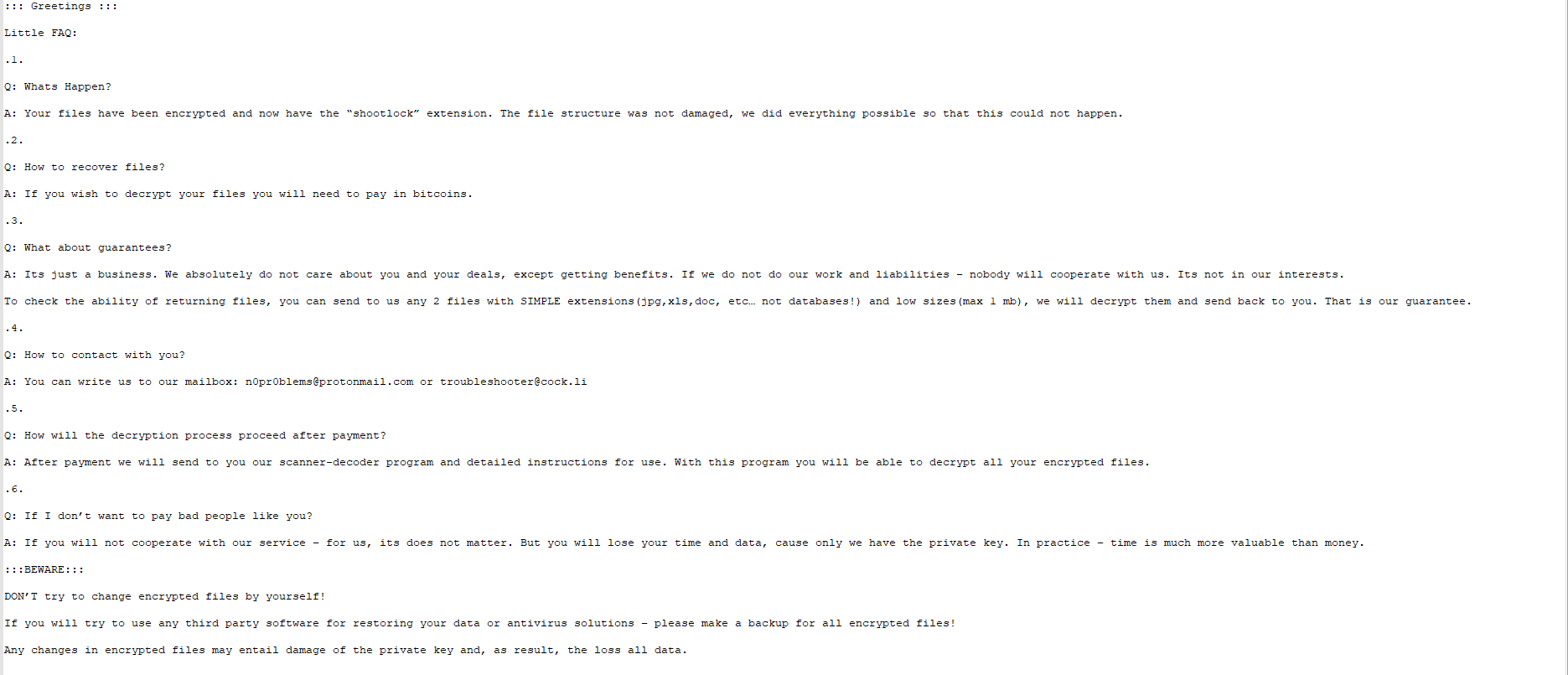
Shootlock ransom note explaining to the victim what has happened to their system and how to pay the criminals to decrypt it.
The text in the ransom note is presented in a Q&A (question and answer) format. Basically, the attackers inform the victim that they should make a ransom payment in BitCoins or any other crypto-currency to regain access to their files.
To prove that the decryption is possible, the creators of Shootlock offer to decrypt two infected files for free, however, that should be less than 1 MB in size and can not be databases.
The victims are promised to be sent the appropriate decryption tool after and only if they fulfill the attackers’ conditions. The end of the ransom note warns users that modifying the files and/or using anti-virus software can lead to permanent data loss.
How to Remove Shootlock Ransomware
The Shootlock ransomware can delete shadow volume copies of the infected files, which makes restoring the encrypted data much more difficult, Therefore, security researchers advise malware victims to make regular backups of their files and install legitimate anti-virus software on their computers.
Also, if you find out that Shootlock has infected your machine, you can contact the following websites to report the malware attack and receive expert advice:
- In the United States, go to the On Guard Online website.
- In Australia, go to the SCAMwatch website.
- In Canada, go to the Canadian Anti-Fraud Centre.
- In France, go to the Agence nationale de la sécurité des systèmes d’information.
- In Germany, go to the Bundesamt für Sicherheit in der Informationstechnik website.
- In the United Kingdom, go to the Action Fraud website.
- In Ireland, go to the An Garda Síochána website.
- In New Zealand, go to the Consumer Affairs Scams website.





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.