Nearly two years after the launch of their malware-dropping botnet service Black Rose Lucy, an unnamed Russian-speaking team is trying to expand their malware-as-a-service (MaaS) business, tempting potential clients with an upgraded version of Lucy Android malware that is capable of making calls, exporting a list installed apps, deleting encryption keys, even running remote shell commands on the target device.
Researchers report that the latest version of Lucy appears to have received quite the number of upgrades. The variant is offered as a malware on-demand service, granting its operators the ability to execute various operations on compromised devices. Some of these activities include:
- Calling phone numbers
- Encrypting files
- Decrypting files
- Deleting encryption/decryption keys
- Deleting itself from the device
- opening a remote shell on the device
According to the cybersecurity company Check Point, the current malware campaign targets victims in former Soviet states. Over 80 malware samples distributed via instant-messaging apps and social media links.
The latest version of the Lucy malware variant employs harmless-looking video player apps that corrupt devices by abusing the Android Accessibility service. Once it gets on a device, Lucy will encrypt files and display a ransom note in the browser window, asking for $500. Unlike most ransomware threats, Lucy doesn’t demand cryptocurrencies such as Bitcoin and Monero, but instead asks the victim to provide their credit card details.
To get the victim to cooperate and pay, Lucy displays a message that is purportedly sent from the Federal Bureau of Investigation (FBI) and accuses the victim of watching adult content on their mobile device. This simple sextortion scheme plays on the common fear of legal consequences of visiting adult websites and storing pornographic content. The victim is warned that a picture of their face has been taken and uploaded to the FBI’s cyber crime data center. The message instructs the victim to pay the requested “fine” within three days, otherwise the fine tuples.
Figure 1: Screenshot of the ransom note
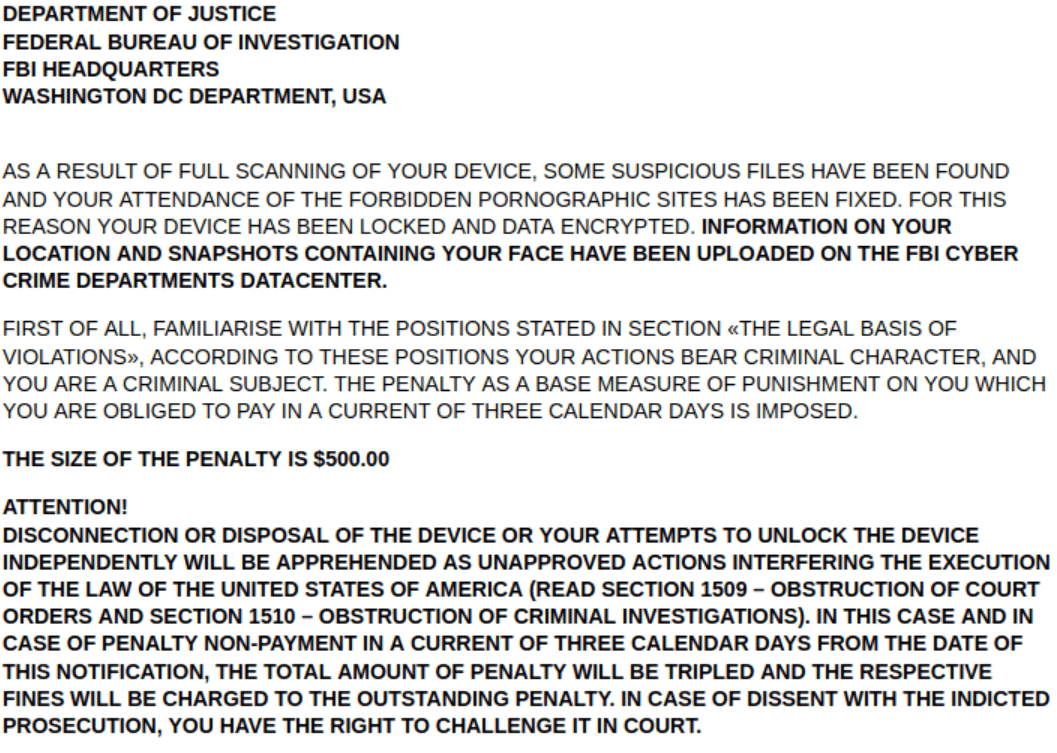 Caption:The ransom note attempts to intimidate victims into paying the ransom by stating suspicious pornographic files have been found. Source: Check Point Research
Caption:The ransom note attempts to intimidate victims into paying the ransom by stating suspicious pornographic files have been found. Source: Check Point Research
Lucy Malware’s Distribution Vector
Researchers report that Lucy infects its victims by exploiting the Android Accessibility service. This is not the first instance of this service being abused by malware; The credential-stealing trojan TrickMo RAT was discovered to exploit the service to infect devices and authorize fraudulent bank transactions.
The Android Accessibility feature is designed to help people with special needs to use their phones. Instead of navigating through a series of settings, the service mimics screen clicks and automates interactions with the device. However, if a malicious app manages to get permission to use the service, it can escalate privileges and infect the device with dangerous malware.
Once Lucy gets on an Android device, it will check if the target device is located in the former Soviet state. The malware will register a receiver called “uyqtecppxr,” which will check the country code of the target device by running BOOT_COMPLETE and QUICKBOOT_POWERON.
The malware will then gain control of the device by opening a dialog window that asks the victim to turn on Streaming Video Optimizations (SVO), which will supposedly allow a video to be played on the phone. If the victim falls into the trap, the malware gets permission to exploit the accessibility service.
Figure 2: A dialog pop-up that prompts the user to enable SVO

Caption: In this image, we can see the deceptive dialog window that tricks the victim into enabling the accessibility service. Source: Check Point Research
After gaining access, the malware will then run a malicious service inside the MainActivity module, which will then register a BroadcastReceiver that will be called by the action.SCREEN_ON command, which will then call itself. This operation will access the ‘WakeLock’ service (a feature that keeps the device’s screen on), as well as the ‘WifiLock’ service, which keeps the WI-FI on.
The malware will also establish a communication channel with a C&C server. Unlike previous versions of the threat, the latest variant uses a domain for its C&C instead of IP addresses. This way, if the server gets taken down, it can quickly get restored and maintain stable communication.
Lucy has four encrypted C&C servers in its code and rotates between them by calling a different API with a different URI. According to researchers at Check Point, the C&Cs are “held as a long string which is a concatenation of all C&Cs hardcoded in the malware’s code, followed by a bulk of unused data.”
File encryption
Lucy will first try to discover all directories on the system. In case of failure, it will look for the “/storage” folder, but if that also fails, the malware will search for the “/sdcard” directory.
Figure 3: Lucy Scanning for Directories.
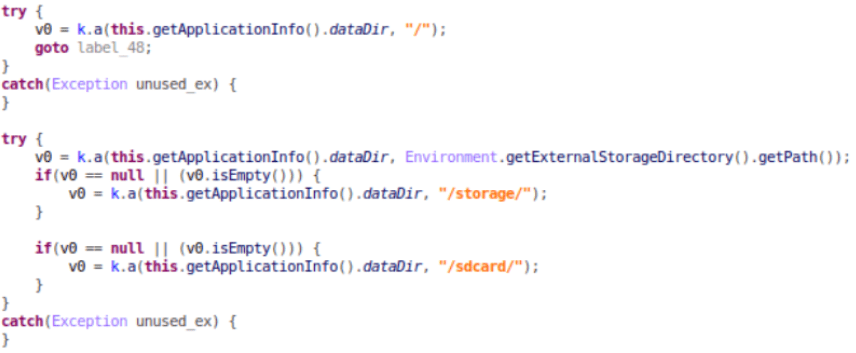 Caption: In this image, we can see the malware’s attempt to obtain information about all directories of the victim’s device, including external sources such as SD cards. Source: Check Point Research
Caption: In this image, we can see the malware’s attempt to obtain information about all directories of the victim’s device, including external sources such as SD cards. Source: Check Point Research
Before it starts the encryption processes, the malware will make sure that the files can be encrypted/decrypted. After performing this check, Lucy malware corrupts the data in selected storage locations and verifies the success of the operation when it’s completed. Researchers point out that Lucy doesn’t discriminate between files, as long as they are encryptable.
Interestingly, during the encryption process, the malware uses an AES algorithm to generate a false encryption key. Researchers argue whether that action was a decoy move, made to hinder the malware analysis, or whether it was a careless mistake.
The actual encryption key is constructed of data from the first segment of the “SecretKeySpec’ and of a string called “Key,” which is fetched from SharedPreferences.
These keys, together with the target file and a Boolean variable, are later joined as parameters and used by the malware to switch between encryption and decryption.
Figure 4: Lucy’s Encryption/Decryption Function
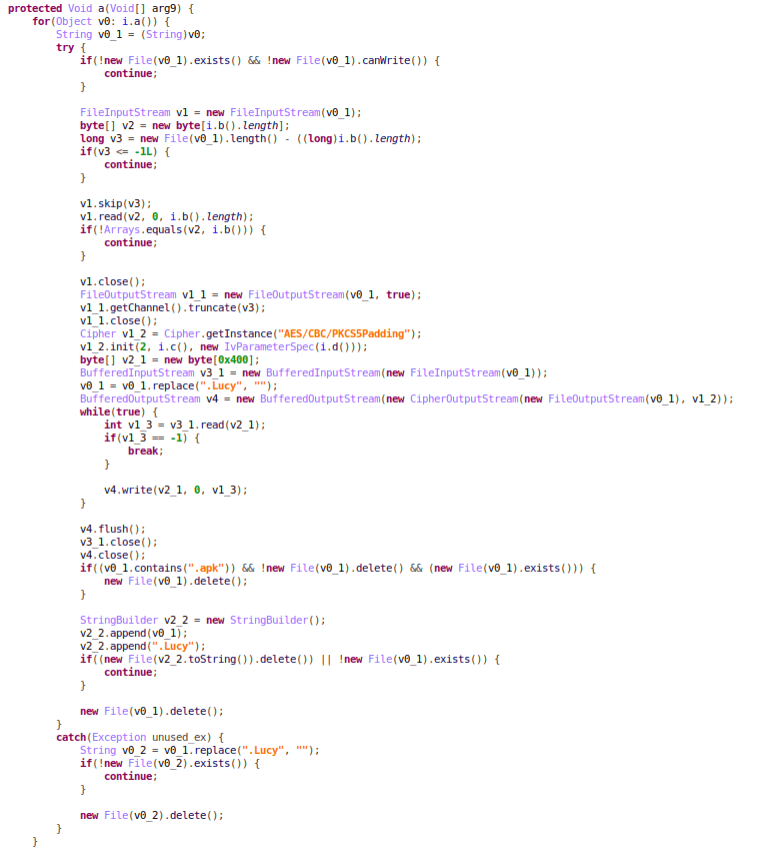 In this image, we can see the malware to encrypt/decrypt files. Source: Check Point Research
In this image, we can see the malware to encrypt/decrypt files. Source: Check Point Research
Once the encryption operation is finished, Lucy will run additional checks to make sure that all files are corrupted successfully. It will then display its ransom note in the browser window.
According to the research, following a decryption process, Lucy will send logs, which inform that the fires were successfully restored, and will then run a command to delete itself.





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.