The infamous AZORult malware is making a comeback with yet another social engineering attack. Researchers at Kaspersky report that a new malvertising campaign redirects traffic to a spoofed ProtonVPN website that spreads the malware.
The malvertising attack started in November 2019, when the attackers listed the "proton[.]store" website on a Russian-based register. Upon visiting the malicious website, which is an HTTrack copy of the original ProtonVPN website, the unsuspecting user is lured into downloading a fake ProtonVPN installer for Windows OS. Instead of getting the VPN they want, they receive a copy of the malware. Once downloaded, the fake software infects the victim's computer, adding it to the ever-growing AZORult botnet.
Researchers explain that upon execution, the malware collects environmental information about the infected device and uploads the gathered data to a command and control (C&C) server that is located at accounts[.]protonvpn[.]store. The malicious actors will then proceed to steal other information such as usernames, passwords, email credentials, and even cryptocurrency (Bitcoin, Electrum, Etherium, etc.) directly from the users' local wallets. Additionally, the malware will also obtain information from locally installed browsers, including cookies and browsing history.
Table of Contents
AZORult Malware Makes a Comeback
The information-stealing AZORult malware has been active since 2016 and has won the title of best-selling malware on the Russian forums. Buyers like AZORult because of its numerous functions and its proven high performance. Not only does the malware harvest sensitive information but it can also act as a dropper for other malware. Not to mention that it guarantees its owners anonymity by its crafty use of .bit domains as C&C servers. It more than justifies the high price tag of $100.
Although the malware continued to sell well, CrydBrox - the main distributor of Azoruld - stopped selling it at the end of 2018. CrydBrox explained that "All software has a shelf life. It's run out for AZORult. It is with joy and sadness that I announce that sales are closed forever."
Almost two years later, a new version of the malware is making a comeback with new tricks and improved rewritten code.
Technical Details
The original version of AZORult was written in Delphi programming language. In early May 2019, however, the malware returned and rewritten in C++. This new version of the malware is known as AZORult++.
During the analysis of the new variant, researchers discovered code lines that contain a path to debugging files. This discovery suggests that the malware is still under development because such lines are usually removed as soon as possible.
Researchers also found evidence that the new version of the malware is, in fact, a version of AZORult, and not a new threat. Evidence of this can be found in a section of the code that is left by the developer.
Figure 1: AZORult Directory
A hint left by the malware's developer that proves that this threat is the new version of AZORult. Source: Kaspersky.
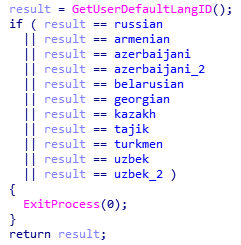
All versions of AZORult start the infection process with a checking procedure. The malware aborts the infection processes if it determines that the target system is using any of the following languages: Russian, Belarusian, Kazakh, Tajik, Turkmen, Uzbek, Armenian, Azerbaijani, or Georgian.
Figure 2: AZORult Language Targeting
The fraction of the code that is responsible for language checking. Source: Kaspersky
If the target system does not meet any of the whitelisted criteria, the malware will generate a unique ID for the device. This ID will be used for identification purposes during C&C communication and for the creation of a mutex.
AZORult++ Variant Capabilities
Researchers point out that AZORult++ shares many signature features with its previous version AZORult 3.3. The new variant, however, uses XOR operation with a 3-byte key to encrypt the stolen data sent to its C&C server. It also doesn't include a loader functionality nor does it have support for stealing browser-saved passwords.
The new variant is also capable of launching RDP connections. The malware does so by adding a new user account to the admin's group. The threat will then call a ShellExecute command to open a port and establish a remote connection to the victim's computer. Researchers warn that this trick allows the attackers to connect to the infected machine and take over the system.
Researchers also confirmed that AZORult can download and run additional payloads. The malware saves the malicious files in either the %TEMP% or the %ProgramFiles% folders. If the malware downloads an .exe file, it will run it via a CreateProcess command. Otherwise, it calls a ShellExecute command.
AZORult is designed to cater to its buyers. By using an online administration panel, the malware operators can configure AZORult to steal specific information and potentially drop additional malware samples.
Notable Incidents Involving AZORult Malware
At the end of 2018, the cybersecurity company Palo Alto Networks spotted a Fallout exploit kit campaign named "FindMyName" that delivered AZORult as a primary payload.
In December 2018, a sextortion campaign attempted to infect users' devices with AZORult, which, in turn, downloaded the destructive GrandCrab ransomware. AZORult was also found to be dropping the STOP ransomware.
A year and a half later, in February 2020, SANS' Internet Storm Center detected a campaign that used a triple-encrypted downloader to target users with AZORult.
Most recently, coronavirus-themed phishing attacks spread AZORult via emails. Researchers report that the attackers targeted industries such as manufacturing, transportation, pharmaceutical, and cosmetics. The criminals, which are believed to be located in Russia and Eastern Europe, spread messages that were crafted to exploit a Microsoft Office vulnerability. The malicious emails warn the victims of the potential dangers of Coronavirus in the shipping industry. Similar Coronavirus-themed attacks were also spotted to deliver another data-stealing and malware-dropping Trojan Emotet.





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.