
In March 2019, Amnesty International published a report, warning of phishing attacks targeted at Egyptian human rights defenders, media, and civil society organizations. The campaigns were carried out by an attacker group known as “NilePhish.”
New samples of FinSpy were observed to, yet again, target Egyptian civil society organizations. This time, the attackers widened the scope of their attacks by including exploits for macOS and Linux systems.
FinSpy spyware is a Windows and Android surveillance malware used by law enforcement and government agencies since 2011. According to Amnesty International, who published a malware analysis on FinSpy, the threat is a commercial malware that is capable of intercepting communication, accessing private data, and recording audio and video.
FinSpy for macOS
The macOS version of FinSpy uses a complex infection chain that implements anti-forensic routines to hinder detection and analysis. The attacks include a check mechanism designed to determine whether the malware is launched in a Virtual Machine. Furthermore, researchers point out that all malware binaries are obfuscated with the open-source tool LLVM-obfuscator.
Figure 1: macOS Infection Vector
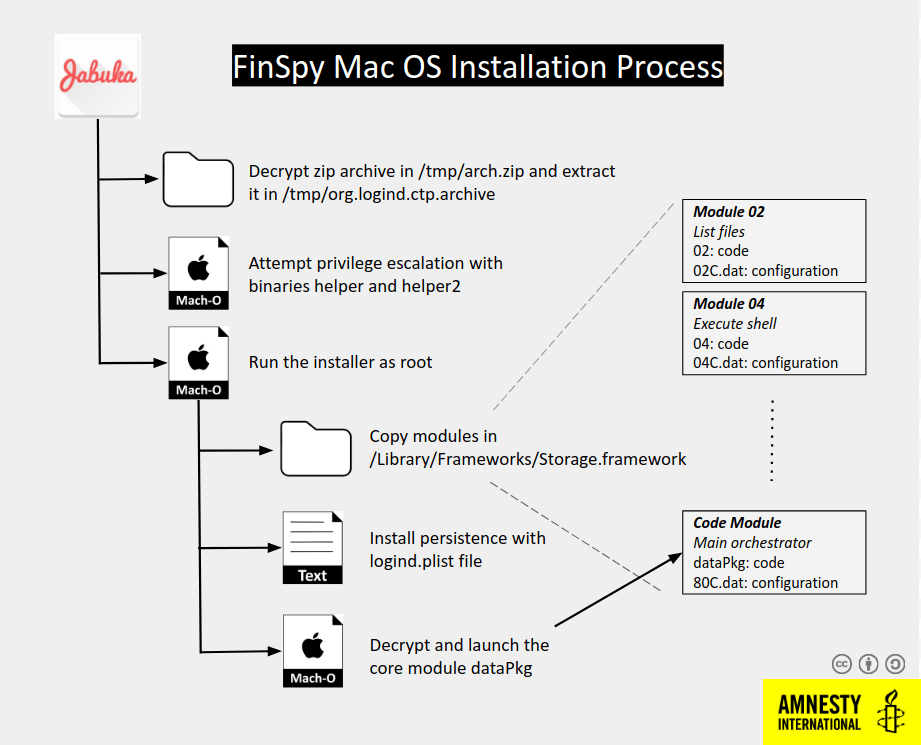
In cases when the scan determines that the target is a standard device and not a VM environment, the ZIP file arch.zip that contains the main payload and privilege escalation binaries will be unpacked to the /tmp/org.logind.ctp.archive directory.
The attackers target a bug in macOS versions older than 10.9 and the CVE-2015-5889 vulnerability to obtain root access. If the operations fail to exploit the vulnerabilities, the user will be asked to grant root permissions to launch the next stage installer.
The main installer, which is dropped at /tmp/org.logind.ctp.archive/installer directory, will copy all the plugins and configuration files to /Library/Frameworks/Storage.framework. Additionally, it will copy the launcher to /private/etc/logind directory and establish persistence by creating a logind.pslist file in /System/Library/LaunchAgents/ folder.
Linux Variant
The Linux payload is identical to the macOS version. However, the launchers and the infection chain are adapted to work on Linux systems. Researchers speculate that this similarity is due to a shared codebase.
Figure 2: Linux Infection Chain
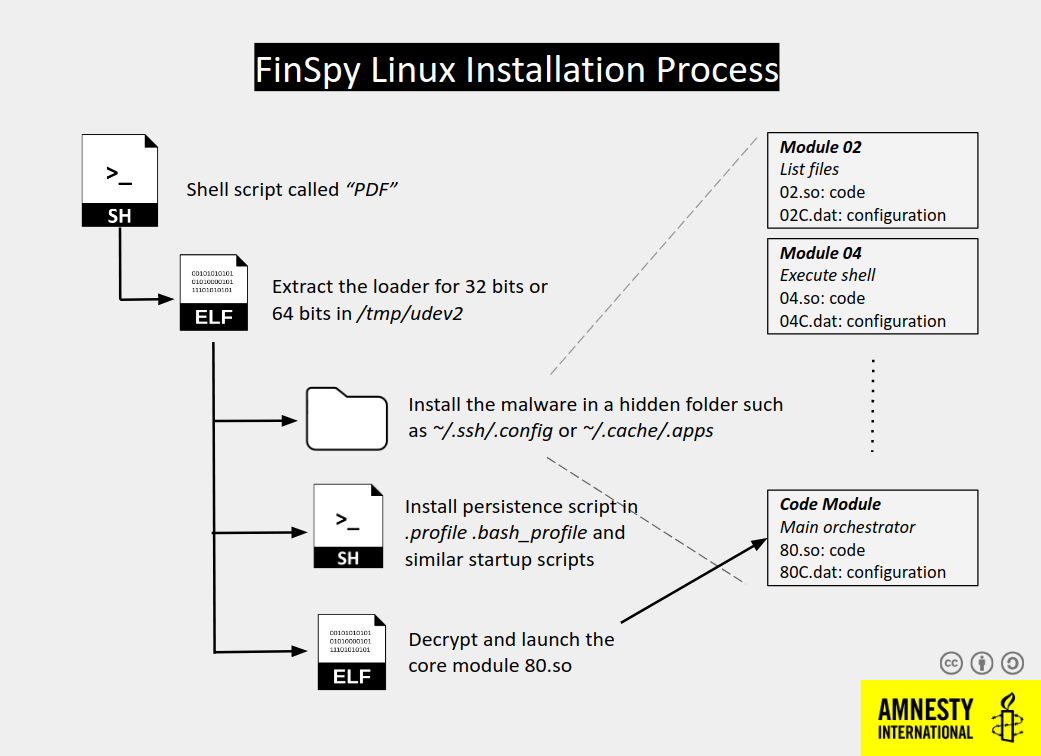
The Linux infection chain starts with a PDF file obtained from a server. The file is a short script containing encoded binaries for Linux 32bit and 64bit that extract a binary in the /tmp/udev2 directory and execute it.
Similar to the macOS variant, the Linux binary will check if it is in a VM environment and will abort the installation if a virtual machine is detected.
Both the macOS and Linux variants contain a long list of modules designed for specific operations, including keylogging, scheduled screen recording, audio recording, email sniffing, collecting information about WiFi networks, and more.
Researchers state that “FinSpy for Mac OS, and similarly its Linux counterpart, follow a modular design,” adding that “[t]he modules available in the Linux sample are almost identical to the MacOS sample.”





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.