The Netherlands' National Cyber Security Center (NCSC) has released a confidential report that warns of targeted ransomware attacks that have affected at least 1,800 companies worldwide. The names of the affected organizations have not been released, but the investigators stated that the cyberattacks were targeted at key infrastructures all over the world.
The Dutch state television network NOS, which obtained a copy of the NCSC report, reports that multiple multinational giants have been hit. The targets included automotive firms, entertainment companies, construction, and chemistry firms, as well as hospitals. These attacks cost up to $5.8 million per incident, researchers add.
The NCSC report highlights three cryptolockers with similar digital infrastructures that were used in attacks in 2019. Considered 'common forms of ransomware,' MegaCortex, LockerGoga, and Ryuk ransomware have gained notoriety for successfully targeting high-profile victims.
Security researchers believe that the three malware strains named by the NCSC report are run by a well-organized criminal structure. The three threats have specific targets and work in combination with other malware to maximize profit from the attacks. As we already reported, while LockerGoga is used in attacks against critical infrastructures, including the US chemical giant Norsk Hydro, Ryuk ransomware breaks government, healthcare, and education institutions.
Table of Contents
Big Game Hunting: Targeting Corporate Networks
Reports suggest that MegaCortex ransomware infects corporate networks that are already compromised with other malware such as Emotet and Qakbot Trojans.
After MegaCortex gains access to a network, it compromises the Windows domain controller. The ransomware will then install Cobalt Strike, which opens a reversed shell back to the attackers.
The threat actors then configure the domain controller to distribute a batch file and the primary executable of the ransomware (winnit.exe) to all devices connected to the network. The attackers then run the batch remotely and terminate over 1,396 Windows processes and services that might interfere with the ransomware's operations.
Early versions of MegaCortex are reported to execute the woinnit.exe file with a specific Base64 argument. This encoded string is required in order for the ransomware to extract and inject a DLL file into rundill32.exe. If everything goes according to the plan, this DLL encrypts the user-generated files.
Batch file commands:
- bat: start copy stop.bat \\<target IP address>\c$\windows\temp\
- bat: start copy winnit.exe \\<target IP address>\c$\windows\temp\
- bat: start wmic /node:"<target IP address>" /user:"<DOMAIN\DC user account>" /password:"<DC admin password>" process call create "cmd.exe /c copy \\<a different DC's IP address>\c$\windows\temp\stop.bat c:\windows\temp\"
- bat: start wmic /node:"<target IP address>" /user:"<DOMAIN\DC user account>" /password:"<DC admin password>" process call create "cmd.exe /c copy \\<a different DC's IP address>\c$\windows\temp\winnit.exe c:\windows\temp\"
- bat: start wmic /node:"<target IP address>" /user:"<DOMAIN\DC user account>" /password:"<DC admin password>" process call create "cmd.exe /c c:\windows\temp\stop.bat"
- bat: start psexec.exe \\<target IP address> -u <DOMAIN\DC user account> -p "<DC admin password>" -d -h -r rstwg -s -accepteula -nobanner c:\windows\temp\stop.bat
Later versions of the ransomware don't need the Base64 argument to run the DLL. Instead, the ransomware's executable will start encrypting target files after it launches. This updated executable extracts two DLL files and three CMD scripts in the C:\Windows\Temp folder. The DLL files encrypt the victim's data by running through Rundll32.exe. The ransomware uses the SCD files to execute various commands that remove shadow volume copies, wipe all free space on the C:\ drive, and delete all files that were used to encrypt the system.
MegaCortex marks the successfully encrypted files with the .megac0rtx extension. Some variants of the ransomware use .aes128ctr and .m3g4c0rtx file extensions.The Ransomware also drops a ransom note named '!-!_README_!-!.
Figure 1: Megacortex Ransom Note
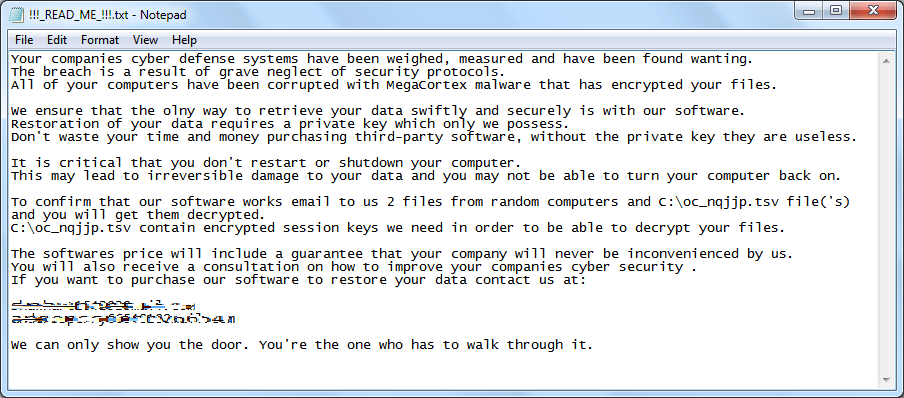 Ransom note shown to the victim with details on how to pay to decrypt their personal data. Source: trendmicro.com
Ransom note shown to the victim with details on how to pay to decrypt their personal data. Source: trendmicro.com
The ransom note contains the attackers' emails and payment instructions. The message also lists several threats that, according to researchers, are idle. The threats are meant to push the victims into paying the ransom. Further analysis of the ransomware, however, determined that some of the threats are true.
MegaCortex Changes User Password and Threatens to Publish the Private Data
Security researcher Vitali Kremez confirmed that MegaCortex indeed changes the passwords for the victims' Windows accounts. The ransomware does this by executing a net user command during its initial execution. During this step, the attackers add a legal notice that is displayed when the victim loads their OS. The notice, as shown in Figure 6 below, informs the victim that they will no longer be able to access their desktop.
In addition to preventing the victims from using their computer, the threat actors threaten to make the victim's data public if they don't pay the ransom. It’s yet to be confirmed or denied if the actors will carry out these threats. If it turns out that the malicious actors do save copies of the victims' data, MegaCortex should not be treated as ransomware but as a complex malware that exposes its victims to multiple layers of risks.
Preventing Megacortex Infection
MegaCortex is linked to Emotet and Qakbot Trojans, which are believed to drop the deadly ransomware. Therefore, warning alerts about these cyber infections should be taken seriously and acted upon quickly and efficiently to reduce risk.
It’s recommended that individuals and business users alike adopt some basic cybersecurity best practices. Using backup devices that are kept offline or disconnected from local network devices can also mitigate potential ransomware risks. All users must, of course, keep their systems updated with the latest security patches, as well as keep their software up-to-date. Enterprises are recommended to invest in teaching their employees to identify potential risks.
In case of a ransomware attack, users are advised to isolate their compromised computers. Isolating the infecting device minimizes the risk of the ransomware spreading to other computers.





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.