Over the past couple of years, the Ryuk ransomware family has been wreaking havoc at hundreds of companies around the world with no signs of slowing down. Ryuk ransomware has been circulating around in cyberspace for a while now, however, in the last few months, infection incidents have been increasing at an alarming rate. Ryuk ransomware has targeted multiple organizations in the US and around the world, netting hackers nearly 4 million USD.
Ryuk ransomware is a malware belonging to the ransomware family. It works by encrypting the files of a target computer rendering them inaccessible. The user is presented a note by the threat actor demanding monetary payment in order to decrypt the files and make them accessible again.
Ryuk ransomware was created using the code from another infamous ransomware known as HERMES. While the two Hermes and Ryuk bear some similarities, Ryuk ransomware was specifically designed to target large organizations.
Table of Contents
How Ryuk Spreads
The Ryuk ransomware uses two powerful banking trojans known as Trickbot and Emotet to distribute itself. These two trojans can be spread through phishing emails designed to trick a user to download the payload dropper.
Ryuk utilizes a combination of trojan droppers, ransomware executable, and batch files to infect and encrypt a system. Obtaining samples of the dropper trojans is difficult due to the payload executable deletes any traces of the dropper. However, researchers have detected on Ryuk ransomware the use of Trickbot and Emotet, two notorious trojans used to gain access to systems.
The ransomware executable is placed and installed on a directory created by the dropper, the malware dropper. These directories are C:\Documents and Settings\Default User\ directory for Windows XP users, and C:\Users\Public for newer versions of windows. Once the directories are created, the executable file will be created using a random filename.
Laying the Groundwork To Ensure Persistence
Ryuk ransomware uses a combination of symmetric and asymmetric encryption implementing the AES-256 and RSA-2048 algorithms to encrypt its files. The attacker will have an RSA global private key which is his only way to decrypt the system. At the same time, it utilizes batch files to execute commands during and after the encryption in order to ensure the files are unrecoverable and that Ryuk runs every time on when the infected terminal starts up.
Ryuk Ransomware also contains two batch files, kill.bat, and windows.bat, to hijack system processes and to prevent system and file recovery before it begins the encryption process. These batch files contain a number of commands to stop processes that would impair the encryption process such as open file handles and anti-virus software.
Commands Executed by kill.bat:
- net stop avpsus /y
- net stop McAfeeDLPAgentService /y
- net stop mfewc /y
- net stop BMR Boot Service /y
- net stop NetBackup BMR MTFTP Service /y
- sc config SQLTELEMETRY start= disabled
- sc config SQLTELEMETRY$ECWDB2 start= disabled
- sc config SQLWriter start= disabled
- sc config SstpSvc start= disabled
- taskkill /IM mspub.exe /F
- taskkill /IM mydesktopqos.exe /F
- taskkill /IM mydesktopservice.exe /F
These commands show the kill.bat using the ‘net stop’ command to stop antivirus processes and the ‘taskkill’ and ‘sc config’ commands to stop other related services.
In order to ensure its survivability in an infected system, Ryuk does changes to the Run registry key. It uses the windows shell to run the svchos command to insert the Ryuk file path to HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run.
This command is used to modify the registry key to ensures that Ryuk Ransomware runs everytime when restarting the infected machine.
Encrypting the System
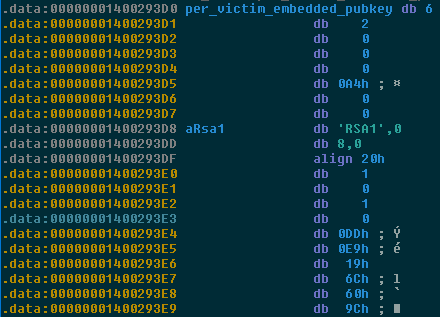
Normally, the encryption process begins with the creation of an RSA key pair in the local system. In the case of Ryuk, the malware is pre-embedded with a public and private RSA key pair. The private key is pre-encrypted with the global RSA key. The global key is held by the hacker distributing the Ryuk ransomware and is needed to decrypt the system. After the batch files disable any type of software or backup that could impede the encryption process, Ryuk ransomware will begin encrypting process of all files in the system. Unlike other ransomware, Ryuk ransomware does not target any specific file extensions which means all files in the system will be encrypted. However, the malware does avoid files ending with the .dll, .exe, and .hrmlog extensions. The Windows, Microsoft, Chrome, Mozilla, Recycle.bin and AhnLab folders are also not encrypted. This was probably done to maintain some level system stability.
Source: research.checkpoint.com
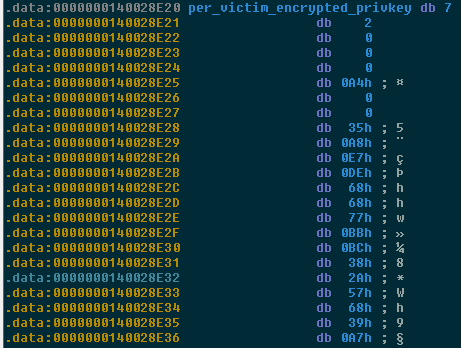
Afterward, the malware will use CryptoGenKey to encrypt system files using an AES encryption generating a unique decryption key for each victim. This key is stored in a file using CryptoExportKey, encrypted with the pre-embedded private RSA-key, and stored in user files.
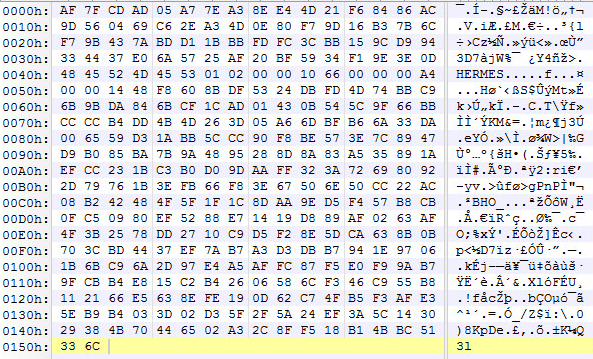
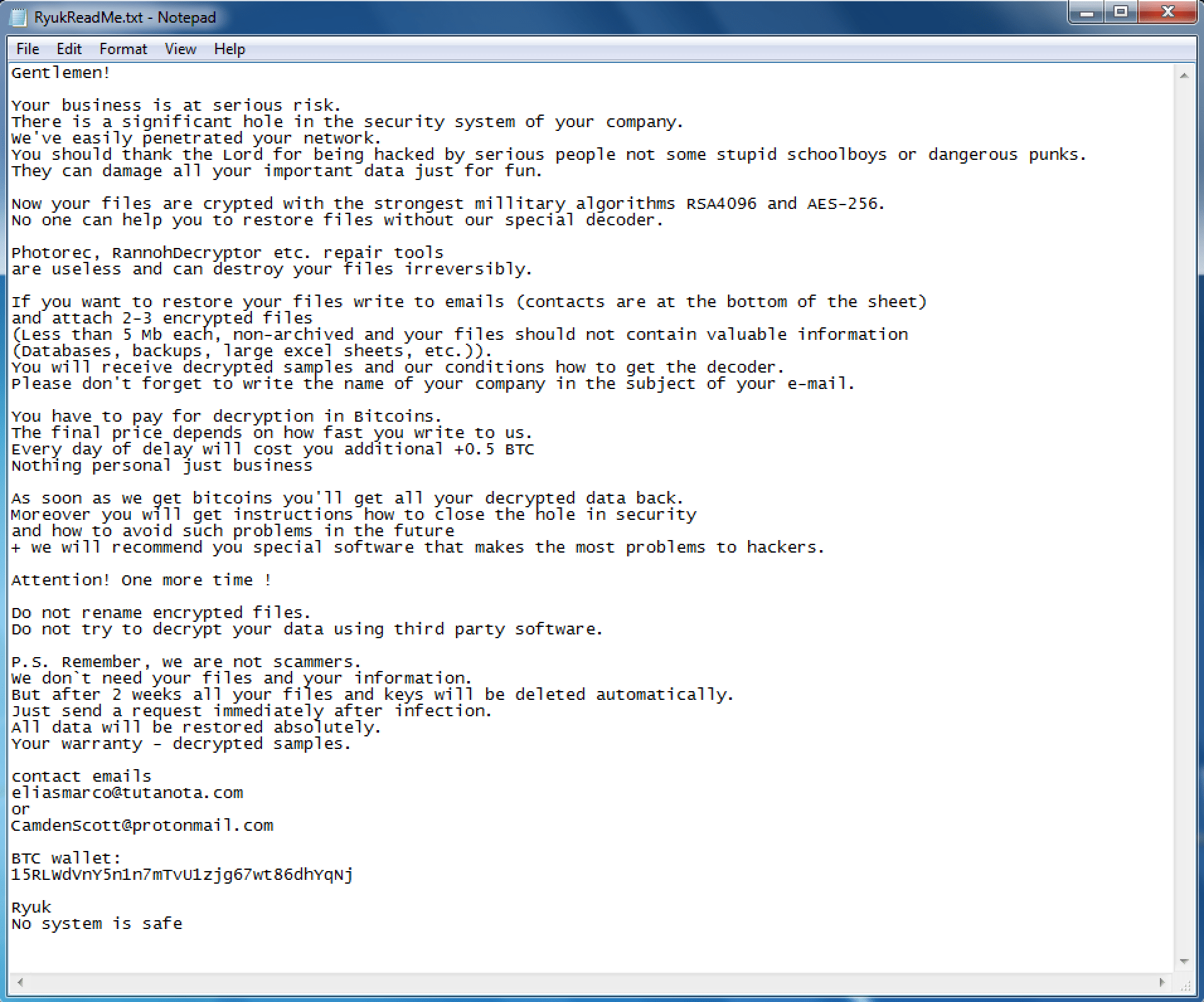
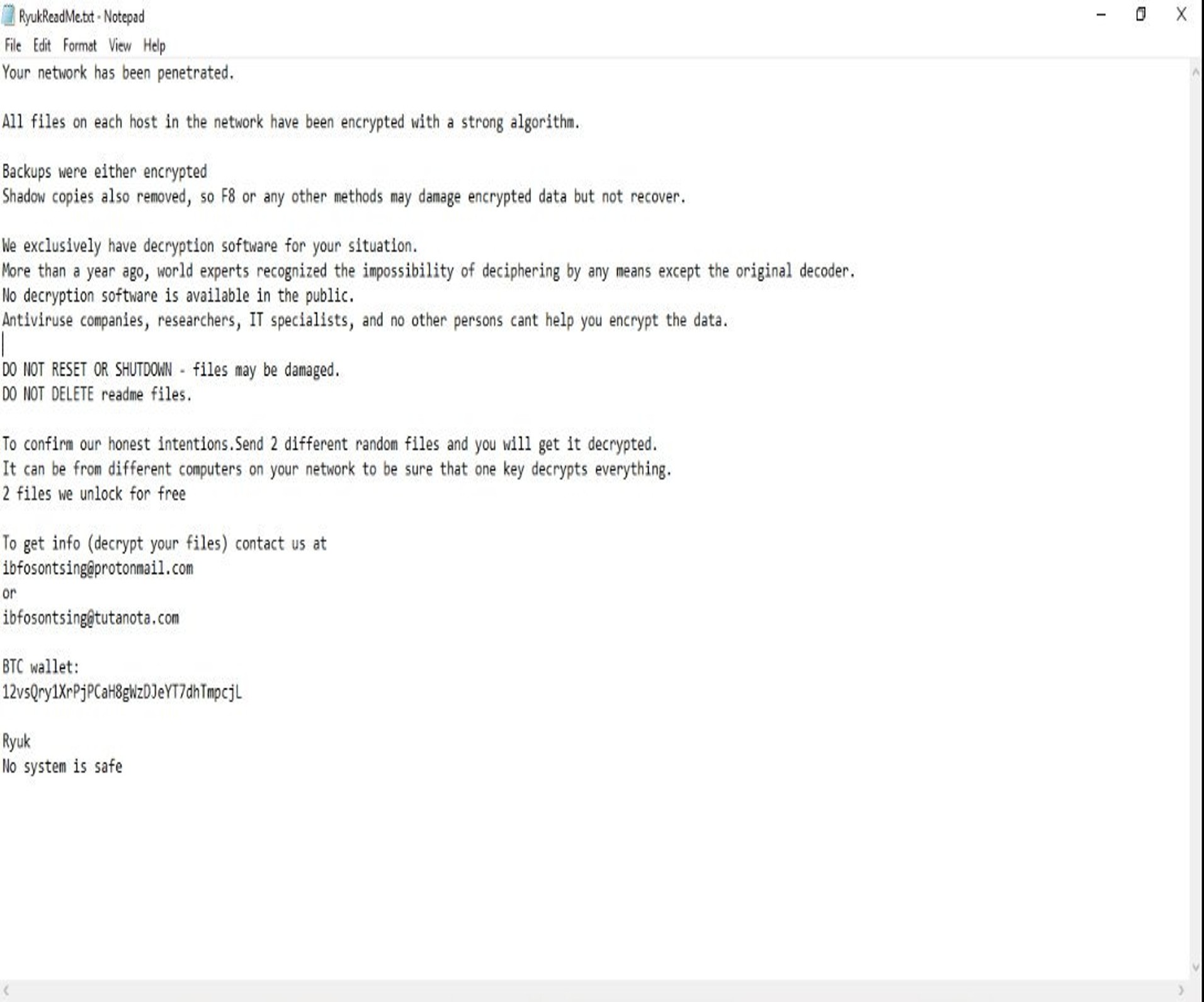
Once the encryption process finishes, encrypted files will have the .RYK file extension added. Furthermore, a txt file RyukReadMe.txt will be added to every directory. This file is a ransom note from the threat actors with instructions on how to contact them and submit payment to decrypt affected terminals. Payment for decryption varies between targets. The note does not give any information regarding the ransom amount.
Destroying Backups using the windows.bat file
The windows.bat is responsible for making sure the system is unrecoverable. One of its functions is to delete data from services such as Windows Volume Shadow Copy Service (vss). It will also attempt to delete any other third-party backup located in the computer's drive.
Commands executed by windows.bat using the vss utility:
- vssadmin Delete Shadows /all /quiet
- vssadmin resize shadowstorage /for=c: /on=c: /maxsize=401MB
- vssadmin resize shadowstorage /for=c: /on=c: /maxsize=unbounded
- vssadmin resize shadowstorage /for=d: /on=d: /maxsize=401MB
- vssadmin resize shadowstorage /for=d: /on=d: /maxsize=unbounded
- vssadmin resize shadowstorage /for=e: /on=e: /maxsize=401MB
- vssadmin resize shadowstorage /for=e: /on=e: /maxsize=unbounded
- vssadmin resize shadowstorage /for=f: /on=f: /maxsize=401MB
- vssadmin resize shadowstorage /for=f: /on=f: /maxsize=unbounded
- vssadmin resize shadowstorage /for=g: /on=g: /maxsize=401MB
- vssadmin resize shadowstorage /for=g: /on=g: /maxsize=unbounded
- vssadmin resize shadowstorage /for=h: /on=h: /maxsize=401MB
- vssadmin resize shadowstorage /for=h: /on=h: /maxsize=unbounded
- vssadmin Delete Shadows /all /quiet
Here we see the windows.bat file using the vssadmin utility to delete data on windows shadow storage by resizeing storage space.
Lastly we can see the a ‘del’ commands targeting drives and file extensions commonly associated with backups.
Lastly we can see the a ‘del’ commands targeting drives and file extensions commonly associated with backups.
Noteworthy Capabilities
Businesses around the world have lost billions of dollars to Ryuk ransomware.
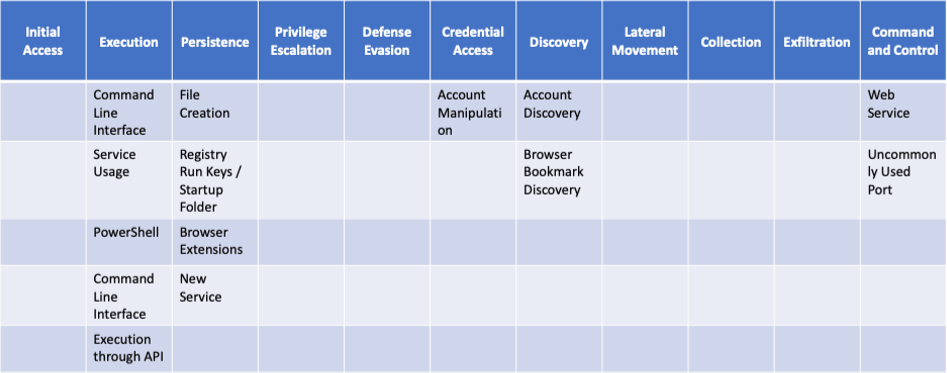
Ryuk ransomware stands out from most ransomware due to its added functionality to effectively target large corporate networks. The reasoning behind this is that bigger organizations will result and a higher payout to decrypt files. Some of these functionalities include:
- Acquiring system privileges to access the Domain Controller Server in charge of security authentications.
- The capability of locating and deleting backups
- Implementing anti-recovery commands to impede file restoration
- Capabilities to scan and spread across a network using Remote Desktop Protocol(RDP)
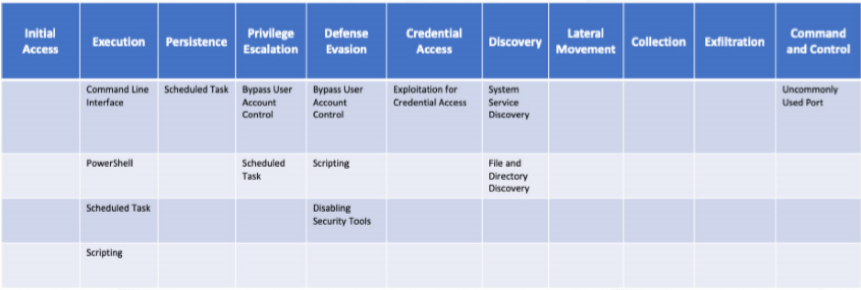
Ryuk ransomware undergoes constant re-engineering by hackers, adding and removing functionality based on their needs. This has given rise to a number of variants, with different levels of capabilities. There are some differences between variants regarding which file types they whitelist during the encryption process. Some variants incorporate anti-analysis tools, the scope of targeted files, IP address blacklisting, and more.
How Do You Identify If Ryuk Has Encrypted Your Files?
Users infected with Ryuk ransomware will be unable to open any of their files. Furthermore, every file will be appended with the .ryuk extension. So a file named ‘myfile.txt’ will turn into ‘myfile.txt.ryuk’. Additionally, every directory will contain an unencrypted txt file named ‘RyukReadMe.txt’ in every directory. This unencrypted text file contains a ransom note with details on how to contact the attacker and pay to recover the encrypted system.
So far two versions of the Ryuk ransomware have been detected. One of them is a long version that seems to be targeted at corporations given the professional tone used, content, and messages such as “your business is at risk.” The second one is much shorter and to the point.
Both of them instruct the victim that they need to make a bitcoin payment to the threat actor in order to have their files decrypted. The note does not specify the amount needed to be paid, which gives the attackers more wiggle room to negotiate based on the target.
Who is the Mastermind Behind Ryuk Ransomware?
The main purpose behind the Ryuk ransomware attacks seems to be monetary gain. One can make this assertion given that they actually decrypt the targeted system if the payment is paid. This would not be the case if the main goal of the threat actors was to disrupt and permanently damage the infected systems. In the beginning, there were suspicions of the North Korean hacker group Lazarus being behind all the Ryuk incidents. However, further research by security analyst indicates that the threat actors are part of a Russian based hacking group known as Grim Spider. It is possible and likely that other hacker groups or individuals also use the Ryuk Ransomware.
Major Cyberattacks Involving Ryuk
Ryuk has had an infamous track record of targeting large organizations. Hundreds of companies around the world have fallen victim to the ransomware and forced to pay to decrypt their files. The healthcare industry, in particular, is an extremely attractive target to cybercriminals due to their willingness to pay to recover sensitive patient data
The FBI issued a warning that Ryuk is still a threat to businesses. Some high profile incidents involving the Ryuk Ransomware include:
- According to a report by the Federal Bureau of Investigation (FBI), more than 100 American businesses have been affected by the Ryuk ransomware.
- CloudJumper, a cloud service provider, was infected with Ryuk but managed to contain the infection and restore its systems without needing to pay a ransom.
- Two Florida cities, Riviera Beach and Lake City suffered a ransomware attack believed to be a strain of Ryuk. This resulted in a ransom payout of $600,000 and $400,000 respectively.
- More than 20 city agencies in Baltimore were infected with Ryuk resulting in delays in services to patients.
- A ransomware campaign against leading U.S. media organizations such as The Los Angeles Times, The New York Times, the Wall Street Journal, Baltimore Sun, and Chicago Tribune.
- Ryuk infected a Cloud hosting company named Virtual Care Provider Inc which provides services to over 110 hospitals, causing disruptions across all the health providers.
Ryuk Ransomware Hashes
MD5 Hashes
- c0202cf6aeab8437c638533d14563d35
- d348f536e214a47655af387408b4fca5
- 958c594909933d4c82e93c22850194aa
- 86c314bc2dc37ba84f7364acd5108c2b
- 29340643ca2e6677c19e1d3bf351d654
- cb0c1248d3899358a375888bb4e8f3fe
- 1354ac0d5be0c8d03f4e3aba78d2223e
SH256 Hashes
- 1b465c0e12523747f892b48fa92a30f82e5027199a2aff06587c5269bd99f69a
- 3c8531fc54eca31a79a23bf16d4f528067c89a5e58e1e745a2c5b1b05140f5a8
- 95b228b664dca2e18935444c67c7c7dbda9da7450a18d429cb04f7e311af5fe9
- 46fb27f4cff2d33baae3b1c199797d1f0929bc03166cebd092081e4fe2f9ea6e
- 8d50d9fe17eb36edc9945a2673c1594f58a6e653f5a794058ee42e46d24d83d7
- f21f222d8f62f2223faec375e834efb76f96b73ef70e0ef09024586cf9eef638
- b7e945a8dafc91ebe8c8717ee3107498afc1ad5461599611d2fb07aaa7700aa1
- 88d491bb73d509aacca103919d3a7418f9c6b611ce7dc453e1cacffed9c0f0d5
- 5e4160a133d44a1cf90d72eedd5e6084543521fecbf070d550c6012d294ccb28
- aacfc3e386ed12082923d03fa1120d5fa6bf7b8655ba77e04b96a45434fa9a83
- 235ab3857ba2d2cd09311d6cc7bf1139863022579ea98be2b503921104ee20ac
- 7c1e0597dd5a1e2d48c9cede54843aa7c299f7404630b5a2aafac2eec7358b20
- 9fe66773c84d371ef1b424005996ade4d5e16fb00306a1d54b107b2b2d03fe17
- 695a716f2c43a69bdd03e74058fa23fb77e596bb4f1f3a021d529c85e9564f7d
- 6eca3f416a08fde6688250dbd4ba4dfaa3df95a5d26b6d978dfbd67fbd159619
- 965884f19026913b2c57b8cd4a86455a61383de01dabb69c557f45bb848f6c26
- 8d3f68b16f0710f858d8c1d2c699260e6f43161a5510abb0e7ba567bd72c965b
- 3012f472969327d5f8c9dac63b8ea9c5cb0de002d16c120a6bba4685120f58b4
- b8e463789a076b16a90d1aae73cea9d3880ac0ead1fd16587b8cd79e37a1a3d8
- 9b86a50b36aea5cc4cb60573a3660cf799a9ec1f69a3d4572d3dc277361a0ad2
- 113af75f13547be184822f1268f984b79f35965a1b1f963d23b50a09741b0aec
- 1455091954ecf9ccd6fe60cb8e982d9cfb4b3dc8414443ccfdfc444079829d56
- c51024bb119211c335f95e731cfa9a744fcdb645a57d35fb379d01b7dbdd098e
How to Protect Yourself from Ryuk Ransomware
Unfortunately, there is no official decryptor that can restore the files encrypted by Ryuk ransomware. There are some methods that involve using anti-malware software or third-party file recovery tools. However, as stated before, there is no guarantee that your files will be restored. Furthermore, by using these third party methods there is a risk that can render your files unrecoverable.
For now, the best way to protect yourself from Ryuk Ransomwarehave is to have an efficient policy regarding email security and implementing systems that prevent the execution of malicious code. Training employees to recognize the telltale signs of phishing emails can also help to mitigate malware infections. Since Ryuk specializes in deleting backups across the network of an infected computer, keeping additional backups that are isolated from the network could help in case your main ones are compromised.





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.