A new malware threat dubbed Octopus Scanner was recently discovered hiding in GitHub repositories. The GitHub Security Lab, who acted on a tip by a security researcher known as "JJ," identified 26 open-course repositories infected with the dangerous threat.
Table of Contents
Octopus Scanner: A Malware for Developers
GitHub, which is a cloud variant of Git, is a system that allows developers to store copies of files of their software development projects. The file copies can be used as backups, allowing the developers to revert changes or to create new branches that other people can download (clone) and work on individually for different projects.
However, Octopus Scanner interferes with this system. If a developer downloads a project from a repository that is infected with the threat, the software that they build will be based on a malicious source code, which will eventually get uploaded on other GitHub repositories, resulting in the spread of the malware.
Octopus Scanner is designed to take over developers' machines by targeting Apache NetBeans, an environment used to develop Java-based software. The malware takes advantage of GitHub’s design to spread itself on the platform and infect legitimate software-development projects.
Octopus Scanner Infection Vector and Installation
The malware will activate when a developer downloads an infected file and implements it in a software project. Once the malicious file is incorporated into the project, the malware will scan the developer's computer for the NetBeans IDE. If the environment is not installed, there will be no further malicious actions. However, if it's present, Octopus Scanner will infect the project build files with a malware dropper that delivers a final payload, a file named cache.dat, which is a remote access trojan (RAT) that enables the attacker with full control of the victim's device.
Figure 1: Octopus Scanner Infection
IMG:
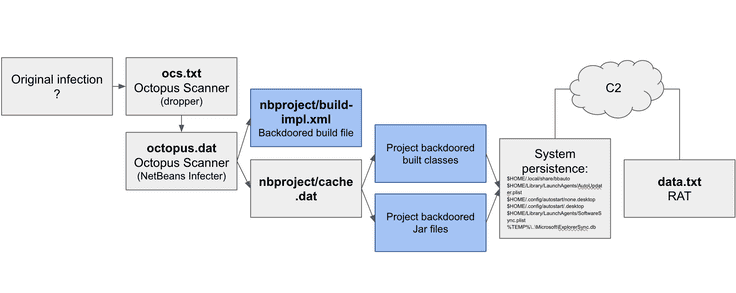 This diagram illustrates the infection mechanism of the latest Octopus Scanner variant. Source GitHub
This diagram illustrates the infection mechanism of the latest Octopus Scanner variant. Source GitHub
Additionally, the malware will try to protect itself and establish some form of persistence by blocking any new project builds that might replace the corrupted one. GitHub researchers point out that the analyzed samples of Octopus Scanner don't drop files in an attempt to persist on the infected machine. Instead, the catche.dat file carries out the actual system infection.
It appears that the malware actors focus on infecting as many victims as possible. They have designed Octopus Scanner to identify and corrupt NetBeans project files, which are likely to be downloaded and used by an indefinite number of victims.
"Infecting build artifacts is a means to infect more hosts since the infected project will most likely get built by other systems and the build artifacts will probably be loaded and executed on other systems as well," GitHub wrote.
Fast Infection and Slow Detection Rate
The GitHub security team managed to match the malware with hashes on VirusTotal, revealing an alarming low detection rate, which is indicative of the threat's ability to spread without being caught. Furthermore, as the malware infects open-source repositories, the infected files can easily be downloaded and used for various individual projects, creating a fast and unpredictable malware transportation chain.
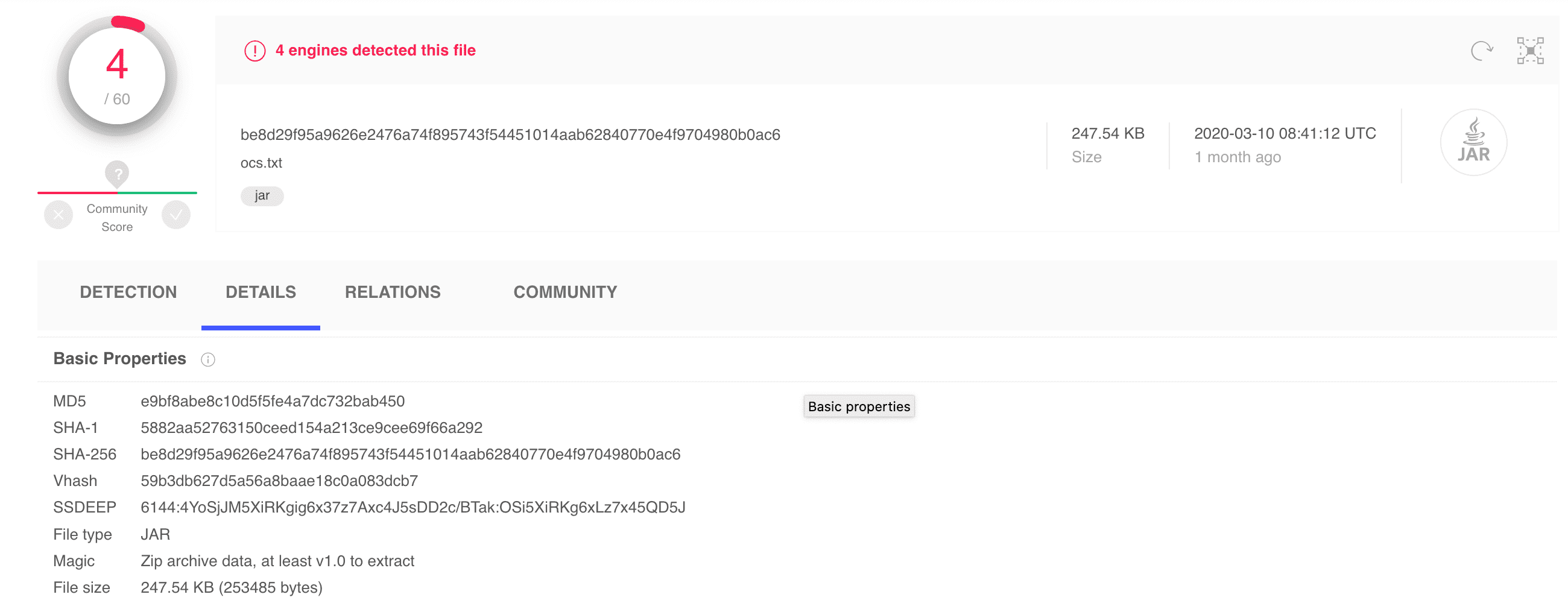
Figure 2: Detection rate
Caption: In this image, we can see that only 4 out of 60 antivirus engines flagged Octopus Scanner as malicious. Source: GitHub
Octopus Scanner is not the first malware threat to enter the GitHub system. Usually, the company shuts down the infected repositories and deletes the accounts. However, Octopus Scanner is more tricky as it affects developers who aren't aware that they are infected with malware.
Since GitHub is used to run legitimate projects by developers all around the world, shutting down their accounts will affect their business operations. Deleting the infected repositories is also not an option as they contain essential files that could be critical for the development of legitimate software. Being unable to delete the infected repositories, the GitHub team faces a labor-intensive clean up that will keep them busy for quite some time.
"Since the primary-infected users are developers, the access that is gained is of high interest to attackers since developers generally have access to additional projects, production environments, database passwords and other critical assets," the GitHub team explained.
Was it a targeted attack?
As NetBeans IDE is not a wide-spread Java development environment, researchers speculate that the Octopus Scanner attack was aimed at specific targets. Research shows that the malware has been active since at least 2018, potentially trying to penetrate organizations that have been using the unpopular IDE for quite some time.
The design of the malware also suggests that the threat actors invested time to make sure that their threat can easily spread wildly on its own. As Octopus Scanner targets open-source projects, many infected files are likely to be cloned or forked for many individual projects, spreading the malware in untraceable fashion.
It is also possible that the attacker might be targeting the developers themselves. As GitHub points out, these people usually have access to multiple projects, password databases, and other restricted resources. The core of every cyberattack is to obtain access to critical assets. In Octopus Scanner's case, a successful cyberattack on the right target could result in the exfiltration of sensitive information, including corporate secrets and clients' details.
Not the First and Certainly Not the Last
Although Octopus Scanner is not the first malware to affect the software building process, its active deployment is definitely alarming. The threat is a warning to all developers that don't pay attention to their cyber hygiene.GitHub recommends their users to use the available security features, including Dependency Graph, security alerts for vulnerable dependencies, and code scanning, that can help prevent malicious code from spreading.





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.