A new ransomware family named 'Buran' tempts criminals with special offers and promises for fast money.
Operators of Buran ransomware are following a trend that is becoming increasingly popular among malware creators. Instead of distributing the malware themselves, they offer it as a service to affiliate cybercriminals. This business model, also known as ransomware-as-a-service (RaaS), grants Buran's creators a percentage of the extorted ransoms without getting their hands dirty. Their affiliates are responsible for the ransomware distribution, while the operators provide technical support.
Table of Contents
Buran Ransomware is a Bargain for Affiliate Cyber Criminals
Last November, researchers spotted a post on a well-known Russian forum offering Buran's services in exchange for only 25% of the extorted ransoms. Buran's rates seem temptingly low compared to other RaaS threats, such as the infamous GradCrab and Phobos ransomware, whose commissions vary between 30% – 40%. On top of that, Buran's operators are open to negotiations 'with anyone who can guarantee an impressive level of infection with Buran.'
Figure 1: Ransomware-as-a-Service
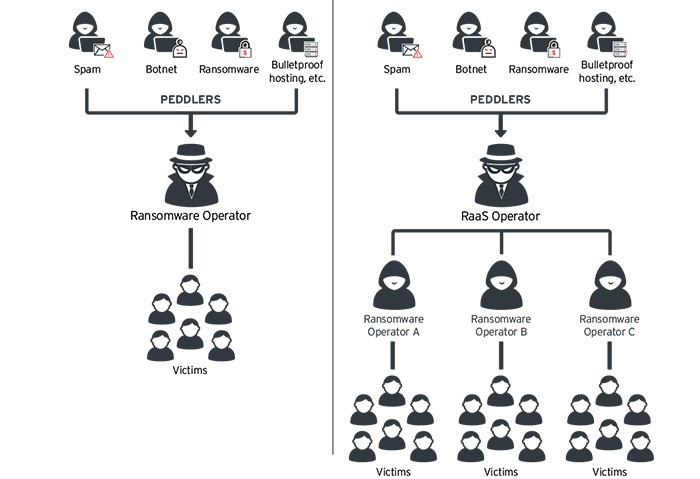 Diagram showing the Ransomware-as-a-Service business model. Source: trendmicro.com
Diagram showing the Ransomware-as-a-Service business model. Source: trendmicro.com
Buran is advertised as a 'stable offline cryptolocker, with flexible functionality and support 24/7.' It is a threat that can scan local drives and network pats, encrypt files without changing their extensions, and has 'no third-party dependencies such as libraries.' The ransomware is also capable of removing recovery points, logs, and backup catalogs, as well as is adapted to delete itself from the system when necessary.
Security researchers agree with these statements. The only false promise so far is the claim that Buran is compatible with all versions of Microsoft Windows OS, Windows XP, however, was discovered to be immune. Researchers at McAfee also point out that, although Buran is programmed not to attack computer systems located in the CIS segment, the only countries that have their computes whitelisted are the Russian Federation, Ukraine, and Belarus.
Origin of Buran
Buran is not an entirely new threat but an evolved version of the infamous VegaLocker ransomware. The two threats modify the registry in a similar manner, as well as store files in temporary folders. Security researchers point out that these similarities merely suggest that the two threats are related but not necessarily connected.
One key piece of evidence, however, links the two threats undeniably. Both VegaLocker and Buran use the same methodology to delete backups, system shadow copies, and system backups. Researchers also agree that Buran shares several artifacts with Jumper (also known as Jamper) ransomware, which is yet another version of VeraLocker.
VeraLocker's last spamming campaign, which continued from late 2018 to April 2019, spread not only the deadly ransomware but also spyware, banking Trojans, and malicious payloads of other ransomware, one of which was believed to be Buran. That theory was later proven wrong, but researchers look at this period as a milestone that marks the time when the malicious actors abandoned VeraLocker and focused on Buran.
How Does Buran Reach its Victims?
One of the vectors of infection used by Buran to infect systems involves the usage of RIG Exploit Kit which exploits Remote Desktop Protocol (RDP) vulnerabilities such as CVE-2018-8174.
Recently, Buran ransomware is mainly spread via multiple malspam campaigns containing malicious word and excel documents. These can be delivered either through attachments or through a link that takes the user to a PHP site hosting the documents containing Buran’s payload. These documents contain embedded macros and PowerShell scripts.
Security researcher Suspicious Link reported a new spam campaign that distributes Buran through Microsoft Excel Web Query (IQY files) attachments.
Figure 2: Example of Buran’s Malspam 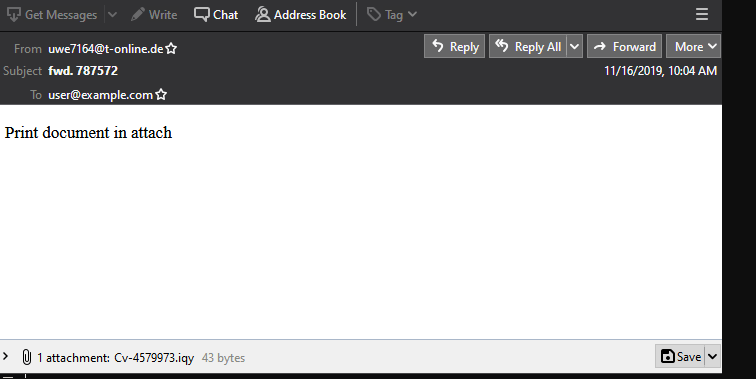
The malicious emails lure the users to 'Print the document in attach' by pretending to be forwarded messages. Source: twitter.com/killamjr/status/1195821676824604672
When a user opens the attached Excel IQY file, the document imports malicious data into a worksheet from an external source.
Excel has a built-in security mechanism that asks the user whether they want data to be downloaded (Figure 2). If the user chooses to decline the operation, Buran's invasion stops here. Many users, however, tend to impulsively click on the 'Enable' button without giving it much thought. When this happens, the IQY file downloads a malicious formula which is automatically executed by Excel. The formula will then launch a PowerShell command that downloads the Buran's executable '1.exe.' into the Temp folder.
Figure 3: Buran's Malicious IQY File
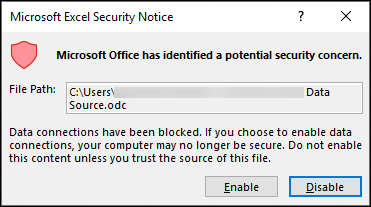 Example of Excel's pop-up message that warns users of potential risks. Source: Microsoft
Example of Excel's pop-up message that warns users of potential risks. Source: Microsoft
Encryption Method
Once the malicious executable is downloaded, Buran will check if the computer system is located in Russia, Ukraine, or Belarus (Figure3). If that's the case, the ransomware will abort its execution. Otherwise, Buran will proceed to execute its malicious payload.
Figure 4: Buran Location Targeting
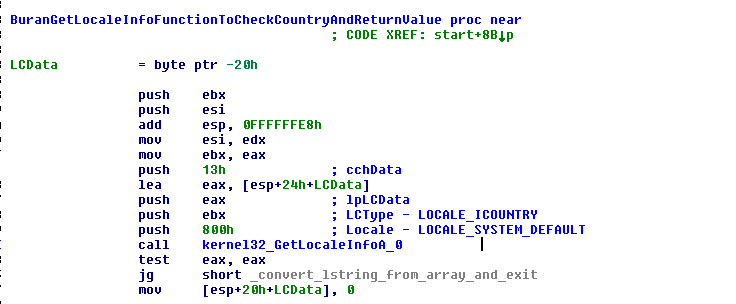
Checking the country of the victim's computer. Source:: McAfee Blog
Researchers point out that Buran could accept special arguments in execution. These specials are features that the affiliates bought or negotiated with the ransomware operators. Such functions can include self-deletion, modification of the extensions Buran adds to the encrypted files, etc.. These arguments get installed during this step.
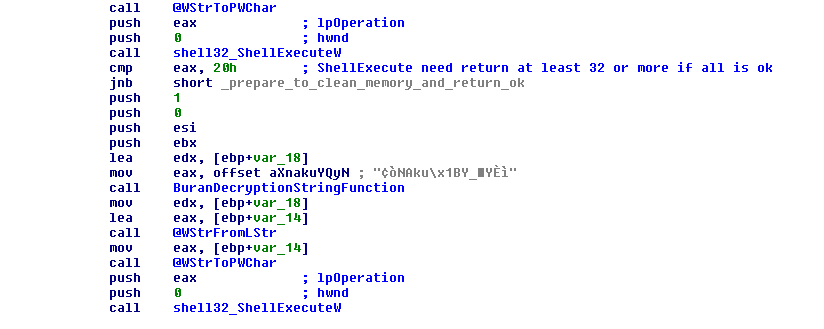
If there are no special arguments, the standard execution will continue as follows: Buran will create a copy of itself with the name 'ctfmon.exe' in the Microsoft AppData folder and will then launch it, as shown in Figure 3.
Researchers at McAfee report that Buran rewrites the registry in a way that hinders the reverse engineering attempts and complicates the malware analysis.
Buran will start the encryption operation by identifying the victim and generating a unique ransom id of the victim. The ransomware will then proceed with the file encryption. Buran will append random numbers at the end of the encrypted files.
How to Protect Yourself from Buran Ransomware
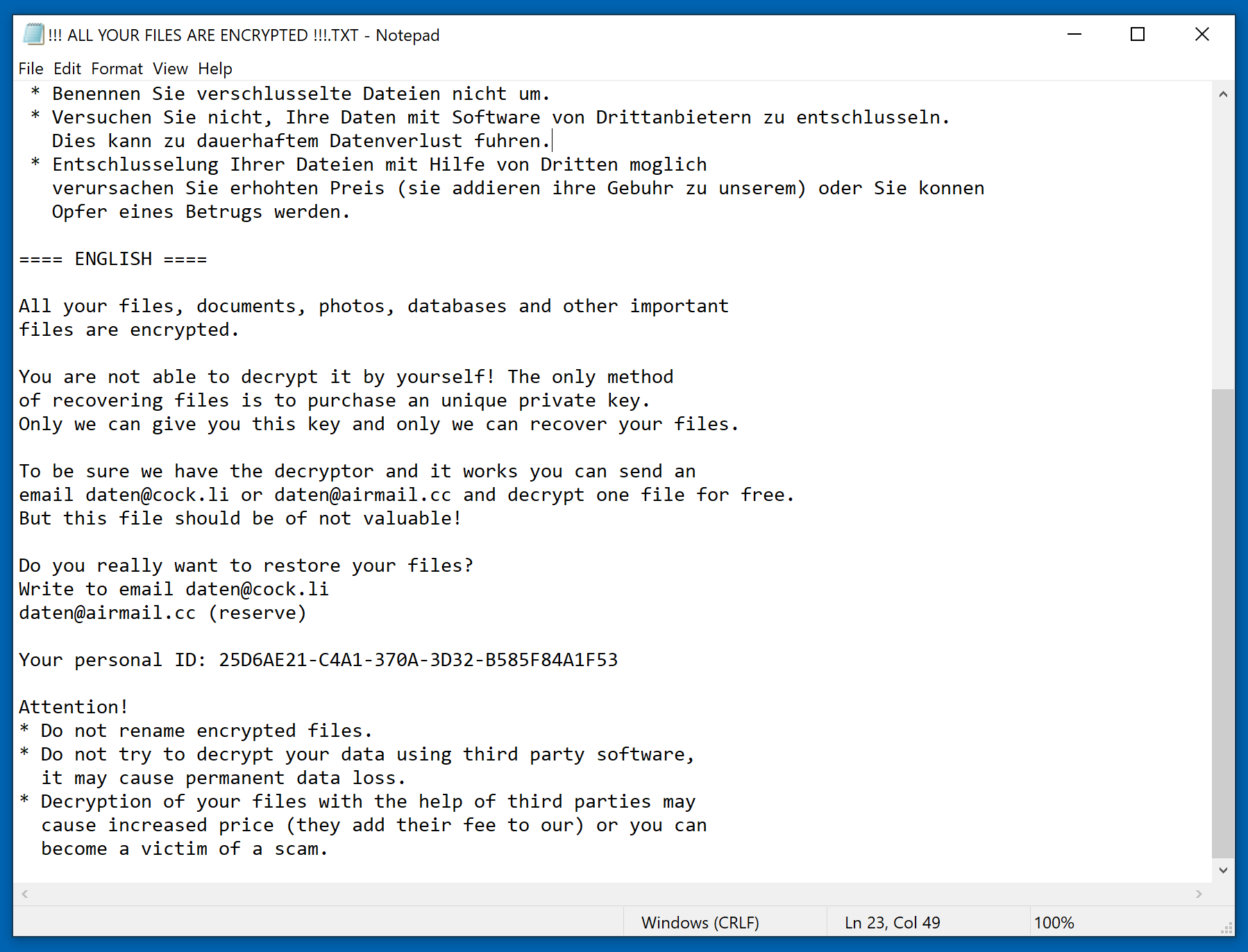
Unfortunately, there is no decrypting tool for Buran ransomware’s encryption. Avoiding infections by Buran by taking a proactive approach is the best way to defend oneself from the ransomware. Since Buran takes advantage of existing vulnerabilities such as CVE-2018-8174, it is essential to keep computer systems updated with the latest security patches. For organizations, training staff to identify suspicious emails can go a long way when preventing Buran and other malware infections. Lastly, keeping backups segregated from the network could help mitigate the damage caused by Buran’s backup deleting capabilities.





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.