
Security researchers at McAfee have detected a cyberespionage campaign attempting to extract confidential information from foreign governments. Researchers warn that the data-exfiltration and surveillance operation is targeting the aerospace and defense sectors.
Attackers use previously-undetected spyware called Torisma to target IP addresses belonging to service providers in Australia, Russia, and Israel, as well as defense contractors based in Russia and India.
The campaign, named "Operation North Star," implements Tactics, Techniques, and Procedures (TTPs), typical for North Korea's threat group Hidden Cobra. According to security researchers, the applied TTP, as well as the use of Visual Basic (a programming language), suggest that the latest attacks are a sequel of 2019 campaigns, which were also aimed at gathering intelligence from key military and defense infrastructures.
Table of Contents
Operation North Star
McAfee's analysis suggests that the latest malware campaign attempts data-gathering malware on victims' machines. The attackers use standard DLL implants that collect basic information that could be useful in classifying the value of potential targets.
However, researchers warn that Operation North Star exhibits a "degree of technical innovation" intended to camouflage the operation and keep it under the radar.
To infect its targets, the campaign relies on spear-phishing emails. The attackers use a series of weaponized documents containing job postings, copied from legitimate recruitments posts, published on a US defense contractor's website.
Figure 1: Attack Overflow
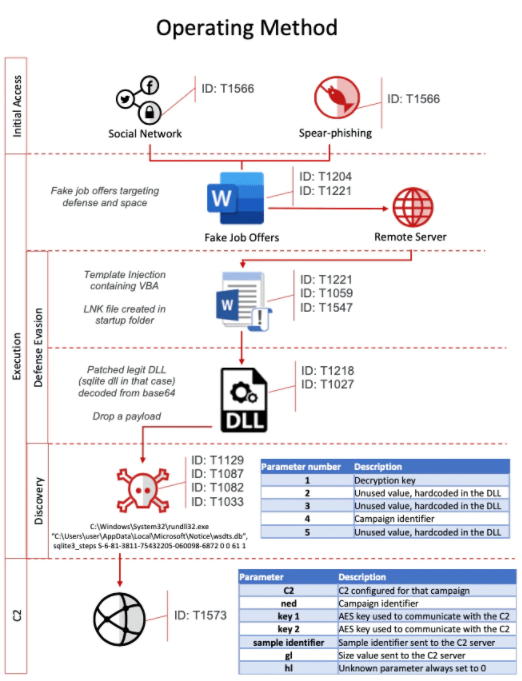
The malicious attachments in the sample analyzed uses a template injection attack that downloads an external Word template containing executable macros.
Second and Third Stage Attack
While the attackers use malicious documents for the initial infiltration, Stage Two of the attack delivers malicious DLL files, designed to spy on the target. The criminals exploit patched SQLite DLLs to gather basic information from its targets, which could be used for identification purposes in the future.
The Third Stage of the attack drops yet more malicious DLLs that are part of legitimate software. Researchers explain that every time a specific function is called with a predefined set of parameters, the corrupted DLL will be activated.
Phase Three of the attack is focused on keeping the malicious operation under the radar. According to the research, to avoid detection, the attackers mimic the User-Agent that is present in the host system. For example, the User-Agent string from a web browser configuration can avoid network-based detection by camouflage the outgoing traffic.
Another interesting camouflaging technique is the implementation of compromised websites located in Italy and the US. Researchers also identified exploited websites owned by an auction house, a printing company, and an IT training firm as Command and Control(C2C) servers for the campaign.
Torisma Spyware
One of the most noteworthy payloads deployed in the latest attacks is a custom developed spyware called Torisma. The threat, which is dropped as a second stage implant, is designed to send and receive information from a command and control (C&C) server.
Figure 2: Inside Torisma Implant
Torisma is designed to monitor for new drives added to the system, as well as to track remote desktop connections. While the threat is focused on active monitoring, it can also trigger payload executions as well.
Figure 3: Torisma Monitoring Loop
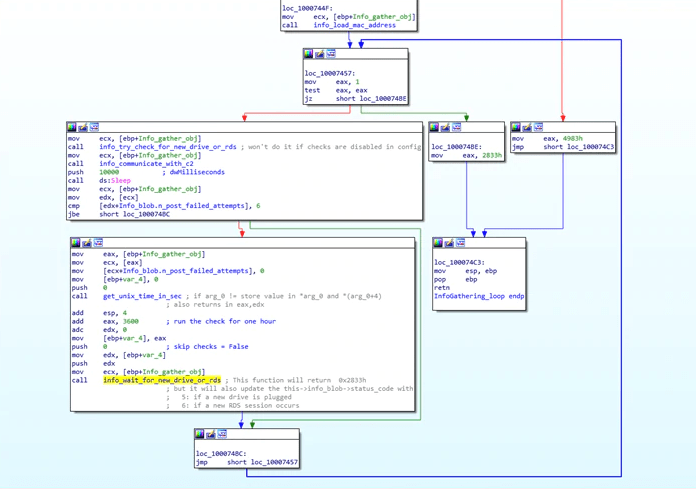
According to researchers, Torisma's end objective is to execute shellcode and to report the results back to the C&C server. Its monitoring loop allows attackers to identify victims, who could be monitored further.





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.