With the COVID-19 pandemic forcing people to work from their homes, cybercriminals are working overtime to make a profit, launching a new ransomware threat every week, if not every day.
At first glance, Vcrypt ransomware appears to follow the classic pattern of corrupting data and extorting the victims for ransom in exchange for a decryption key. What sets this malware apart from other ransomware threats is that Vcrypt's code doesn't have encryption capabilities. Instead, the malware uses a free archiving application named 7-Zip to lock its victims' files saved on the C:\ drive and deletes the data saved on all other drives.
Table of Contents
Infection
Vcrypt travels the web camouflaged as a harmless-looking video driver named video_drive.exe. If a victim is tricked into executing the file, the threat will use a cryptographic key to lock the files on the C:\ drive. It will then proceed to delete all data saved on all other drives, from A to Z.
When video_driver.exe is executed, it will extract the legitimate 7-Zip app and save it as 7za.exe in the %Temp% folder. The ransomware's payload will call the Windows "system()" function and run the archiving app through system commands. Through a series of these commands, the ransomware will utilize 7-Zip's capabilities to compress the user-generated files from the following directories into password-protected archives:
%Username%\Desktop
%Username%\Downloads
%Username%\Pictures
%Username%\Music
%Username%Videos
%Username%\Documents
%Public%\Desktop
%Public%\Downloads
%Public%\Pictures
%Public%\Music
%Public%\Videos
%Public%\Documents
The newly-created files use the same name as the source folders with the additional ".vcrypt" extension attached to them. For example, the files that are saved in the %User%\Pictures folder will be locked in a file named User_Pictures.vcrypt.
The threat actors didn't put too much effort into this ransomware as they hardcoded an easily crackable cryptographic key in the malware's code. Vcrypt uses the Oezfdse6f5esf413s5fd4e6fSQ45R424EDDEZS key to encrypt every archive.
Once the data encryption process is completed, the ransomware will scan all other drives, from A to Z, and delete all files saved on them. It will then drop its ransom note – a file named help.html. Additionally, the ransomware will use Internet Explorer to display the ransom message, which is written in French. The note briefly informs the victim that their files have been locked and urges them to visit a website that supposedly provides more information.
The threat actors chose not to use a Tor or dark web page to host Vcrypt's website. Instead, they used a surface website hosted on a free platform. Unsurprisingly, the website is now removed due to offending content, leaving the victims unable to contact the criminals and negotiate the price for decryption.
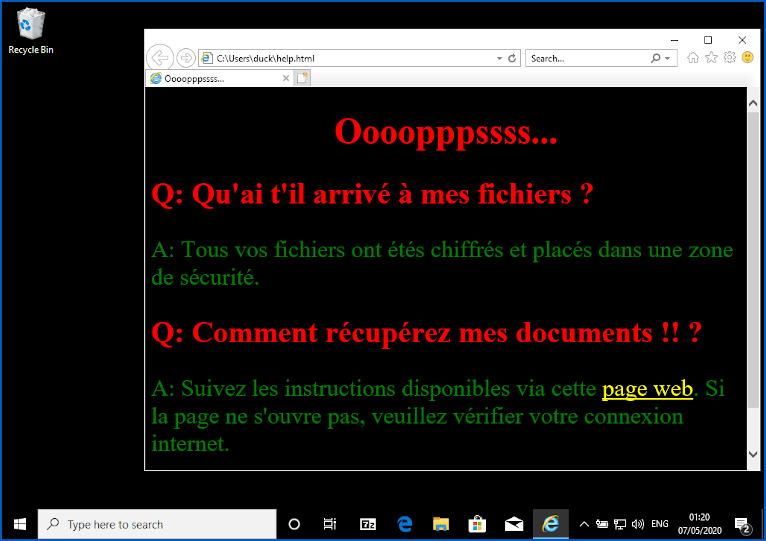
Figure 1: Screenshot of Vcrypt’s Ransom Note
In this image, we can see the Vcrypt’s ransom note displayed in Internet Explorer. Source: Sophos
Ransom note (original text)
Oooopppssss…
Q: Qu'ai t'il arrivé à mes fichiers ?
A: Tous vos fichiers ont étés chiffrés et placés dans une zone de sécurité.
Q: Comment récupérez mes documents !! ?
A: Suivez les instructions disponibles via cette page web. Si la page ne s'ouvre pas, veuillez vérifier votre connexion internet.
Ransom note (machine translation)
Oooopppssss…
Q: What happened to my files?
A: All your files have been encrypted and placed in a security zone.
Q: How to recover my documents !! ?
A: Follow the instructions available via this web page. If the page does not open, please check your internet connection.
Decryption
According to researchers at Sophos, users can decrypt their data manually by installing the 7-Zip application and opening the .vcrypt archives one by one. When the user attempts to export the archives' content, a pop-up window will ask them for a password. All you have to do is to type (or copy-paste) the key, which was used for the encryption: Oezfdse6f5esf413s5fd4e6fSQ45R424EDDEZS.
The files stored on the wiped drives cannot be restored as easily. Sadly, only data backups saved on external devices can retrieve these files.
Conclusion
With the COVID-19 pandemic imposing an unprecedented quarantine, many workers found themselves locked in their homes and forced to turn their living spaces into home offices. The dire situation opened many doors for the cybercriminals who took full advantage of the situation and flooded the web with malware.
Although Vcrypt is rather basic, it could cause quite the stir. Launched on the right computer, this ransomware could hinder essential processes, industrial operations, and even healthcare-related services. Cyber threats shouldn't be taken lightly! The FBI issued an alert, warning that cybercriminal activities are increasing in the unusual situation caused by the Coronavirus pandemic. The best line of defense is the human resource. Users are advised to be vigilant and doubting. The business is encouraged to invest in the computer education of their employees. Of course, a reliable anti-malware solution could also be handy.





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.