VegaLocker is a computer virus from the ransomware trojan, which was first spotted in February 2019. It performs a typical encryption attack, locking the victims' files, requesting a ransom payment to restore them.
Since its discovery, Vegalocker has been responsible for multiple high profile ransomware campaigns around the world. This number grows exponentially if you count all the variants Vegalocker has spawned, such as the Buran and Zeppelin ransomware.
Table of Contents
VegaLocker Has Multiple Vectors of Distribution
VegaLocker is usually distributed via spam email messages; however, there are several other methods for spreading the ransomware.
- SPAM email messages: Hackers would send out infected messages disguised as legitimate notifications from popular internet portals or services. These files are either directly attached or linked in the message body. They can also be uploaded to fake websites developed to impersonate legitimate ones by using similar domain names, certificates, design, and content. Victims would then access these spoofed websites and be tricked into downloading the malware installer.
- Infected payloads: Hackers use different file formats that are infected with malicious code. The malicious documents can take various forms, such as presentations, rich text files, spreadsheets, and databases. As soon as the victims open them, a notification message shows up, asking them to enable built-in scripts. IfThe scripts would then are beginning downloading and executing the malware.
- Application installers: These are malicious copies of legitimate setup files of popular end-user programs that have been modified with the VegaLocker ransomware code. Once opened, the computer is infected with VegaLocker Ransomware.
- Fake user profiles: They are usually posted in community forums or social media accounts. Hackers can utilize both fake or stolen identities to increase the number of victims.
- Malicious browser plugins: Add-ons to the most popular web browsers that are advertised as useful. The malicious plugins are uploaded to the official repositories using fake user reviews and developer credentials. When users install them, they execute their built-in commands and inject VegaLocker Ransomware into the victim's computer.
Experts Rated VegaLocker Ransomware as Critical
Although there is no particular information on the criminals who have created VegaLocker Ransomware, researchers believe that they are very experienced hackers as the threat is rated as "critical." The identity of the individuals who created Vegalocker is still unknown. Security experts believe VegaLocker ransomware was created by Russian hackers, given that its ransom note is written in Russian.
The security analysis shows that VegaLocker targets user-generated files, encrypts tje,, and removes their Shadow Volume Copies to disable recovery.VegaLocker ransomware targets different file types such as documents, databases, media files, etc. The targeted file formats include:
.jpg, .jpeg, .raw, .tif, .gif, .png, .bmp, .3dm, .max, .accdb, .db, .dbf, .mdb, .pdb, .sql, .dwg, .dxf, .cpp, .cs, .h, .php, .asp, .rb, .java, .jar, .class, .py, .js, .aaf, .aep, .aepx, .plb, .prel, .prproj, .aet, .ppj, .psd, .indd, .indl, .indt, .indb, .inx, .idml, .pmd, .xqx, .xqx, .ai, .eps, .ps, .svg, .swf, .fla, .as3, .as, .txt, .doc, .dot, .docx, .docm, .dotx, .dotm, .docb, .rtf, .wpd, .wps, .msg, .pdf, .xls, .xlt, .xlm, .xlsx, .xlsm, .xltx, .xltm, .xlsb, .xla, .xlam, .xll, .xlw, .ppt, .pot, .pps, .pptx, .pptm, .potx, .potm, .ppam, .ppsx, .ppsm, .sldx, .sldm, .wav, .mp3, .aif, .iff, .m3u, .m4u, .mid, .mpa, .wma, .ra, .avi, .mov, .mp4, .3gp, .mpeg, .3g2, .asf, .asx, .flv, .mpg, .wmv, .vob, .m3u8, .dat, .csv, .efx, .sdf, .vcf, .xml, .ses, .qbw, .qbb, .qbm, .qbi, .qbr , .cnt, .des, .v30, .qbo, .ini, .lgb, .qwc, .qbp, .aif, .qba, .tlg, .qbx, .qby , .1pa, .qpd, .txt, .set, .iif, .nd, .rtp, .tlg, .wav, .qsm, .qss, .qst, .fx0, .fx1, .mx0, .fpx, .fxr, .fim, .ptb, .ai, .pfb, .cgn, .vsd, .cdr, .cmx, .cpt, .csl, .cur, .des, .dsf, .ds4, , .drw, .eps, .ps, .prn, .gif, .pcd, .pct, .pcx, .plt, .rif, .svg, .swf, .tga, .tiff, .psp, .ttf, .wpd, .wpg, .wi, .raw, .wmf, .txt, .cal, .cpx, .shw, .clk, .cdx, .cdt, .fpx, .fmv, .img, .gem, .xcf, .pic, .mac, .met, .pp4, .pp5, .ppf, .nap, .pat, .ps, .prn, .sct, .vsd, .wk3, .wk4, .xpm, .zip, .rar.
The infection starts with a security bypass module that scans the local system for the presence of security programs and engines that could block VegaLocker's execution routine. Samples of VegaLocker have been found to look for signatures of the following engines:
Habbo, Rebhip, The Qt Company Ltd, Microsoft Corporation, Delphi Libraries, SMART INSTALL MAKER, InnoSetup, James Jackson-South, Microsoft Visual C/C++ Libraries, libczmq3, Adobe Systems Incorporated, Mercury Interactive, NSIS, Splinterware Software Solutions and StockSharp LLC.
Once detected, the real-time engines will be disabled or removed immediately. After that, VegaLocker will proceed to modify the configuration files of the to the operating system's boot options. Boot options modifications This reconfiguring the ensure the virus runs a virus every time the computer is turned on. Additionally, this will disable access to the recovery boot options and menus, which renders most manual user recovery guides non-working. Depending on the variant, Vegalocker is also capable of removing System restore points, Shadow Volume Copies, and backups, and the victims will be unable to restore their computers without paying the ransom for a decryption key.
Commands used to alter boot options and delete shadow volumes:
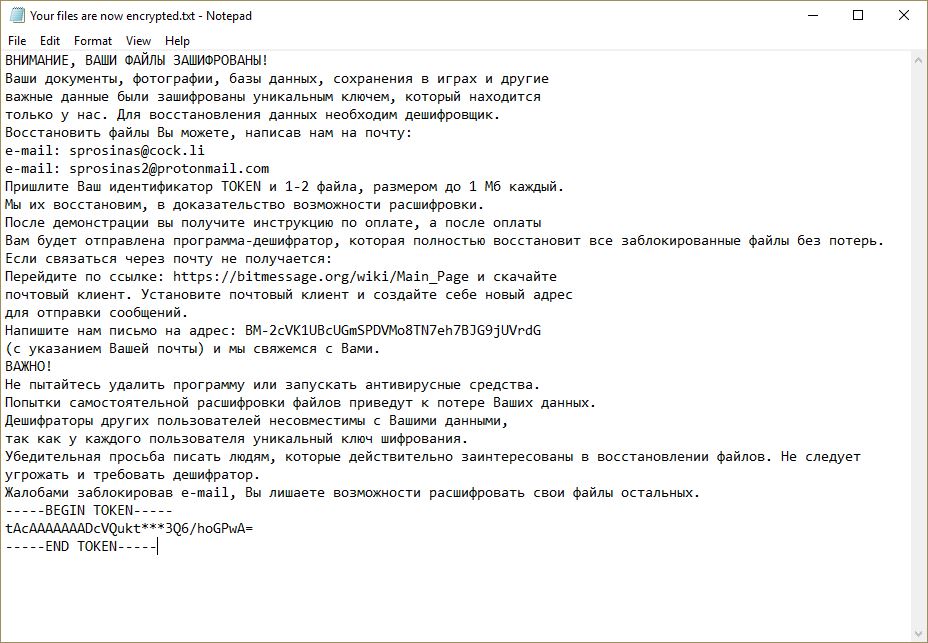
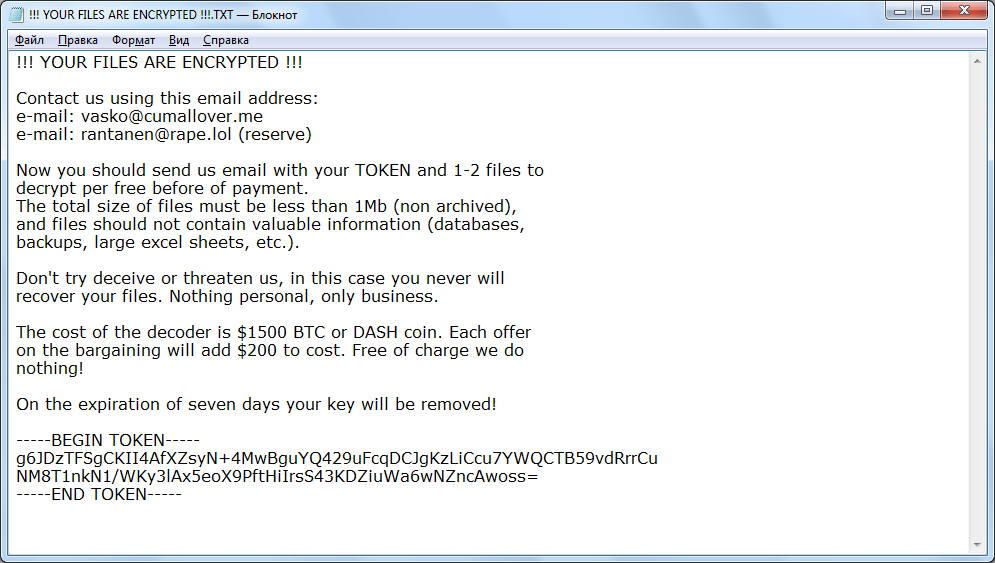
The latest version of VegaLocker combines SHA and RSA encryption algorithms to lock up users' files. Once installed, the ransomware places the blankie (скореевсего образец вируса).exe file in the infected computer from which the dangerous payload could be identified. VegaLocker Ransomware is programmed to escape virtual machine hosts by continually monitoring the running processes in memory for any signs of strings that are related to hypervisors or guest additions. If any of these are detected, the ransomware will immediately stop or even delete itself to avoid suspicion. Apart from collecting personal information used to expose the victims' identities and account credentials, VegaLocker Ransomware is also capable of modifying the Windows Registry by creating entries for itself or modifying existing ones. Usually, VegaLocker causes severe performance issues, which can make the infected terminals unusable until the ransomware is removed. VegaLocker Ransomware has one big difference from other threats of its kind – it does NOT apply any appendix or renames the encrypted files. However, the ransomware does provide a ransom note which is called "Your files are now encrypted.txt" or "ABOUT YOUR FILES.txt" written in Russian. The attackers demand a ransom in Bitcoin and provide email addresses such as sprosinas@cock.li, sprosinas2@protonmail.com, or sup24@keemail.me, sub24@protonmail.ch. If victims do not contact hackers within three days, their files could be permanently lost.
The creators of VegaLocker Ransomware have released another similar version of the threat that also uses the ABOUT YOUR FILES.txt ransom message to inform victims about the secret encryption process. Unfortunately, no free decryptor is currently available for recovering the files encrypted by VegaLocker Ransomware. Cybersecurity experts advise victims to avoid contacting the attackers or paying the ransom and restore the data loss by replacing it from backups whenever possible.
VegaLocker Ransomware Does Not Apply Any Appendix to Encrypted Files
There is No Free Decryptor for VegaLocker Ransomware





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.