Researchers have discovered an all-new addition to the Vega ransomware family. The new strain, dubbed Zeppelin Ransomware, has an arsenal of configurable features that allow hackers to tailor it to their needs.

The analysis revealed that the new version of the ransomware was detected in early November of this year. Since then, incidents have been rampant, with researchers describing the attacks as "carefully chosen." Unlike the early variants of Vegalocker, which w targeted Russian users, Zeppelin has been modified to attack European and American companies. Incidents involving Zeppelin have mostly been limited to IT and healthcare companies in Europe and North America.
Table of Contents
A Customizable Ransomware that Caters to the Masses
Like its predecessor, Zeppelin ransomware is a Delphi-based ransomware with multiple configuration options that enable a range of different features, depending on the attacker's intentions and the victims in question.
Zeppelin can be deployed in a range of forms, including as a DLL or EXE file, or as part of a PowerShell loader. No matter how it is delivered, it offers the following functions;
- Startup – Ensure ransomware persistence on the target computer
- IP Logger – Track locations and IP addresses of victims
- Delete Backups – Deletes backup copies and disables file recovery in order to prevent users from getting their files back without paying the ransom
- Task-Killer – End specific tasks
- Auto-Unlock- Automatically unlocks files that are locked during the encryption
- Melt – Used to self-destruct files through notepad.exe
- UAC prompt – Attempts to run the ransomware as an administrator, giving it elevated privileges and letting it do more damage
Outside of allowing attackers to customize the Zeppelin's features and targeted file types, the Zeppelin builder will enable attackers to write their own ransom note and create their own text file. This explains the multiple version of ransom notes attributed to Zeppelin. Some of them were short and generic messages, while others were more elaborate that seemed tailored to the organizations or individuals they were sent to.
Multiple Levels of Obfuscation to Avoid Detection
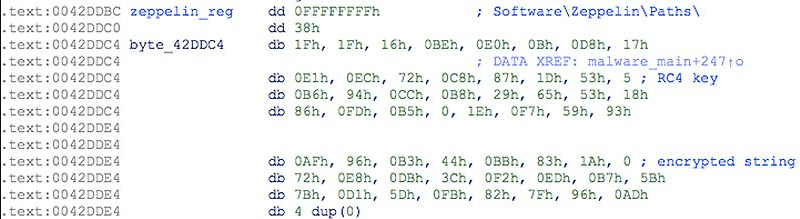
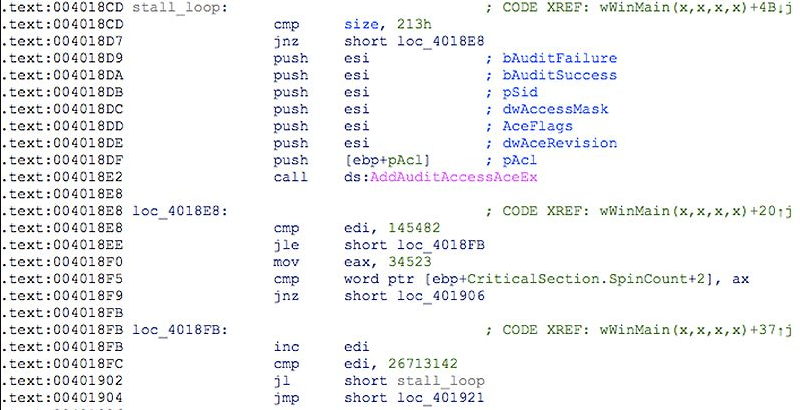
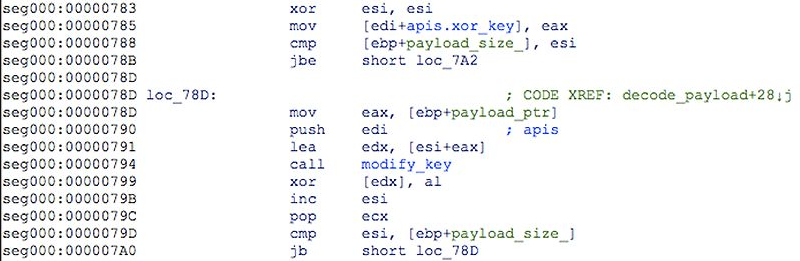
Zeppelin is able to evade detection by using several layers of obfuscation to avoid detection by antimalware tools. This includes using pseudo-random keys, different-sized code, encrypted string, and delays in execution to outrun sandboxes, among other methods. Estimates suggest that around a third of antivirus programs (30%) are unable to detect Zeppelin.
How Zeppelin Infects and Encrypts A System
IT is believed that certain remote desktop applications are used to execute powershell commands and initiate downloading Zeppelin's payload. Another possible vector of infection can be phishing emails with hidden payload droppers.
Zeppelin uses a standard combination of file encryption; Randomly generating keys for the files and asymmetric encryption to protect the session key. In this case, the ransomware will create a pair of 512-bit RSA keys for the victim. Both of the victim's public and private key will be encrypted by the attacker's 2048-bit public RSA. As if that was not enough, the encrypted keys will be further encoded by using a random 32-byte RC4 encryption algorithm.
After the creation and encryption of the victim's key pair, Zeppelin will begin enumerating files across the systems drives and networks. If a file's extension is not on the exclude list, the file will be encrypted using an AES-256 encryption algorithm and encrypt the resulting key with the victim's previously generated public RSA key.
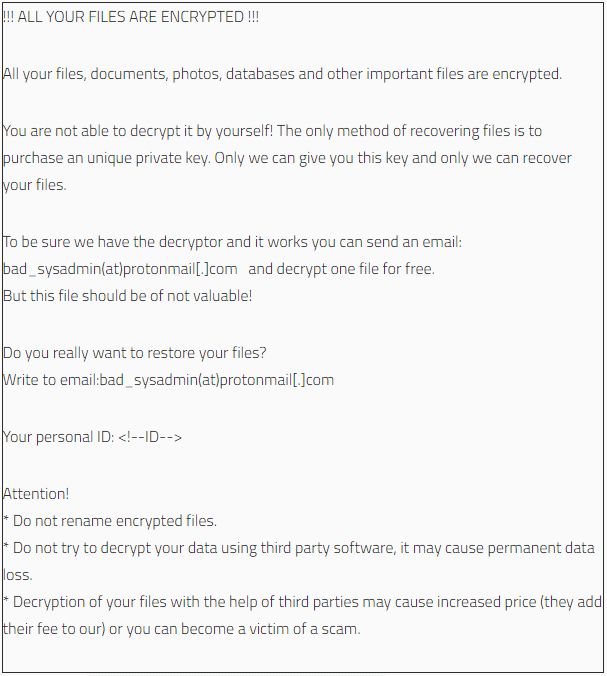
The ransomware places the ransom note on the system and will display it to users after their files are encrypted.
Figure 2.1: Zeppelin's Ransom Note
Zeppelin's ransom note presented to the user after encryption. Notes vary depending on the cybercriminal distributing the malware. Source: gbhackers.com
So far, all known ransom notes have instructed users to contact their attacker at a specific email address and use their personal ID number to arrange for the release of their files.
Designed to Target Western Countries
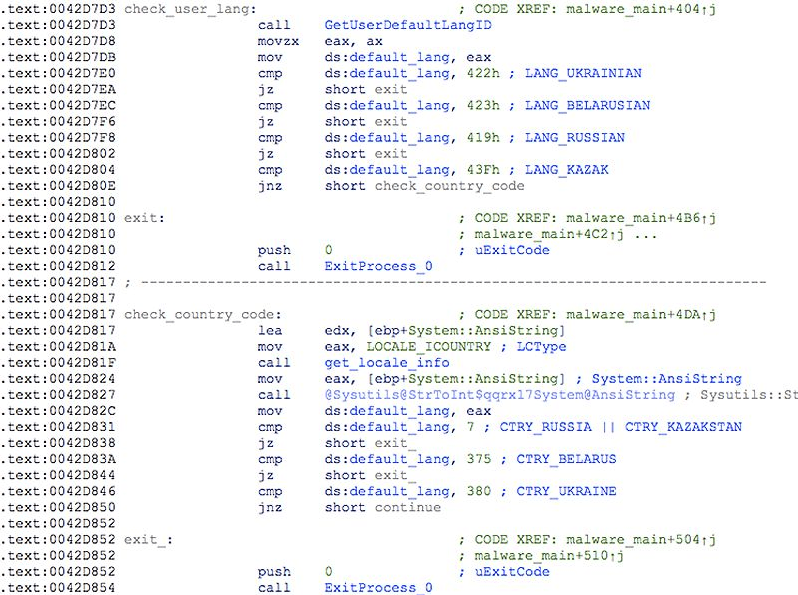
Unlike its Vegalocker predecessor, Zeppelin doesn't target computers from Russia, Belorussia, Kazakhstan, and Ukraine. Instead, the new Zeppelin strain has been designed to target western and European countries. Victims of the Zeppelin ransomware campaign have mostly been IT and healthcare companies in Europe and North America.
Figure 3.1: Checking for Whitelisted Countries
Zeppelin will not run if the infected system is located in one of the whitelisted companies. Source: https://threatvector.cylance.com/
The fact that Zeppelin ransomware targets indiscriminately, except for Russian users, would suggest that a different group is behind its resurgence. Given that underground hackers would offer Vega ransomware as a service, researchers with BlackBerry Cylance, who discovered the ransomware, believe that it was either developed from bought or stolen assets or that it has found its way into the hands of other users.





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.