While some hackers develop malware such as ransomware to make a profit, others just want to see the world burn. To that end, enter the wiper class of malware, a malicious program whose sole purpose is to destroy your files.
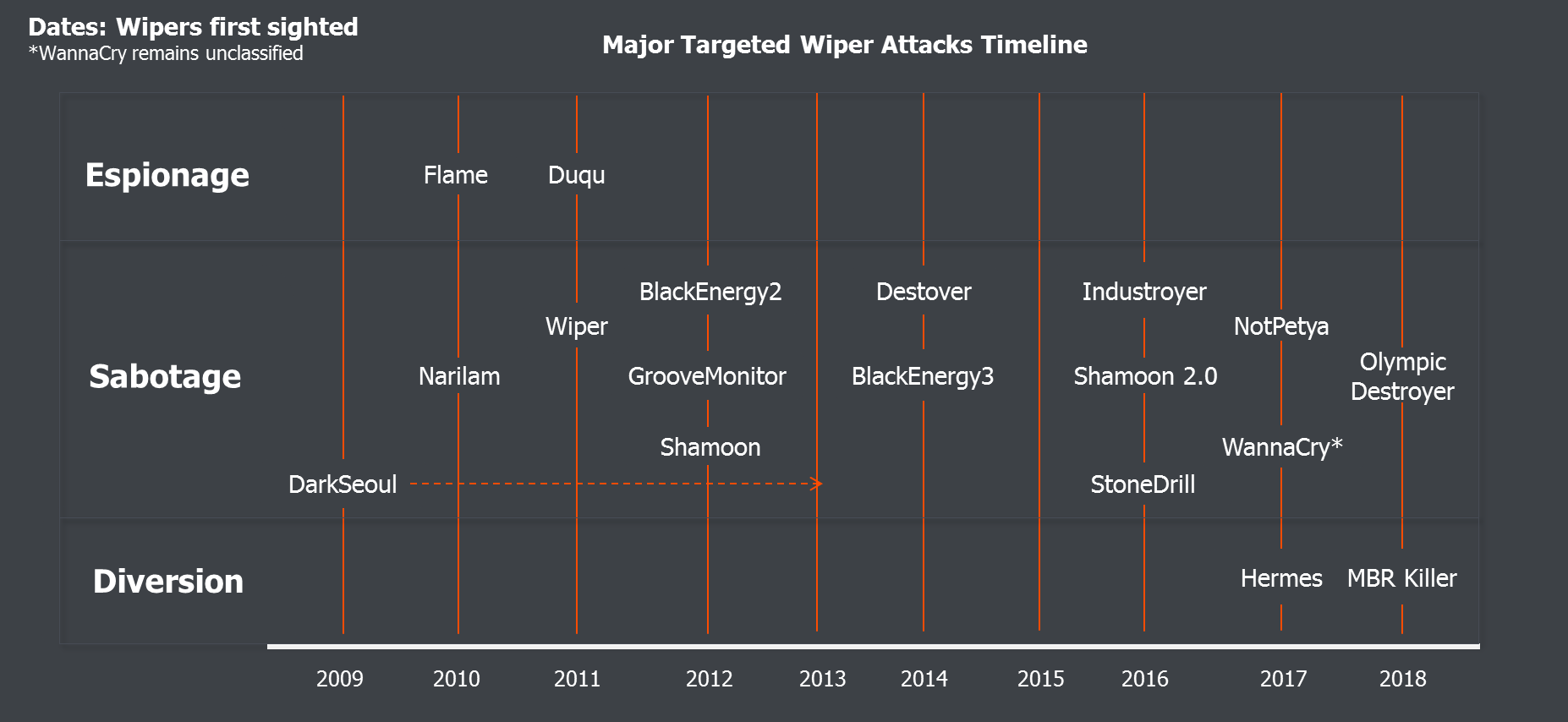
The initial instances of the wiper type malware were first spotted in the Middle East in 2012 and South Korea in 2013. However, wiper attacks did not come into prominence until around 2014 due to a number of high profile cases involving Wiper malware. That same year, the FBI issued an emergency "flash alert" to companies, forced by the severe malware attacks against the U.S. The FBI alert marked the attack against Sony Pictures Entertainment as the first wiper malware attack in the USA.
Figure 1.1: Fake Wiper Ransom Note
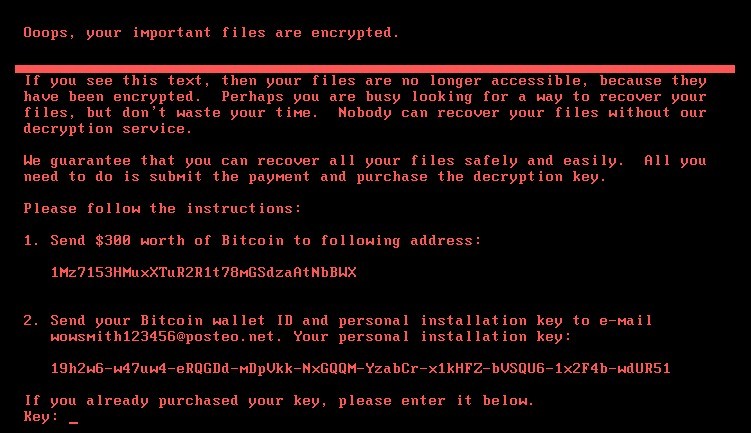
A fake ransom note used by wipers in order to disguise themself as ransomware. Ransomware or wiper, if you see this note, then you're in for a very bad day.
Table of Contents
Wipers are a Rare and Highly Destructive Malware
The security firm Kaspersky Lab describes wipers as one of the rarest types of malware. Due to its ability to wipe hard drives and even BIOS flash memory, a wiper is a malicious program with "highly destructive" potential. Researchers also stated that infections with wiper tend to lead to expensive and continuous repairs. In the vast majority of cases, and the affected data is often impossible to be restored.
Wiper Malware vs. Ransomware
Unlike ransomware, which is capable of decrypting the system’s files after the ransom is paid, the Wiper malware was developed to permanently encrypt, and essentially destroy a system’s data. Thus, this type of malware is considered even more dangerous than ransomware.
Figure 2.1: Ransomware and Wiper Comparison
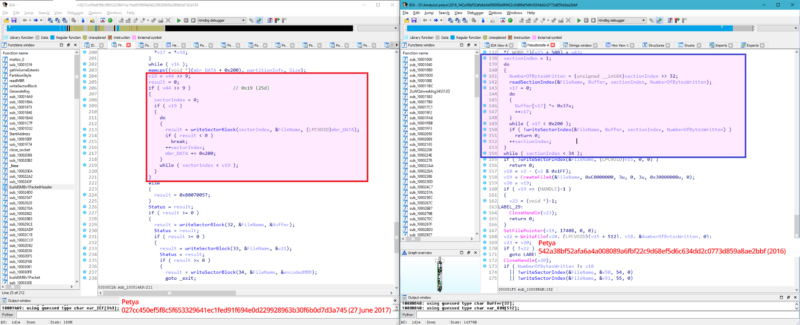
This image shows a comparison between Petya Ransomware (left), and NotPetya (right), a variant of the former. We can see how the modified code to convert NotPetya into a wiper malware. Source: blog.comae.io
Usually, wipers have three targets: files, the boot section of the operating system, and backups. Often, wipers affect the files partially, rendering them unusable, while in other cases, wipers affect specific files according to their type or parameters.
Figure 3.1: Wiper Master Boot Record Process
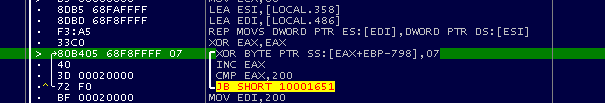
Wiper program NotPetya using the XOR logic process to encrypt the MBR. Source: fortinet.com
Similarly to ransomware, wipers can encrypt different key points of the disk drive, however, they provide no decryption key for their “key-less” encryption method.
Some Wiper variants are also capable of targeting the Master File Table (MFT). The MFT stores information about every file on the computer including creation date, creation date, access permissions, and disk location. Once the MFT is damaged, the files stored on a disk cannot be restored. This feature makes it practically impossible to restore the system’s files even with advanced recovery tools.
Variants of the Wiper Family
One of the more famous varieties of wiper malware was the Shamoon malware that was employed between 2012 and 2016. It was used to attack Saudi energy companies in particular. It used a commercial direct drive access driver called RawDisk to access files. The original malware used a picture of a burning American flag to overwrite files, while the 2016 variation used a picture of the body of Alan Kurdi.
One of the most damaging wiper variants, or any other malware, is the NotPetya malware 2017, which caused over $10 billion of damage worldwide. Like any ransomware, NotPetya would demand a ransom with the promise of restoring the victim’s encrypted files after the payment is made. However, after analyzing the source code of NotPetya, it became clear that hackers never had a decryption key.
Wiper malware came back into the public eye with the recent discovery of a new strain of malware called ZeroCleare. The malware was uncovered by researchers at IBM X-Force. The malware, which is being used to attack energy companies and industrial companies in the Middle East, was reportedly created by APT34 and xHunt; two Iranian hacker groups with alleged ties to the Iranian government. Iran is also suspected of carrying out a cyberattack against a Saudi oil company with a new wiper variant named "Dustman".
Experts Suspect North Korean Launched Wiper Attacks
After the malware attack against Sony Pictures Entertainment, security researchers focused on the previous Wiper malware attacks attributed to North Korea. According to the FBI, some components used in the Sony attack were developed using Korean-language tools, suggesting that Wiper Malware has a North Korean tie.
According to the information security consultant Brian Honan, who heads Ireland's computer emergency response team,"at this stage it is not possible to identify and attribute who is behind these attacks."
Anyone could have repurposed previously seen wiper malware for these attacks."There are samples of wiper-type malware available online that those with the right skills and motivations could reuse or include in their own malware."
The Wiper Threat is Growing
The cost of these attacks is colossal. Companies that are hit by these destructive attacks can take a long time – perhaps even months – to fully recover from them. It takes an average of 512 hours for a response team to mitigate the damage but that’s just the average. It can sometimes take far longer. It also has a huge financial cost. The average wiper attack leaves a company $239 million out of pocket.
Unfortunately, there is no doubt that the Wiper threat keeps growing. According to a report by Europol, there is a huge possibility of a potential rise in the number of wiper malware attacks in the near future.





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.