With the World Health Organization officially declaring the COVID-19 infection a pandemic, numerous cybercriminals have taken the opportunity to exploit the historical event and use it to make a profit.
In the past two months, waves of cyberattacks themed around the Coronavirus strain have been flooding both desktop and mobile users.
The operators of the inactive trojan Zeus Sphinx also couldn't resist the urge to jump on the Coronavirus bandwagon. An ongoing malspam campaign has been detected to target bank customers in the U.S., Australia, and Canada.
Figure 1: Countries Targeted by Zeus Sphinx
 Caption: The chart shows the US and Australia as the top countries targeted by Zeus Sphinx malware. Source: IBM X-Force
Caption: The chart shows the US and Australia as the top countries targeted by Zeus Sphinx malware. Source: IBM X-Force
Table of Contents
Zeus Sphinx is back after years-long rest
Zeus Sphinx (also known as Zloader and Terdot) resurfaced after nearly three years of absence with a new campaign. This new campaign takes advantage of the news around government relief payments or stimulus checks.
Although some malicious activity was detected in December 2019, a significantly increased volume of malspam was detected to spread the trojan in March 2020. Experts believe that the first spam wave was just a test.
The recent malspam campaign, which is themed around the government relief payments, reportedly uses a weaponized document called "COVID 19 relief." The subject of the messages is related to Coronavirus, targeting users in the US, Canada, and Australia.
Researchers report that the used variant of the malware is not significantly different from older samples.
What is Zeus Sphinx
Sphinx is a modular malware that is based on the leaked source code of the infamous banking trojan Zeus v2. On a basic level, the threat is a credential-stealing malware that targets a wide range of banking and financial web platforms.
Zeus Sphinx first emerged in August 2015, when it was used in attacks targeted at major financial entities in the U.K. The campaign quickly expanded its reach, affecting the banking sectors in North America, Brazil, and Australia.
IBM X-Force researchers, who analyzed the new Zeus Sphinx campaign, report that the latest malware variant is not much different from the original threat. Sphinx is programmed to corrupt its victims' web browsers and to take control of the content that they display. The trojan manipulates its victims into sharing sensitive personal and financial details through the use of a wide variety of web injections and social engineering tricks.
The trojan uses web injections (malicious scripts) that create various form-type windows and boxes that mimic the design of the target websites. Cybercriminals use social engineering to trick their victims into filling these fake forms. Such attacks steal sensitive information, including usernames and passwords, authentication codes, email addresses and phone numbers, personal and credit card details.
Malspam campaign details
Zeus Sphinx spreads through a malspam campaign that plays on COVID-19 hysteria. The campaign uses government relief payments as a lure. The attackers have designed an email message that plays on the subject, tricking their victims into downloading a weaponized document called "COVID 19 relief."
Figure 1: Malspam playing on government relief payments.
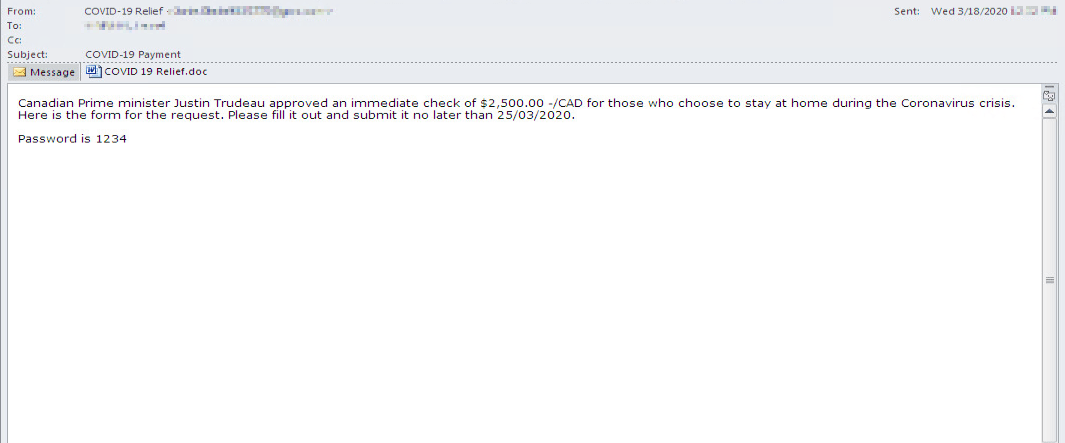 Here, we can see the malicious email that lures its readers into downloading Zeus Sphinx. Source: Security Intelligence
Here, we can see the malicious email that lures its readers into downloading Zeus Sphinx. Source: Security Intelligence
When the user opens the provided password-protected document (a .doc or .docx file), a message will ask permission to enable the "Editing" mode of the user's file viewer. What most users don't realize is that this mode supports macros (macroinstruction scripts). Users give their permission for the macros to run automatically by enabling Editing Mode.
If the user falls into the trap, malicious macros create a folder under the %SYSTEMDRIVE% directory. A batch file is then dropped and executed in the newly created folder. This operation will result in a new VBS file being written in the same folder.
The new VBS file is then executed. The VBS file hijacks the legitimate Windows OS process Wscript.exe and uses it to create a communication channel with a cybercriminals-operated command and control (C&C) server. This operation will fetch a DLL executable, which is the main body of the malware.
Just as with previous campaigns, the executable of Sphinx gets saved into the %SYSTEMDRIVE% folder. Regsvr32.exe will then be used to initiate the installation of the Sphinx DLL.
Sphinx Technical details
Once the malware infects the computer, it creates a hollow process called msiexec.exe and will inject its code into it.
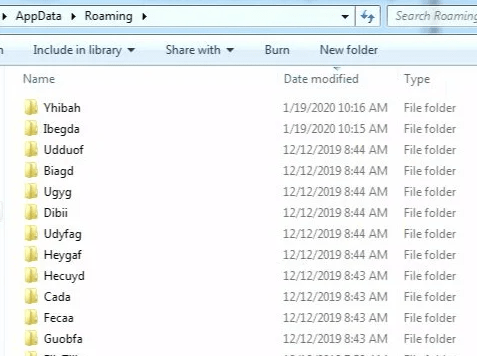
The malware will create an executable file in a new folder under %APPDATA%. This file will later have its extension changed so that it can be used to establish persistence for the malware, ensuring it stays on computers and runs automatically.
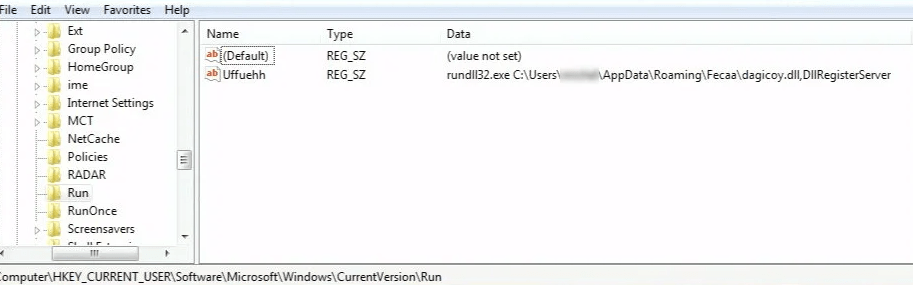
Sphinx also creates ten additional malicious folders under %APPDATA%. The trojan uses them to create a run key in the registry that links to the newly created DLL file under %APPDATA%. Experts explain that this is a persistence method that executes the DLL file through the uses of Rundll32.exe with Dll RegisterServer as an argument.
Additionally, the malware creates two more registry entries under HKCU\Software\Microsoft, each one containing a key that holds a part of the malware's configuration.Sphinx ads multiple registry keys not only to establish persistence but also to have the ability to manage its configuration over time.
Experts state that to stay undetected by antivirus programs, Sphinx uses a digital certificate to sign and validate its code when injected into browser processes. Additionally, the malware uses dynamical names that differ on each deployment.





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.