The logistics giant Toll Group was forced to shut down its IT systems on January 31 due to a severe malware attack caused by the Mailto Ransomware. The incident compromised around 1,000 systems affecting local and global deliveries across Australia. Shortly after the security breach, the Australian Government issued a Mailto Ransomware warning alongside a list of recommendations for managed security service providers (MSSPs).
Table of Contents
What is Mailto Ransomware
Mailto (also known as NetWalker) was discovered by cybersecurity researcher GrujaRS and belongs to the KoKo Ransomware family. According to security experts, Mailto Ransomware is capable of encrypting users' files, making them unusable.
The ransomware encrypts data and renames files with the developer's email address, adding an extension that includes the user's unique ID (e.g. ".e85fb1"). For instance, "1.jpg" might be renamed to "1.jpg.mailto[Hamlampampom@cock.li].e85fb1".
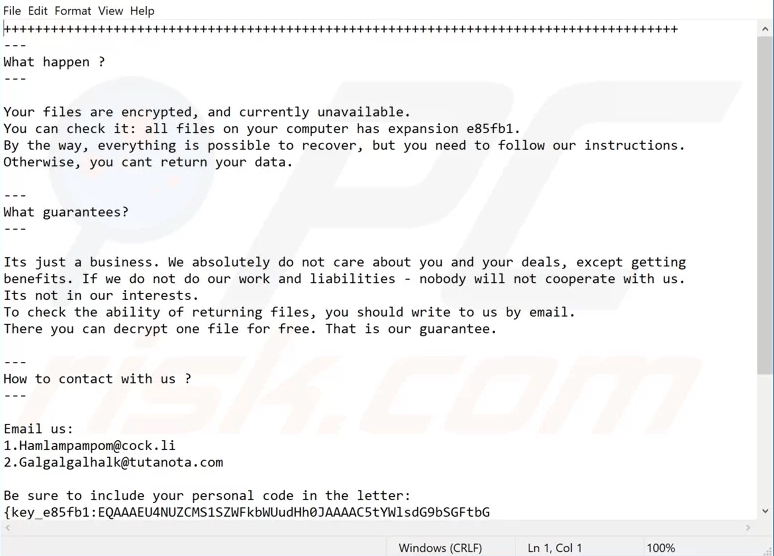
When the encryption process is complete, Mailto Ransomware creates a text file in the format "victim' s_ID-Readme.txt" (e.g. "E85FB1-Readme.txt") on the victim's desktop, as shown below.
Figure 1: Image: Mailto Ransom Note
Mailto ransomware generates a text file containing instructions on how the user can pay to decrypt his files. Source: pcrisk.com
The ransom note informs victims their files are locked and tells them to contact the attackers responsible for their files' encryption. The cybercriminals can be contacted via the email addresses provided in the ransom note, which will tell them how to decrypt their files and/or pay the ransom.
Each user whose files were infected by Mailto Ransomware receives a unique ID/personal code. The IDcode can be found within the ransom note and must be included in the email response. In addition, ransomware victims are allowed to attach one file for free for decryption by the attackers. If victims fail to pay the ransom, their files will remain encrypted and inaccessible.
How Does Mailto Ransomware Infect Computers
There are multiple ways of distributing ransomware. Usually, Mailto is spread via spam campaigns, untrustworthy download channels, software activation tools, fake updaters, and trojans.
Ransomware is also spread through email attachments such as executable and archive files, JavaScript, Microsoft Office, and PDF documents, etc. The malicious emails are sent via large-scale spam campaigns and are usually marked as "official" or "important".
Mailto Ransomware could be also distributed through untrustworthy download sources. Examples of these include Peer-to-Peer sharing networks (e.g. BitTorrent, Gnutella, eMule, etc.), free file hosting websites, third party downloaders, and other sources.
Often, software activation tools install malware rather than activating licensed software. Fake updaters exploit security flaws and install malicious content.
Updated Version of Mailto Ransomware Has Been Released
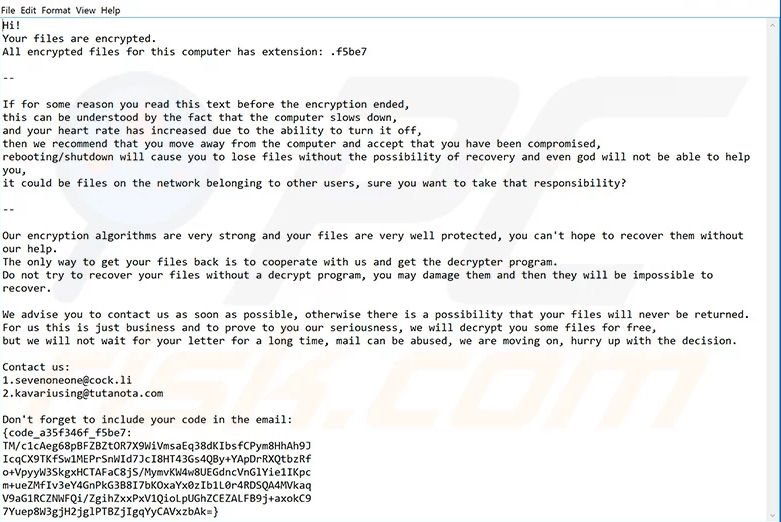
The malware researchers found that an updated version of Mailto Ransomware has been released. Its behavior is virtually the same, with the only difference between the old and the new ransomware variant being the email addresses and message provided in the ransom note. The updated ransom message is shown below.
Figure 2: Mailto Update Ransom Note
The updated version of Mailto ransomware contains different ransom note. Source: pcrisk.com
Mailto Ransomware Targets Enterprise Networks
The Australian Cyber Security Centre (ACSC) has limited information about the initial intrusion vector for Mailto infections. However, the experts have come to the conclusion that the ransomware targets enterprise networks in particular to generate huge revenues.
The company's files usually contain various sensitive data such as customers' personal details, product information, information about employees, etc. For that reason, it is more likely that companies will pay the ransom for the decryption, making blackmailing much easier.
According to the ACSC, there is a proof that developers of Mailto Ransomware have used phishing and password spray attacks, and then used compromised accounts to send further phishing emails to users' address book for spreading the malware.
Guidelines to Fight Mailto and Other Ransomware
Due to the increased number of Mailto and other ransomware attacks against businesses, the Australian Government has issued the following precautionary measures for computer users:
- Keep your anti-virus software and other security tools installed on the systems updated for detection and prevention of the spread of Mailto ransomware.
- Patch the servers regularly to restrict the lateral movement of ransomware attacks within a network and limit the number of hosts impacted after a successful infection.
- Maintain offline backups (e.g., cloud backup) of critical data, which allows faster recovery in case of a ransomware attack.
- Apply content filters on email inboxes to prevent malicious content from reaching users and thus reducing the chance of a possible compromise.
- Use network segmentation to partition the larger networks into smaller sections for segregating communications between specific hosts and services.
- Draft an incidence response plan for quick response in the event of a ransomware attack.
- Educate your employees and users to improve cybersecurity awareness and make them cyber ready.
Unfortunately, the security experts believe that Toll Group will hardly be the last victim of ransomware attacks this year, so people should secure their systems before it's too late.





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.