
Many people continue to use Docker daemons even though they are known to be vulnerable to malware attacks. Unsurprisingly, new malware threats pop up daily, exploiting these weaknesses for criminals' profit. Cetus, a new cryptojacking worm, was recently reported by security researchers at Palo Alto Networks Unit 42.
According to the research, the threat poses as legitimate binaries to sneak into Docker environments. Cetus infiltrates computers through the Portainer interference managing tool. The malware will impersonate binaries and run them through the tool to reach multiple Docker environments. Once on the system, the threat's next step is to deploy its cryptominer and disguise it as a binary called docker-cache.
Researchers report that Cetus uses a new version (v5.5.3) of one of the most popular Monero cryptominers, XMRig. Due to its reputation of often being exploited for malicious purposes, this miner is blacklisted by many cybersecurity applications. Hence, it is not surprising that Cetus' creators have put a lot of effort to obfuscate the cryptominer and prevent unwanted detection.
Malware structure
According to the research, Cetus uses a simple yet effective infection mechanism. The threat will use Masscan to scan subnets for Docker daemons. If it detects these daemons, the malware will use the Docker command-line interface (CLI) tool to send requests to the daemon's REST API.
The malware will use the command docker -H <victim> ps -a to make sure that the Docker is exploitable and not infected. It will proceed to run a new container of ubuntu:18.04 from the Docker Hub and will then update the Package Manager list.
The command docker -H <victim> exec <name> apt-get install masscan docker.io will use the updated Package Manager to install Masscan and Docker. The malicious Portainer and docker-cache will then get copied into the container.
Cetus will then attempt to establish persistence by adding itself to /root/.bash_aliases. This operation will allow the malware to run every time the root starts a bash session or the container restarts.
Finally, the command docker -H <victim> restart <name> will restart the container and run Cetus.
Main functions
Cetus has a rather simple architecture. This malware contains only two main functions: miner_start and scan_start.
The miner_start function logs Cetus' actions by opening /var/log/stmp.log. It will also open the cryptominer, which will hijack the victim's computing resources and utilize them to mine Monero.
The core function of Cetus is the scan_start function. It is designed to spread the malware by scanning the subnet. This function will pick a random 16-bit subnet and will run Masscan detect Docker daemons on port 2375. If it finds a target, the function will deploy the Docker CLI tool to start the infection process.
Figure 1: Cetus Infection Mechanism
 This diagram illustrates Cetus’ infection mechanism. Source: Palo Alto Networks
This diagram illustrates Cetus’ infection mechanism. Source: Palo Alto Networks
Interestingly, for every newly infected Docker, the malware will select a new name for the container. Researchers discovered that Cetus has two lists of eight names each. The malware will pick a random entry from the lists and match them to create unique names for the container.
Figure 2: Container Names
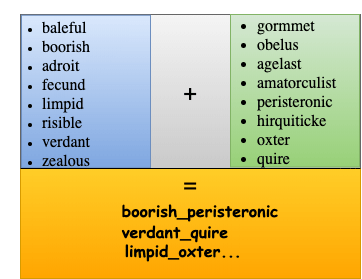 In this image, we can see how Cetus matches list entries to create new container names. Source: Palo Alto Networks
In this image, we can see how Cetus matches list entries to create new container names. Source: Palo Alto Networks
Cetus will run its miner with the name as an argument. As the miner adds itself to the mining pool, the threat actor will receive information about the mining process, which will allow them to classify each individual cryptominer and create statistics about the campaign.
Researchers believe that this managing mechanism is included to establish the foundations for more complex attacks. Furthermore, as Cetus was linked to another cryptojacking campaign that targets AWS credentials and Docker daemons, researchers warn that these new attacks are a part of an alarming trend of sophisticated attacks on the cloud.





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.