DeathRansom was a little known ransomware that faked encrypting user files. Now, after an overhaul by its creator, this nefarious ransomware can permanently encrypt your files and extort your money.
Table of Contents
A Slow Start Kept DeathRansom Under the Radar
DeathRansom showed up at the beginning of 2019. When the ransomware was first introduced and distributed, it would pretend to encrypt the files in a system. However, researchers and users alike discovered that they could easily get access to their files again by removing the .wctc extension.
After several improvements by its creators, the malware is infecting victims’ machines again and holding their data at ransom. This time, unlike its first iteration, DeathRansom is fully capable of encrypting your files.
The initial spike of users affected by DeathRansom began around November 20th. Yet, judging by the progressive growth of malware victims over the past 30 days, it is almost sure that a new distribution campaign is underway.
While there haven’t been as many infections as the earlier days, reports of DeathRansom attacks continue coming in. This means that there is likely still an active campaign distributing the ransomware.
The Revamped DeathRansom is Now a Serious Cyber Threat
Unlike with the non-encryption DeathRansom, the new working version doesn’t add an extension to the encrypted files. Instead, the data of the file is what is encrypted. Now, the only way to identify which files have been encrypted is by the ABEFCDAB file marker added to the encrypted data.
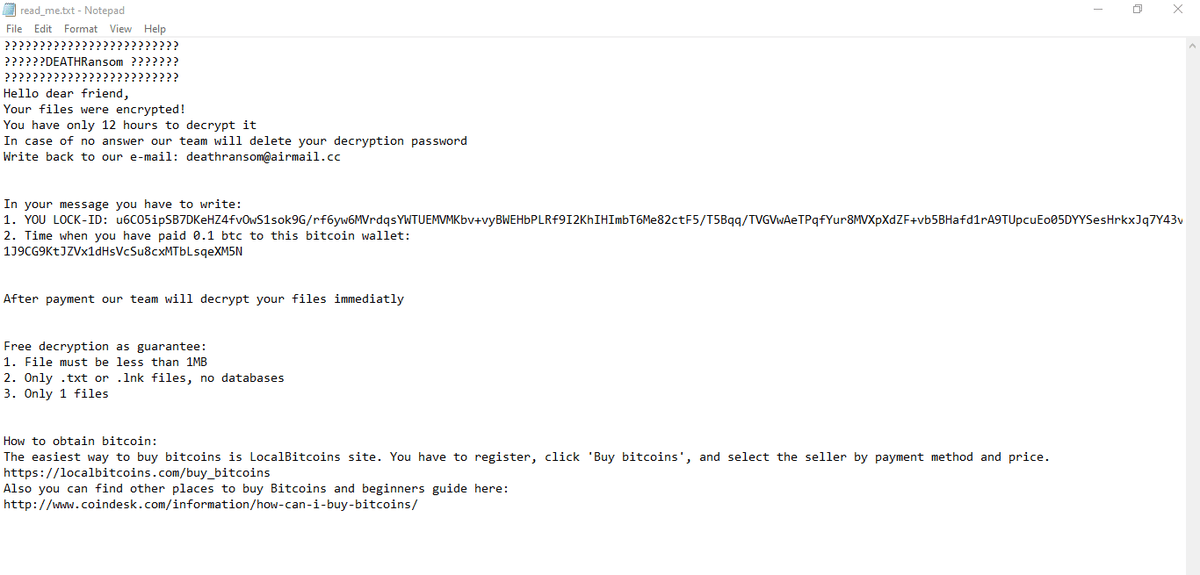
The ransomware creates a ransom note in folders where encrypted files are. The ransom note, called read_me.txt contains a unique “LOCK-ID” and an email address. Victims are supposed to email the address and quote their unique LOCK-ID in order to get their files unencrypted.
At this point, there is no information on how DeathRansom ransomware is being distributed. Some possible methods used to spread the malware are the traditional methods used by hackers such as phishing emails, drive-by-download, or Trojan payload droppers. One thing that has been noticed about the victims of DeathRansom is that they have also been hit by the STOP Ransomware. This was noticed in a Reddit post and with several submissions to ID-Ransomware with victims uploading their DeathRansom ransom note and a STOP Djvu encrypted file in the same submission. Given that STOP is distributed as part of adware bundles and cracked software and games, it’s possible that the two ransomware are connected and DeathRansom could be distributed in a similar way. Like most ransomware, DeathRansom attempts to clear shadow volume copies by running the following command: “vssadmin.exe delete shadows /all /quiet”. This command uses Windows’ vssadmin administrative tool that manages system backups and snapshots. After deleting the backups, the ransomware then encrypts files on a computer that contains specific strings of data and file extension names. The files encrypted by the ransomware include users’ files, such as documents, photos, videos, audio files, etc. The only silver lining here, if you could call it that, is that the ransomware does not affect system files. Files excluded from encryption:
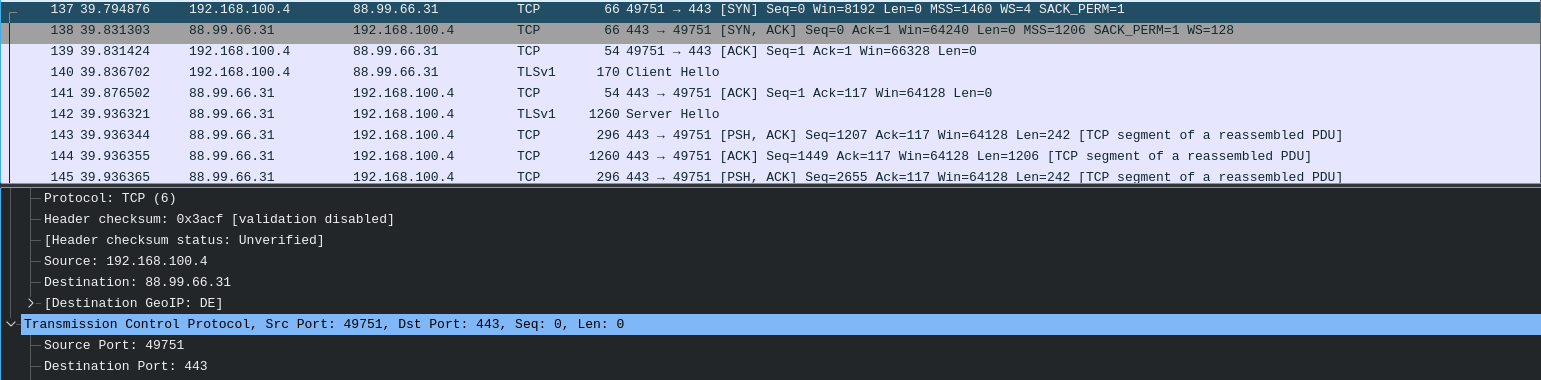
During a dynamic analysis of the newest sample of DeathRansom, security researchers noticed DNS requests and TCP traffic to a remote server. This probably why DeathRansom’s creator avoids encrypting system files in order to keep the system stable and track the malware’s infections.
Currently, there is no decryptor tool or information on how victims of DeathRansom ransomware can recover their files without paying the ransom. Malware victims should keep in mind that paying the ransom is no guarantee that their data will be decrypted. Thus, this option is not suggested. There are multiple methods on how to remove the DeathRansom and restore the system files manually. However, none of these are guaranteed to remove the ransomware and decrypt the locked data. Users who attempt the manual approach should take extreme caution due to the risk of permanently losing their files. As always, the best way to protect yourself from ransomware attacks is to employ good cybersecurity practices. The first thing to do is to set up daily backups and store them in an isolated network. Other good cybersecurity practices include avoiding suspicious attachments on emails, visiting spammy websites, having good anti-malware software.
No Clear Consensus on How DeathRansom Spreads
Encryption Routine and Targeted Files
Is There a Way to Remove DeathRansom from Your Computer?





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.