Discovered back in 2014, Emotet started as a banking Trojan, which was programmed to steal sensitive information. Later on, it became primarily a distributor of other malware. Emotet is considered to be a powerful threat that not only obtains private information but also rents the infected devices to other malicious software. To this date, its destructive behavior continues to cause trouble.
The US Department of Homeland Security describes Emotet as one of "the most costly and destructive malware affecting state, local, tribal, and territorial (SLTT) governments, and the private and public sectors." According to reports, this powerful infection was able to affect governments, as well as the private and public sectors, costing upwards of $1M per each incident.
Table of Contents
What is Emotet
Emotet, alias Geodo or Mealybug, debuted in the malware field as a simple banking Trojan programmed to steal its victim's financial information. Two years after its discovery, the malware got updated to operate mainly as a 'loader' that penetrates the system and allows its creators to download additional payloads. The masterminds behind Emotet also use the malware to create a botnet consisting of infected machines. This way, they can rent access to infected computers to other cybercriminals. Such IaaS (Infrastructure-as-as-Service) model is known in the cybersecurity field as MaaS (Malware-as-a-Service) or CaaS (Cybercrime-as-a-Service). That being said, Emotet has proven that it can serve not only as a standalone malware but as a service for malware delivery as well. Among the threats dropped by Emotet on infected devices are Ryuk, ZeuS, Trickbot, Panda, IcedID, Azorult, Dridex, and Ursnif.
As already mentioned, Emotet's first version surfaced back in 2014 and was designed to steal its victim's bank account information. Emotet 2.0 came shortly after that, upgraded with a money transfer system, malicious spam email module (malspam), and a banking module which helped the malware to target German and Austrian banks.
With the start of 2015, Emotet got another update. These new modifications made the malware even harder to detect. Along with the reinforced stealth, the third version of Emotet also contained new Swiss banking targets. It seems that the Emotet gang saw an even greater potential in their creation because three years later, the malware became a popular delivery mechanism for other famous threats like Ryuk Ransomware, Trickbot Trojan, and many others.
Even though there was a surge in Emotet activity at the beginning of 2019, that didn't last for long. In May, the C&C servers were shut down, which led to many believing that this was the end for Emotet. After months of inactivity, the malware revived in September and launched a strong spam campaign. Many English, German, Polish, and Italian victims received an infected Microsoft Word document with a title like 'Overdue invoice' or 'Payment Remittance Advice.' According to reports, when opened, the document initiates a macro that downloads Emotet from infected WordPress sites.
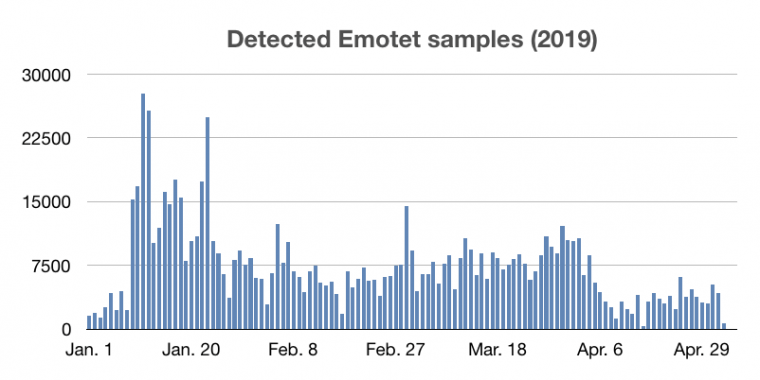
Figure 1: Emotet Samples Detected
This chart shows the amount of Emotet virus samples detected in 2019. Source: Virus Bulletin.
How the Emotet Trojan Works
Emotet has a functionality that helps it evade detection from some AV programs. What's more, it is not only Virtual Machine-aware but also has a way of detecting a sandbox environment (a tool used by malware researchers for observing threats within a safe, controlled space). If such a tool is found, the malware will lay dormant to evade signature-based detection. To maintain persistence, Emotet will auto-start Registry services. DLLs (Modular Link Libraries) allow the Trojan to update itself continuously.
After the malware successfully penetrates the machine's system, it will steal the following data:
But how exactly does the Emotet infection start? Typically, the victim receives a malicious email containing a Microsoft Word document, be it in a file form or as a download link. Here's the entire invasion process is broken down in 3 simple steps:
- The unsuspecting victim opens the file, which enables a macro.
- The micro executes commands through Microsoft Command Prompt and PowerShell to download Emotet from a compromised website via connecting to an IP address in possession of the cybercriminals.
- The infected machine activates Emotet, and the malware starts to distribute itself on other computers connected to the same network.
Thanks to its worm-like behavior, Emotet can spread to other connected devices. That's why it's essential to differentiate an infected computer from an affected one.
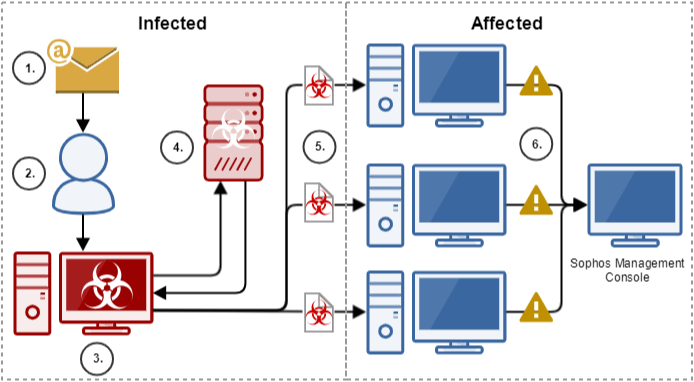
Figure 2: Before and After Emotet Infection
The diagram explains in detail the origin of the Emotet infection and how the threat can affect devices connected to the infected machine. Source: Sophos.
Emotet is also known to use a list consisting of the most commonly used passwords to get access to other connected systems. This Trojan benefits from weak admin passwords and system vulnerabilities, which allow malicious software to access the computer network. If it is unable to gain admin privileges, it will find other system processes to run itself through. Once the system is compromised, it will start to regularly contact Emotet's C&C (Command & Control) servers, to get the necessary updates, as well as new payloads and instructions.
The Many Spam Campaigns Used by Emotet
Just as Emotet's activities changed over the years, its distribution methods also took a slightly different approach. The threat typically spreads by malicious spam email campaigns (malspam). An infection occurs through a malicious link, macro-enabled attachments in the form of documents (Word files, Excel spreadsheets, PDFs, etc.) or malicious script. At the very beginning, Emotet relied solely on JavaScript files. It wasn't until later where it started to use macro-enabled documents to receive payloads and instructions from the cybercriminals' C&C servers.
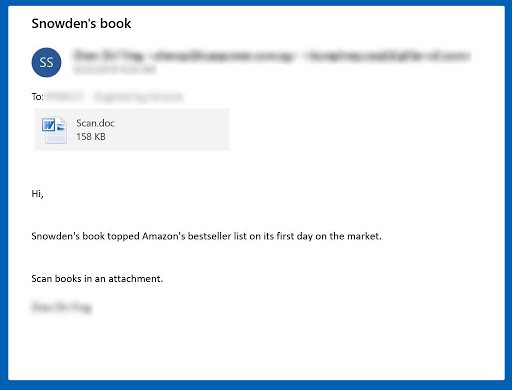
The emails are known to have a financial theme, be it a reply to a previous transaction, fake payment remittance notices, payment details, etc. They are specifically customized to trick the user into clicking or downloading the malware. In most cases, the titles of these emails read something like 'Your Invoice' or delivery information from renowned companies, so the user will click without giving it a second thought. Since Emotet can steal previous email content, it can implement existing conversations into the spam message. This will not only make the email trustworthy but will also make it harder for the anti-spam filter to detect. Emotet has a specifically tailored spam campaign according to their target. If their victim is a business, the email is likely to be an invoice or delivery information. With individuals, the message is most likely to contain something popular like an invitation to an event or a free copy of a book.
Downloading the malicious files enable macros the macros within them, will execute commands to download Emotet from embedded URLs leading to compromised WordPress websites.
Among the pages attacked by the Trojan are:
Once Emotet has been successfully downloaded and gains access to the computer system, the Trojan will obtain the user's contact list to send itself to more people. That's a smart trick since the unsuspecting recipients will not feel like these emails are unsafe, and therefore will be more inclined to interact with them.
After taking an almost three-week vacation for the winter holidays, Emotet came back strong with a new malicious spam campaign that targeted over 80 countries. The gullible victims think they're getting information about upcoming events when in reality, Emotet is infecting their computers. Apart from the typical invoices and financial reports, the new email strategy includes using Greta Thunberg demonstration invites, impersonating the “Permanent Mission of Norway,” as well as invites to a holiday party.
According to reports, the phishing emails claiming to be from representatives of Norway were sent to 600 unique email addresses at the United Nations. In said emails, the representatives of Norway at the United Nations in New York claim that there's a problem with an attached signed agreement that the recipient needs to review. Here's the full text of the phishing email:
"Hi,
Please be advised that the new problem has been appeared today.
See below our info for this question.
Please let me know if you need anything else.
Regards
Permanent Mission of Norway to the United Nations in New York"
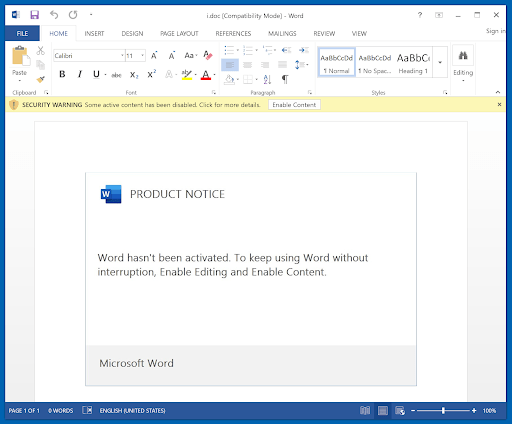
The email also contains an attachment – a Microsoft Word document with the name “Doc_01_03”, posing as a legitimate signed agreement by the Permanent Mission of Norway. When opened, the document will prompt the user to click the Enable Content button, to view the content of the file. After the user enables the content, a macro to download Emotet will get executed. After its installation is complete, the Trojan will run in the background and start sending spam emails to other people. What's even worse for the compromised UN workstation is that Emotet will also install the Trickbot Trojan and other payloads that may compromise their entire network.
Notable Emotet Attacks That Show Its Destructive Power
Is there a specific target for Emotet? No. For Emotet, everyone is a potential target. The Trojan has hit many individuals, companies, and even governments across the U.S. and Europe. At first, the infamous threat was widely known for stealing banking accounts, financial information, and Bitcoin wallets, mainly in Germany, where it posed as several German federal authorities. After getting a serious update that allows it to drop other threats on the infected machines, the list of targets grew significantly, targeting victims in the UK, Canada, and the United States.
Back in 2018, a particular Emotet attack on the city of Allentown, PA, even required direct help from Microsoft's team, since all city systems ran Microsoft software. Reportedly, the malware attack cost the city more than $1 million to resolve, which includes Microsoft's emergency response fee and the amount of money needed to recover the damages done by the Trojan.
“This particular virus actually is unlike any other virus. It has intelligence built into so it keeps adapting to our systems, thus evading any firewalls that we have up,” Mayor Ed Pawlowski told The Morning Call.
Emotet even made international headlines after an attack on Lake City, Florida, costing the town $460,000 in ransomware payouts, according to reports. After the successful infiltration, Emotet dropped another banking Trojan called TrickBot, as well as the Ryuk ransomware.
Preventing an Emotet Infection
Now that you've acquainted yourself with the essence of Emotet, you should make sure that you're taking the necessary precautions to avoid infecting your computer with such destructive malware. In short, here's a list of what you can do to protect your device and personal data:
- Make sure a reputable AV software protects your PC.
- Keep your system and other software up-to-date to avoid system vulnerabilities.
- Change your passwords regularly, and never use default or weak passwords. It's best to use two-factor authentication when possible, especially when online banking is concerned.
- Be cautious when opening your email messages. Always check if the sender is who they say they are. If the message claims to be sent from a legitimate company, the first thing you should do is compare the email address with the one given on the company's official page. Do not interact with email attachments unless you are 100% sure they come from a trustworthy source. Cybercriminals' scare tactics can make their victims rush into opening infected emails, so don't be too hasty to open a message just because of the subject title that's urging you to act fast.
If you have suspicions that your computer got infiltrated by Emotet, do not panic. The first thing you need to do is check if your computer is connected to a network. If it is, make sure to isolate it immediately. After that, proceed with applying appropriate patches and cleaning the infected system. You have to clean each computer connected on your network thoroughly to make sure there are no traces left from the Trojan. You can do that manually, or by using antivirus programs that have automatic features for cleaning the system.





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.