The trojan-type malware TrickBot has been infecting victims since 2016 and it is currently considered among the top threats targeting businesses. According to security researchers, the malware has been developed to steal users' private data, mostly targeting financial institutions and credit card providers. After being updated in 2017, the number of incidents involving TrickBot has increased dramatically. The experts claim that by July 2019, the trojan has compromised over 250 million email accounts.
Table of Contents
TrickBot Banking Trojan: A Financial Institution’s Worst Nightmare
TrickBot is a banking trojan that steals credentials from banking institutions worldwide. The first attacks involving TrickBot were against Australian banks in September 2016, and by November 2016, the attacks reached financial institutions in the United Kingdom. After the initial attack campaign, security experts found that TrickBot had five distinct characteristics:
“TrickBot combines RAT and redirection techniques to conduct sustained, multi-phased campaigns. The Trojan slowly manipulates victim accounts until ready to deploy a standard Remote Access protocol (VNC) completely invisible to device recognition and geo-location tools. After switching off all active components of the malware, they open a browser from within the genuine victim machine, log into online banking and proceed uninterrupted to empty the victim's account.”
Like most banking trojans, TrickBot was created to generate revenue for its developers by literally stealing other users' money. While the latest version of the TrickBot trojan is rough around the edges, researchers believe it shows a possible direction that future versions of TrickBot will take.
TrickBot Has Multiple Vectors of Infection
TrickBot is usually distributed via spam emails; however, there are a couple of other ways for its distribution:
- SpearPhishing: TrickBot is distributed via phishing emails containing malicious attachments. These emails specifically target senior-level executives.
- Network Vulnerabilities: TrickBot is capable of spreading through an organization’s network by exploiting the Server Message Block (SMB) Protocol that allows Windows computers to disseminate information to other systems on the same network.
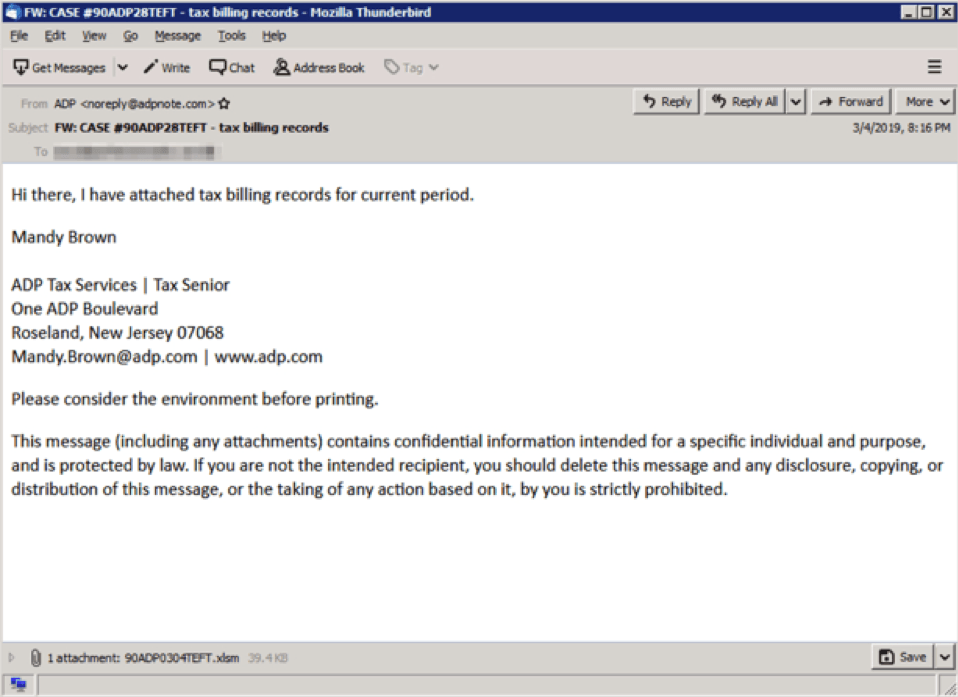
- Secondary Payload: TrickBot can also secondary infection dropped by the other powerful Trojan Malware – Emotet.
Figure 1: TrickBot Phishing Email
A phishing email posing as a tax service provider in order to trick the user into downloading TrickBots’s malicious payload. Source: threatpost.com
TrickBot Steals Users’ Login Credentials and Passwords
TrickBot hijacks web browsers and modifies the websites displayed by them. Once the websites are modified, the attackers steal the recorded logins and passwords and send them to a remote server.
By stealing login credentials and passwords for cryptocurrency wallets, PayPal and bank accounts, the attackers can transfer money without users' knowledge, leading them to severe financial losses. The latest versions of TrickBot are even capable of locking victims' computer screens, forcing them to pay a ransom.
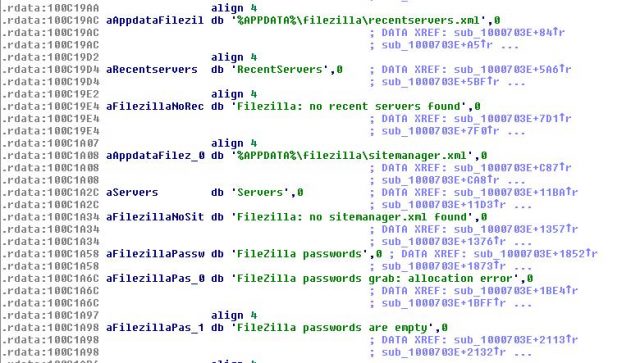
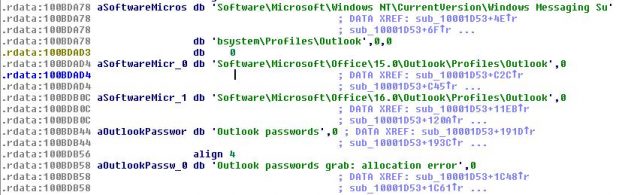
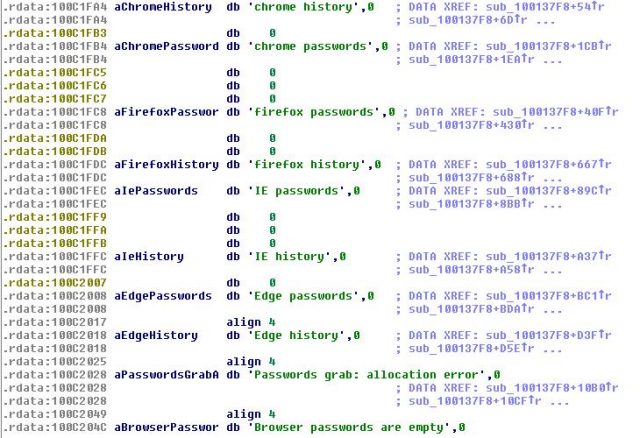
Thanks to the implemented module "pwgrab", TrickBot is capable of hijacking various applications, such as Mozilla Firefox, Google Chrome, Microsoft Edge, Internet Explorer, WinSCP, Microsoft Outlook, and Filezilla.
To steal data from web browsers, TrickBot malware uses a cookies-grabbing module. This module is used for stealing web browser cookies which help hackers to create a better profile of each victim and to optimize the cyber attack.
Recent versions of TrickBot are capable of stealing PIN codes from people who use services of telecommunication providers such as T-Mobile, Verizon Wireless, and Sprint. This allows hackers to gain control over victims' phone contacts or text messages.
TrickBot is Constantly Evolving
A really important thing about TrickBot is that this malware is capable of updating itself after an infection. It means that each of its victims will receive the latest version of TrickBot via the Internet, no matter when this banking malware banking trojan has infiltrated the system first.
During the past few months, the malware has been updated several times. With every update, the banking trojan gains more pervasive functionality, keeping security experts on their toes. Some of the most recent updates include: :
September 13, 2019 - Hackers launched a spearphishing campaign to distribute TrickBot by attaching a malicious Word document to the emails. The interesting part here is that the content of this document contained thousands of JavaScript code lines within. To hide them, hackers changed the text color to white and, since the background was also white, the text became invisible. This way the attackers tricked users into thinking that the document was empty. However, once opened, it ran a macro command, which extracted the malicious content to a local file and the JavaScript code was executed, injecting TrickBot into the system. A screenshot of a malicious MS Word document containing JavaScript code is shown in the picture below.
Figure 3: Screenshot of a malicious MS Word document containing JavaScript code: 
We can see Microsoft Excel warning the user about the malicious code in the file. Source: pcrisk.com
November 25, 2019 - A new version of TrickBot added a new feature that allows the threat actor to steal OpenSSH private keys and OpenVPN passwords and configuration files. However, TrickBot's data exfiltration function was not fully developed, which means that the stolen information was not sent anywhere. For that reason, researchers suggested that developers were hardly testing this function. In any case, the problem could be fixed at some point, so the data could be sent to the Command & Control (C&C) server.
December 10, 2019 - Hackers launched another spam campaign to spread the TrickBot banking trojan. At that time, the attackers used hijacked .edu email addresses to send deceptive emails, which contained details regarding some sort of "annual bonuses". The emails encouraged users to download a form, print it and sign it. However, the download links led to a malicious executable that injected TrickBot into the system. An email from this spam campaign is shown in Figure 3 below.
Figure 4: Email from spam campaign 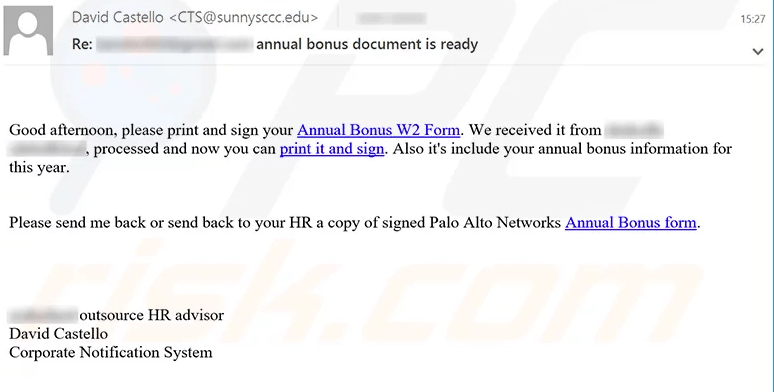
This social engineered email attempts to trick the user into downloading TrickBot’s malicious payload. Source: pcrisk.com
The email text was presented as shown below:
“Subject: Re: ******* annual bonus document is ready Good afternoon, please print and sign your Annual Bonus W2 Form. We received it from ******* ***********, processed and now you can print it and sign. Also it's include your annual bonus information for this year. Please send me back or send back to your HR a copy of signed Palo Alto Networks Annual Bonus form. January 14, 2020 - The creators of the TrickBot banking trojan developed a post-exploitation tool called “PowerTrick”. The main purpose of this tool is to spread TrickBot from an infected computer to every other terminal connected to the same network. PowerTrick infects systems via reverse shell, This is done by running a number of PowerShell commands that download and install the malicious software (TrickBot Anchor Malware, More_Eggs JavaScript backdoor) into the systems. January 17, 2020 - The latest update of TrickBot implemented a new feature that allows the malware to bypass Windows UAC (User Account Control) and run the malicious executable with administrative privileges, without users' knowledge and permission. Depending on the infiltrated system (Windows 7 or Windows 10), TrickBot malware uses different methods to bypass the Windows UAC and infects the system. The latest versions of TrickBot are very hard to detect. Apart from its increased hiding capabilities, the malware can disable Windows Defender, which makes its removal process much harder. So, if you have recently downloaded any suspicious email attachments or used third party Adobe Flash Player tools, you should use reliable antivirus software to find and remove the malware immediately.
******* outsource HR advisor
David Castello
Corporate Notification System”It is Virtually Impossible to Determine if TrickBot is Present onto the System





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.