Hackers continue exploiting the COVID-19 outbreak to make easy money. Among their recent creations is the Ginp banking trojan. Ginp takes advantage of Android users by using information about people infected with Coronavirus. The attackers’ main purpose is to steal login credentials and credit card details from victims. A recent ThreatFabric’s analysis of Ginp shows that the trojan reused some of the code from Anubis; a family of Android malware family famous for its use in cyber espionage activities.
Table of Contents
The Coronavirus Finder Does Not Work
Malware authors found a way to use fear of the global pandemic to lure victims to install the Coronavirus Finder app on their Android devices. However, what users don’t know is that they install the Ginp trojan instead.
As soon as Ginp is downloaded on the victims’ phone, the attackers send a special command to the trojan and it opens a web page named “Coronavirus Finder.”
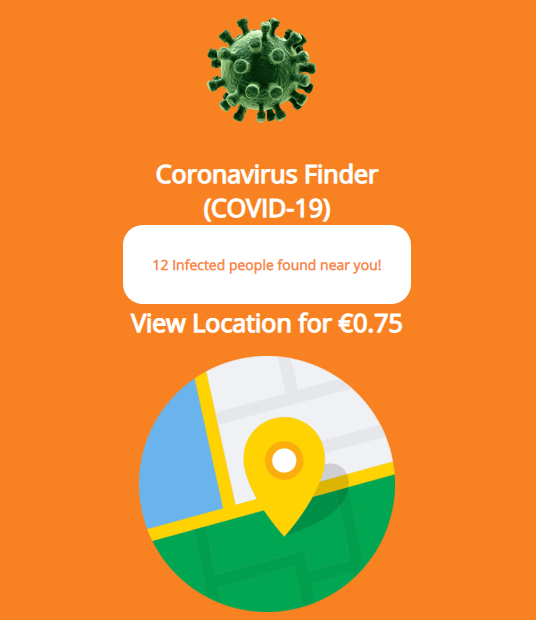
Figure 1: Image: Coronavirus Finder App Loading Screen
Ginp Trojan tricks the user into giving their login information by requesting payment to display nearby COVID-19 cases. Source: Kaspersky Daily
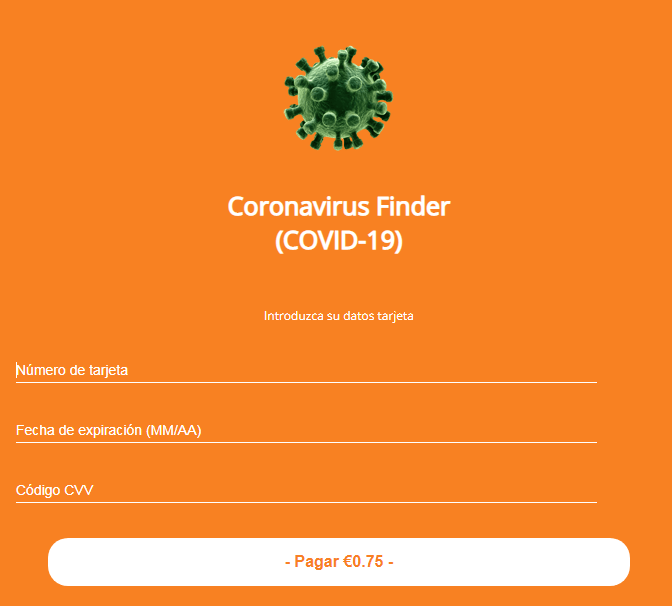
The Coronavirus Finder website shows how many people have been infected with COVID-19 near the victim’s location. After that, it asks the victim to pay €0.75 to see the exact location of the infected persons. If they agree to pay, Ginp redirects the victim to a payment website, where payment details are needed. When the victim enters the details, they are neither charged, nor do they receive any information about the infected persons’ location. Instead, the attackers receive full access to the victims’ credit card details and their bank accounts are no longer safe.
Figure 2: Image: Coronavirus Finder Payment Website
The bad actors use social engineering to trick users into giving away their credit card number. Source: Kaspersky Daily
The Ginp trojan has some additional capabilities on top of stealing its victims’ credentials which users should be aware of:
- Sending or harvesting SMS messages
- Request admin privileges
- Enable overlay attacks
- Update command-and-control (C&C) URL
- Update target lists
- Set itself as the default SMS application
- Prevent Accessibility Services disabling
- Install suspicious apps or contacts
- Enable call forwarding
- Prevent itself from removal
Security Researchers Have Spotted Ginp Trojan Before
The Ginp trojan was first discovered in October 2019 by the Kaspersky expert Tatyana Shishkova. The first variant of Ginp was disguised as a "Google Play Verificator" application, primarily stealing SMS messages. Then, the trojan posed as fake “Adobe Flash Player” app targeting credit card information, and its next version was enhanced with payload obfuscation targeting Snapchat and Viber users.
Later on, the developers of Ginp borrowed code from the Anubis malware and went after banking app users. The analyst Tony Bao found a variant of Anubis (detected by Trend Micro as AndroidOS_AnubisDropper) that targeted 188 banking- and finance-related applications.
The latest Ginp variant has slight modifications, including a new endpoint related to downloading a module and pieces of code borrowed from Anubis targeting users of 24 apps from Spanish banks.
Stay Safe From the Ginp Trojan
Since the Ginp trojan is currently attempting to capitalize on the pandemic, Android users should be particularly vigilant with unknown websites, pop-ups, and unsolicited messages regarding the Coronavirus. Given the speed at which this virus spreads, no one has this level of confidential information, therefore they need to be very skeptical about anyone who claims to.
Security researchers also suggest some precautionary measures to avoid exposure to the Ginp trojan, which include:
- Install or update Android apps only from Google Play Store.
- Do not open any suspicious links and never share sensitive information, such as logins, passwords, or credit card details.
- Do not give Accessibility permission to applications that request it, other than anti-virus apps.





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.