
Researchers recently discovered a spike in Monero-mining botnet Lemon Duck infections. Researchers warn that criminals are operating a massive campaign that aims to steal computing resources.
While Lemon Duck botnet has been idle since December 2018, cybersecurity analysts registered an increased number of DNS requests connected with the botnet's command and control (C&C) server. Since late August 2020, Lemon Duck's mining servers have been attacking countries around the world. According to Talos telemetry, the campaigns are focused on Asian countries, including Vietnam, the Philippines, and India.
Figure 1: World Map
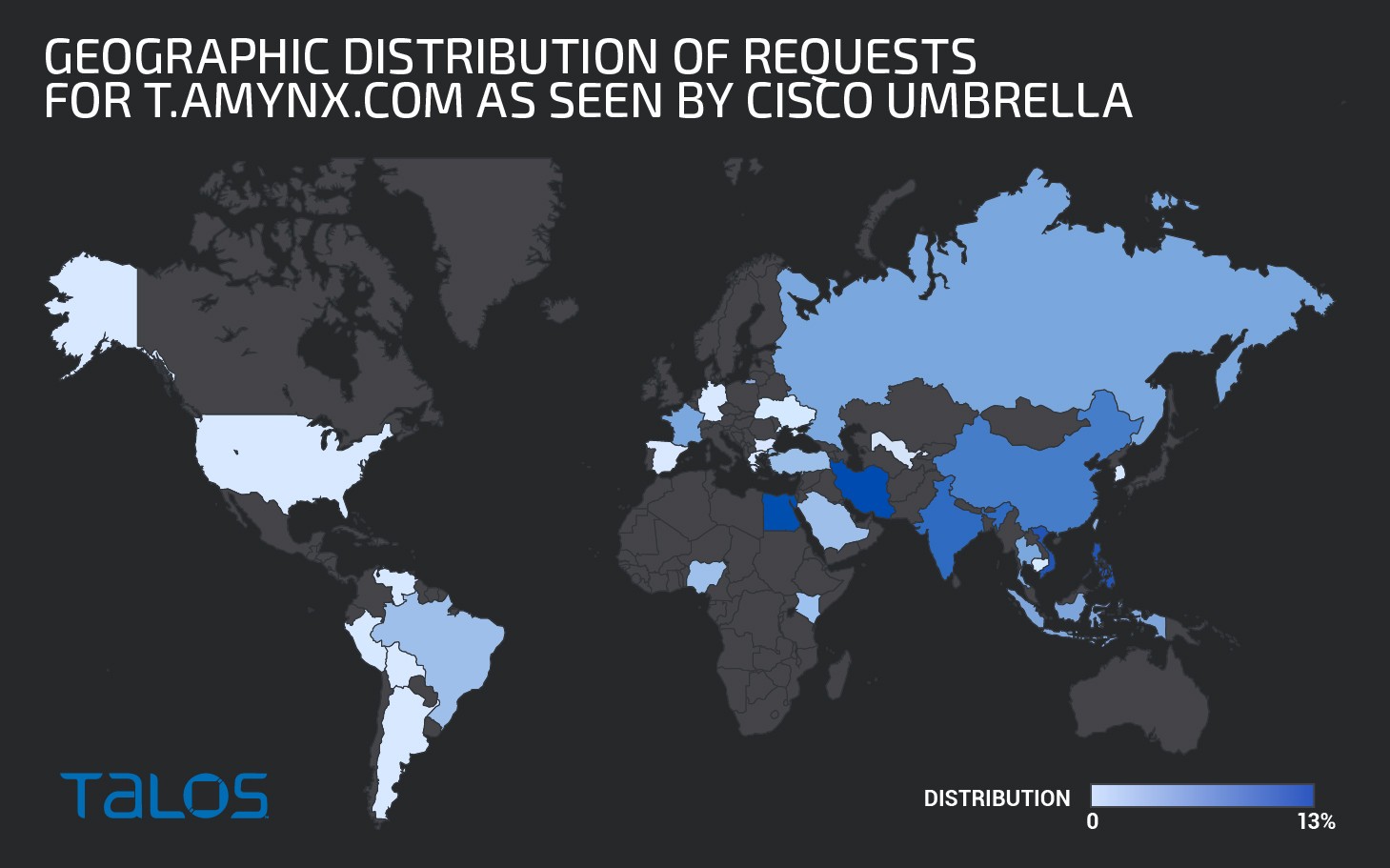
"Cisco Talos has identified activity in our endpoint telemetry associated with Lemon Duck cryptocurrency mining malware affecting three different companies in the government, retail, and technology sectors," Cisco Talos researchers said in a blog post.
Table of Contents
Lemon Duck Botnet
Lemon Duck is a multi-modular botnet that provides its operators with various opportunities to cause harm. With its 12 independent modules, this network stands out in the botnet crowd as superior.
The botnet's arsenal of functionalities includes password brute-forcing, sending emails with exploit attachments, and targeting the RDP BlueKeep flaw (CVE-2019-0708) in Windows OS. The threat can also target vulnerabilities in the open-source data-structure store Redis. YARN Hadoop, Linux-based resource-management, and job-scheduling technology are also vulnerable to attacks from Lemon Duck.
According to Talos research, Lemon Duck's main module is delivered as PowerShell scripts, which subsequently install the mining payload, the main spreading module, and a Pyinstaller spreading (email-spreading) module.
Infection Vector
Upon infiltrating the host, Lemon Duck will download a PowerShell-loading script designed to neutralize Windows Defender by utilizing the function "bpu."
The bpu function bypasses Windows defenses by adding powershell.exe to the list of processes excluded from scanning. The function will also check if the script is running with administrative privileges. If it does, a payload will be downloaded and run by utilizing the Invoke-Expression cmdlet, a function that can call code or commands within a script.
If the script doesn't run with administrative privileges, bpu uses system executables to launch the next attack stage. The loader will modify some registry entries to indirectly execute the PowerShell payload through "ComputerDefaults.exe" for Windows 10 or "CompMgmtLauncher.exe," used for earlier Windows versions.
Figure 2: PowerShell Payload Loading
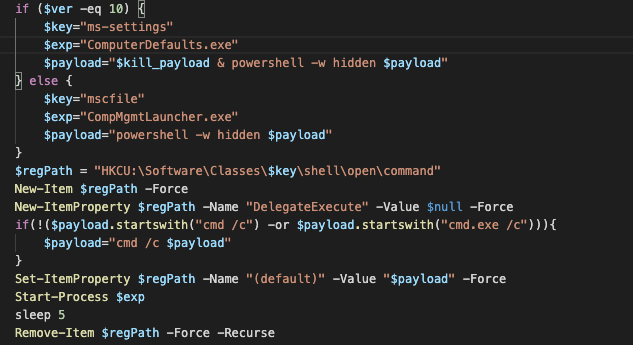
According to the research, all executable modules are downloaded and run by the main module. The module communicates with the C&C over HTTP.
Malware Modules
Lemon Duck's main module is designed to check the components relevant for mining, such as the type of the installed graphics card (GPU) and whether the user has admin privileges. If no GPU is detected, the module will download and run XMRig, a CPU-based mining script.
The main spreading module is another essential malware functionality. It is designed to kill any competitive mining malware that runs on the host device. The module is Python-based, packaged using Pyinstaller, which researchers describe as "a rather ambitious piece of code" because it contains over 10,000 lines of code.
An interesting email-spreading module is also part of the Lemon Duck's arsenal. The module exploits Microsoft Outlook to send emails to every contact in the victim's address book. The sent messages use a mix of subject lines, such as COVID-19-themed and other emotion-driven subjects, including "HALTH ADVISORY:CORONA VIRUS" and "WTF," to lure the recipients into downloading a malicious attachment.
Figure 3: Malspam Example
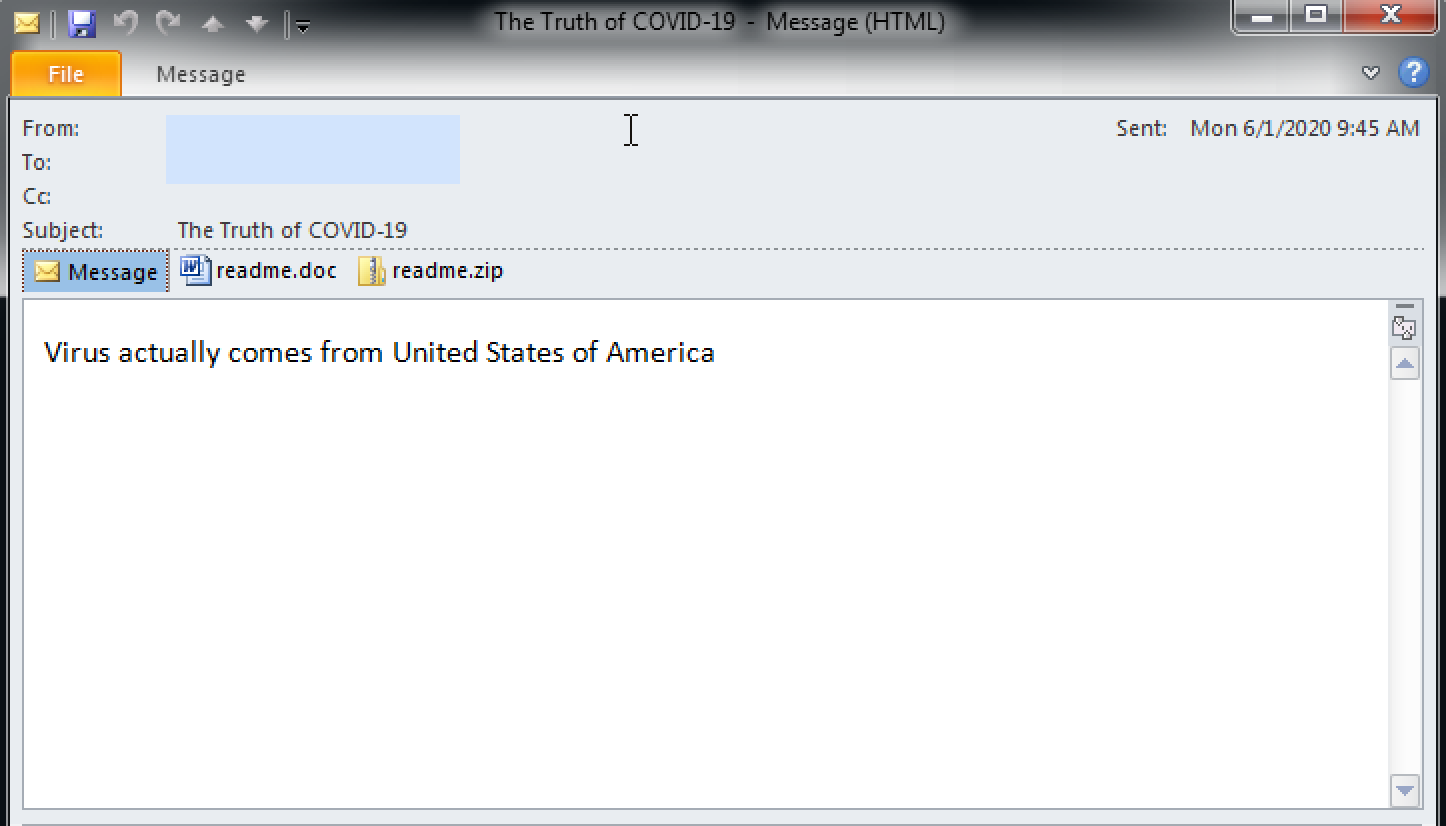
According to the research, every generated email contains two attached files, one being an RTF document with the name readme.doc. that exploits the remote code execution vulnerability, CVE-2017-8570. The other is a ZIP archive called Readme.zip that contains a JScript, designed to download and run the first-stage Lemon Duck loader.
No One Is Safe! Not Even Linux Users!
Lemon Duck proves that Linux machines are not invulnerable to malware attacks. Researchers found a Linux module in the malware's toolset.
Upon compromising a Linux host through Redis, YARN, or SSH, two bash scripts will execute. While one of the scripts is tasked to collect information about the host and launch a Linux version of the XMRig miner, the other will remove competing mining processes and stop and uninstall processes related to Alibaba and Tencent security software.
USB Infection
Despite being commonly feared, cyber infections caused by corrupted USB drives are relatively rare. However, Lemon Duck is one of these mythic threats that could reach your device through an infected external storage device.
Lemon Duck’s USB spreader will enumerate and infect all removable and network drives. It will also create a file inf_data that will prevent future reinfections.
The spreader drops a 32 or 64-bit variant of a malicious DLL, which is associated with a CVE-2017-8464 exploit. Upon creating a mutex, which ensures that only a single copy is running in memory, the DLL code will runDLL32.exe and inject code into its process space.
Additionally, the USB spreader module will also create a readme.js file, identical to the readme.js file, spread by the email spreading module.
Previous Campaigns
In early October 2019, Lemon Duck was used in cryptomining attacks across enterprise networks. The attackers used various advanced techniques, such as fileless script execution, to turn enterprises' large pools of CPU resources into efficient mining bots.
In February 2020, researchers at ThrapX published an alarming alert about a Lemon Duck campaign targeting IoT (Internet of Things) devices at manufacturing sites.
A month later, in late March 2020, researchers found another Lemon Duck campaign targeting Windows-based printers, smart TVs, and automated guided vehicles. The global campaigns leveraged the XMRig mining tool to exploit IoT devices.
Talos researchers warn that crypto-mining botnets cannot be ignored as they could cause disruption of supply chains, data loss, and security issues.
"Cryptocurrency-mining botnets can be costly in terms of the stolen computing cycles and power consumption costs," researchers said. "While organizations need to be focused on protecting their most valuable assets, they should not ignore threats that are not particularly targeted toward their infrastructure."





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.