
RIPlace is not a technique that interferes directly with your anti-virus apps. Neither does it take advantage of a new critical Windows vulnerability. RIPlace is an entirely new technique that exploits a flaw in the Windows OS Rename function, allowing malware, including ransomware, to modify and delete your data.
In 2018, researchers at Nyotron discovered a flaw in the Windows OS that could allow malware actors to change and potentially encrypt user files. The so-called 'RIPlace' technique is a sort, a few-lines-long code that bypasses anti-virus, anti-ransomware, and Endpoint Detection and Response solutions.
How does RIPlace work?
To understand how RIPlace operates, we must first understand how ransomware threats corrupt data.
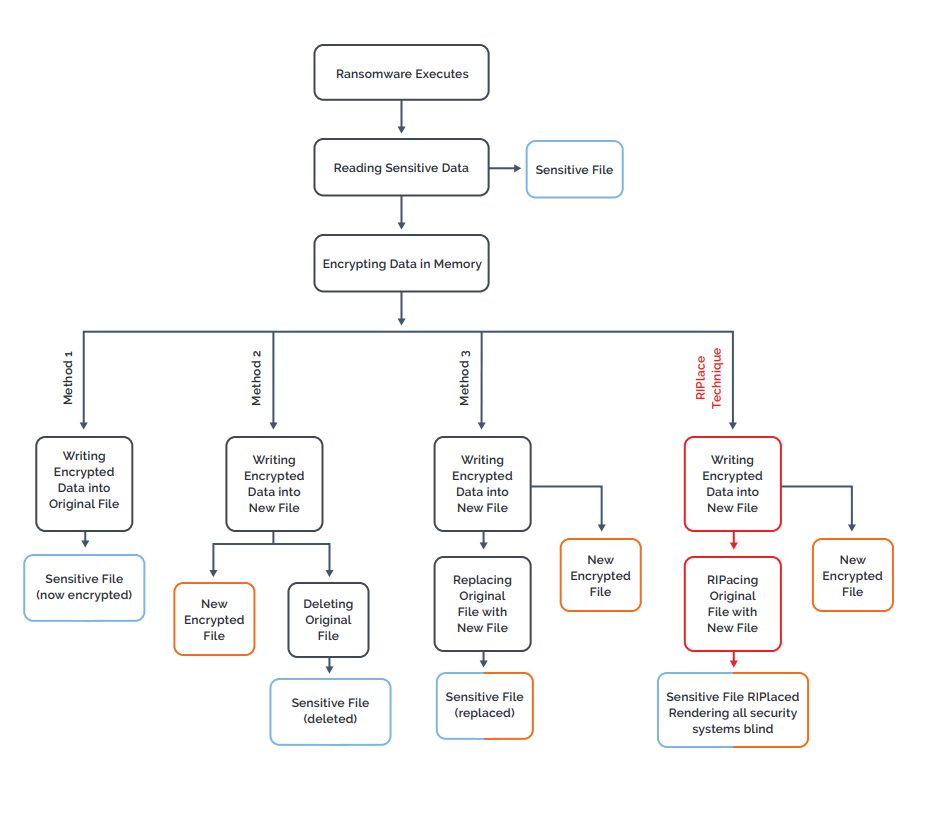
Once a ransomware threat is successfully installed on a computer, it will follow the following procedure:
- Open and read the target file,
- Encrypt the content in memory,
- Corrupt the target file using either of the following methods:
- Method 1: the threat writes the encrypted data from memory directly to the original file,
- Method 2: the threat writes the encrypted data from memory to a new file and then deletes the original one,
- Method 3: the threat writes encrypted data from memory to a new file and then replaces the original with the new one by using the Rename function.
Ransomware protection features work to prevent these methods from succeeding. As shown in figure 1, however, RIPlace uses a variation of the third method to used to encrypt the files in a way that bypasses anti-ransomware filters.
Figure 1: Ransomware encryption methods
This chart illustrates how RIPlace makes ransomware undetectable from security software. Source: Nyotron
RIPlace uses the DefineDosDevice function to create a DOS device that links to the newly-created encrypted file. When the ransomware calls the Rename function, it will 'mistake' the DOS device for the legitimate path, and since DOS device names are not expected, an error will be returned.
The ransomware protection filters will see this error and won't interfere with the operation, allowing the Rename process to replace the original file with the encrypted one.
Companies Ignore RIPlace Warnings
In Spring 2019, the Nyotron researchers disclosed the RIPlace technique with Microsoft and other security vendors. Despite the warnings, very few companies have taken action to protect their users. Their excuse for inaction is based on the fact that the RIPlace technique has not been observed in the wild; therefore, it is not a threat. However, security researchers warn that if ransomware operators start implementing RIPlace, the consequences will be dire.





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.