A new variant of the infamous Metamorfo banking Trojan targets victims around the globe.
Metamorfo malware came under the spotlight in April 2018, when it targeted multiple Brazilian financial institutions. Researchers observed various phishing campaigns with small "morphing" differences that spread the malware through the use of "spray and pray" spam tactics.
Almost two years later, the malware is making a comeback with new targets in US, Canada, Spain, Brazil, Mexico, Ecuador, and others. Researchers report that the malware attacked over 20 online banks around the globe. The list of targets has not been released yet, as it is likely that the Metamorfo campaign is still active.
Table of Contents
Metamorfo: Old Malware, New Tricks
Security analysts explain that the new malware variant, Metamorfo, targets payment-card data and credentials at financial institutions that use Windows OS. They add that although the latest version of the malware shares similarities with its predecessor, it has new tricks up its sleeve that lure the victims into revealing their sensitive information.
Security researcher Xiaopeng Zhang reports that Metamorfo can disable the auto-fill function of all internet browsers. By doing this, it forces the victims to manually type their sensitive information, which is then recorded by the malware's keylogger.
Metamorfo can also display messages that prompt the victim to re-type their password and confirmation codes, keeping the cybercriminal’s database updated even if the victim changes their password. These tricks not only allow the keylogger to record various sensitive data but could also enable the con artists to bypass two-factor authentication.
In addition to its arsenal, Metamorfo is also capable of stealing Bitcoin wallets. During the first stage of its execution, the malware checks if the computer has a Bitcoin wallet. If it detects one, it overwrites the address of the rightful owner and replaces it with one used by the threat actor.
Metamorfo Infection vectors
Metamorfo is usually spread through phishing emails. The threat actors would send fake notifications and alerts that the victim might expect and is likely to believe to be genuine. The victim will be prompted to download a ZIP archive that supposedly contains additional information on an important subject, an invoice or a receipt. In reality, the ZIP file contains an MSI file used to install Metamorfo.
Figure 1: Metamorforo Phishing Email Example
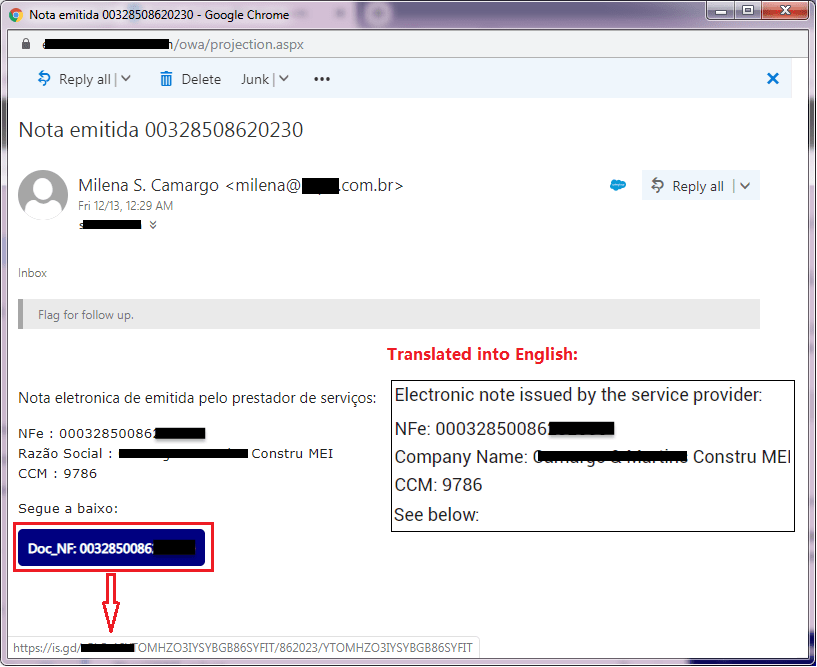
Example of an email used by hackers to trick users into downloading the Metamorfo banking malware. Source: fortinet.com
Metamorfo uses an MSI file named “XlsPlan_Visualize.msi” that serves as a downloader program that retrieves an additional ZIP file archive named img.zip from the following address: hxxp[:]//www[.]chmsc[.]edu[.]ph/library/modules/down/op57.
The new ZIP archive contains three files that get decompressed into the %Public%\Downloads\KJFLDKR folder. VBS code will then rename the file to KJFLDKRE.msi. This file is the actual Matemorfo malware, which will execute with the "quiet" parameter in order to run in the background, unnoticed by the user. It will also terminate any instances of Msi Exec.exe processes
Figure 2: Content of Memamorfo’s “KJFLDKRE.msi” file
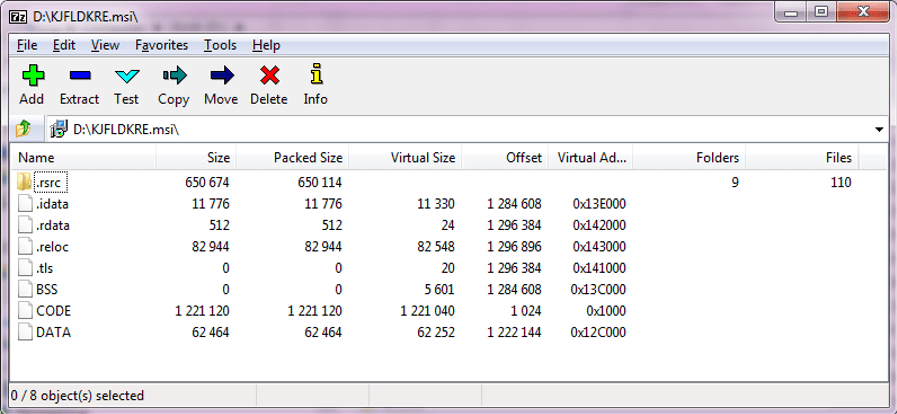
The malware will also add the three decompressed files to the auto-run group of the registry so that they start alongside the OS every time the device is restarted.
Prevention
Metamorfo is spread via spam campaigns that take advantage of the user's naivety. The best way to prevent these social engineering tricks from succeeding is to take a proactive approach. Users should not give in to their impulses and be wary of unexpected emails and suspicious attachments.
Having an antivirus app can be quite beneficial as most antivirus vendors and programs include tools that successfully counteract the most common phishing tricks.
Last but not least, users should definitely keep their system updated w





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.