
Qbot trojan is back on the scene with some new tricks. The nasty banking trojan is now targeting Microsoft Outlook to extract information and use it for malicious purposes.
Qbot is a notorious banking trojan that has been targeting bank customers for over a decade. It was first discovered in 2008 and is known for its data exfiltration capabilities, which are aimed at its victims' browsing history data and banking details, including login credentials.
Table of Contents
About Qbot
Also known as Qakbot and Pinklipbot, Qbot is often described as the Swiss Army knife of banking trojans. The threat has a wide range of capabilities, including stealing information from infected devices, installing other malware, allowing Bot controllers to connect to infected computers, and many more.
The newest variant adds email hijacking to the long list of Qbot's functions. Researchers at CheckPoint, who first reported the new threat, note that the threat uses an email collector to extract emails and use them in elaborated phishing campaigns that aim to infect more devices.
The email collectors extract email threads from Microsoft Outlook and upload the stolen data to a hardcoded server. Later, the attackers could exploit these emails to send malspam to continue the once legit email threads and easily trick their targets.
CheckPoint researchers report that such stolen emails were used in campaigns with subjects related to tax payment reminders, and job recruitment, and even Covid-19.
New Campaigns
CheckPoint researchers have observed multiple Qbot campaigns this year, with the first one running from March till the end of June.
Shortly after the first campaign, Qbot was once again spotted in the wild. Emotet trojan, one of the most serious malware today, launched multiple malspam campaigns, some of which spread Qbot.
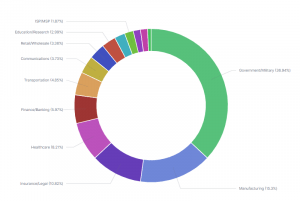
Most recently, a malspam campaign resumed earlier in August, spreading the upgraded Qbot variant. The campaign was aimed at US- and Europe-based organizations, targeting government, military, and manufacturing sectors.
Figure 1: Attacked Organizations by Industry
Infection Chain
The initial infection begins with specially crafted emails that target organizations. Although this method is not as sophisticated as the spear-phishing techniques, the campaigns featured hijacked email threads that effectively targeted companies' employees.
Figure 2.1: Malspam example
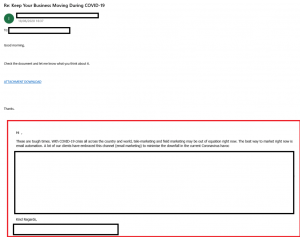
Figure 2.2: Spam Email IMG:
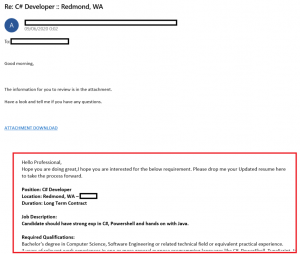
The campaigns used various topics to trick their targets into interacting with either weaponized URLs or ZIP attachments that contained a malicious VBS (Visual Basic Script) file, which downloaded Qbot's payload from a hardcoded URL.
New Anti-VM and Anti-Debugging Techniques
Researchers note that the implementation of a VBS file is a new infection method that wasn't previously used by Qbot. The malware developer also utilized several other new techniques to obfuscate the VBS and make the malware analysis time-consuming and unpleasant for the analyst.
The malware developers adjusted the file sizes. Due to performance limitations, most sandbox environments dismiss large files. The threat actors avoid sandbox analysis by using files that are larger than 35MB,
The threat actor included an additional anti-VM technique to stay on the safe side. A sleep timer, designed to delay script execution by calling the Sleep API, was implemented to prevent sandbox analysis.
Additionally, the VBS file contains multiple obfuscation methods, as well as custom XOR encryption. Interestingly, the threat actor encrypted the download URLs with three different XOR keys.
Conclusion
Qbot is a complex, multi-layered malware that is more dangerous than ever. Its active malspam campaigns target organizations and critical governmental infrastructures, threatening to cause severe damage if the right victim falls into Qbot's traps.
Additionally, being included in Emotet's infrastructure is a warning to all companies and organizations worldwide. As Qbot's developers continually upgrade their threat, organizations should also invest in their security in order to prevent mishaps.





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.