
The LockBit criminal gang has launched a data leak website as a part of their new strategy to extort their victims on two fronts.
According to cyber intelligence company Kela, the LockBit gang posted a link on a Russian-speaking hacker website, advertising their new website, potentially trying to attract more criminals into their Ransomware-as-a-Service (RaaS) business.
Data leak websites became a trend in 2019. Many ransomware operators started uploading stolen data on public websites, leaking pieces of sensitive information until the victims pay up. Ransomware threats that use this scheme are the infamous Maze, NetWalker, DoppelPaymer, and Sodinokibi/REvil.
The new LockBit website is not the first leaking page created by the gang. Since June 2020, the ransomware operators have been working under the label of Maze Cartel, a ransomware organization, publishing data on the cartel's web platforms. It is currently unknown whether this new website is under the cartel's control or interdependently run.
Table of Contents
New victims
Experts warn that all LockiBit attacks are not typical ransomware operations. As the threat actors upload personal, often confidential information, such attacks are considered data breaches.
Therefore, companies attacked by LockBit, or other data-leaking ransomware, must be transparent about the attacks so that their customers and employees can take measures to protect themselves.
About LockBit Ransomware
For the most part, LockBit acts as a standard ransomware threat. It infects the target device and launches a scan of the HDD. The threat is looking for user-generated data, such as pictures, databases, spreadsheets, and anything that might be valuable to the user.
Once the target files are located, LockBit will use an advanced encryption algorithm to lock the files and prevent the user from accessing their data.
All files encrypted by LockBit are easily recognizable. The ransomware marks the corrupted files by adding the ".abcd" extension to them. Additionally, it drops a text file named "Restore-My-Files.txt" to every folder that contains corrupted data.
Figure 1: Ransom Note
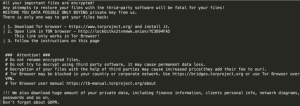
The text files are ransom notes which inform the victim that their files are encrypted and that data recovery software is available in exchange for ransom. The note includes a message that warns the victim that if they don’t pay the ransom, their personal files will be uploaded online.
Additionally, LockBit will change the desktop wallpaper to a message for the user, also informing the victim that their files are encrypted and urging them to open the Restore-My-Files.txt document.
Figure 2: LockBit Wallpaper
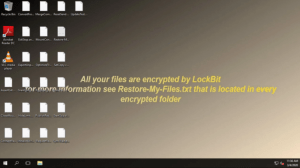
Victims are instructed to contact the criminals through a web portal and to refrain from using third-party recovery tools because such actions could cause permanent data loss.
Data recovery
The data recovery could be quite challenging as LockBit deletes the shadow backup copies and the backup catalog. It also disables the 'Windows Automatic Repair' feature.
Currently, there is no third-party decryption tool for LockBit ransomware. However, paying the ransom is not advisable as such actions not only encourage the criminals to continue their extortion business but also finances other forms of crime, including the online drug trade.
Users can use backups saved on external or cloud devices to recover their data. However, users are advised to remove the ransomware before they attempt data recovery operations. Otherwise, the ransomware will corrupt their newly-restored files.
Technical Improvements
LockBit has several interesting features that set the ransomware apart from other threats of the same category. This particular ransomware allows its operators to breach corporate networks and encrypt hundreds of devices in just a few hours.
LockBit also jeopardizes its victims' privacy and security by leaking their data online.
According to cybersecurity company Cynet, new LockBit variants have several technical improvements that allow the threat to impersonate legitimate Microsoft processes.
Initial Infection
LockiBit is used in targeted brute-force attacks. According to research published by the security company McAfee, it takes several days for the attackers to crack a network admin account password.
Once the admin password is cracked, the attackers obtain all the necessary permissions to deploy the ransomware successfully.
Researchers report that in some LockBit attacks, the attackers used known post-exploitation frameworks.
"[T]he attacker often uses known post-exploitation frameworks, for privilege escalation, lateral movement and performing any additional actions on their objective," reads McAfee's paper.
Interestingly, as LockBit variants are part of RaaS business operations, the threat could also be spread via standard mass-distribution tricks, such as malspam, Trojans, fake updates, pirated software, and others.
Ransomware-as-a-Service
Mcafee reports that a threat actor named Lockbi or LockBit was offering LockBit as a "bespoke" ransomware-as-a-service for limited partners/affiliates.
In an advertisement published on several popular underground forums, the seller provides a general description that matches the LockBit behavior researchers observed in the wild.
Figure 3 : LockBit Advertisements

It is worth mentioning that the seller appears serious as they put down a deposit of 10,5 BTC (about $113,950) in escrow. Escrow deposits are used to guarantee that the seller won't scam their potential partners because if they don't keep their end of the deal, they will lose the deposit.





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.