
Tycoon ransomware is one of the latest cyber-threats deployed in cyberattacks against small to medium size software organizations and education industries. Tycoon ransomware was first seen in December 2019. Researchers have discovered variants of the Java-based ransomware Tycoon that are capable of targeting Windows and Linux systems.
“This is the first time they’ve seen a ransomware module compiled into a Java image file format, or JIMAGE. These files contain all the components needed for the code to run — a bit like a Java application — but are rarely scanned by anti-malware engines and can go largely undetected.” - Statement by BlackBerry
Table of Contents
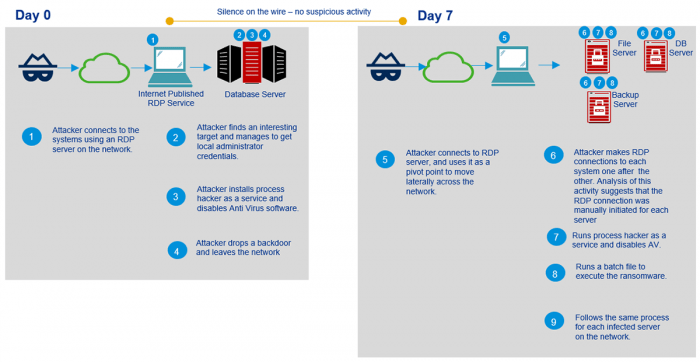
Tycoon Ransomware is Manually Deployed
Security researchers found that Tycoon ransomware is manually deployed, with the attackers targeting individual systems and connecting via RDP server. Once a target is identified and infiltrated using local administrator credentials, the malware operator disables any antivirus software and installs ProcessHacker, a hacker-as-a-service utility.
Tycoon takes the form of a Java Runtime Environment (JRE) and piggy-backs on an obscure Java image format (JIMAGE) to infiltrate a targeted machine, Doing this means that the ransomware passes by antivirus detection without being spotted. Since the JRE build contains both a Windows batch file and a Linux shell, security researchers suggest that malware operators can use Tycoon to encrypt both Windows and Linux servers.
Figure 1: Image: Java image file format (JIMAGE)
Screenshot of the ransom software module complied with JIMAGE. Source: Small Tech News
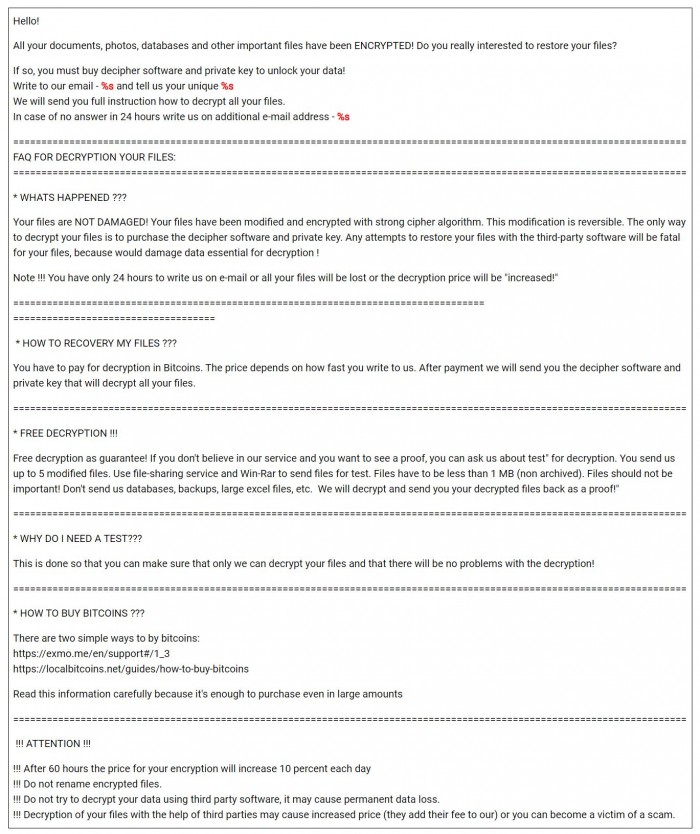
Once the ransomware infiltrates the victims’ networks using vulnerable RDP servers, it encrypts the files stored on the systems. According to security researchers, malware operators use a strong, off-the-shelf encryption algorithm to lock the victims’ files in exchange for a ransom payment, usually demanded in cryptocurrency, as shown in the ransom note below.
Figure 2: Image: Tycoon Ransomware Ransom Note
Caption: The ransom note informs the victims what to do to recover their files. Source: Small Tech News
Unfortunately, even if the victims pay the ransom fee, their data is not always decrypted. Therefore, the cybersecurity community warns that paying the ransom is not recommended as it only motivates threat actors to carry out more ransomware campaigns.
Tycoon Ransomware Campaign is Still Ongoing
A rather disturbing fact about Tycoon ransomware is that the malware campaigns involving Tycoon continue to this day. Until now, security researchers have only seen Tycoon targeting Windows systems, but shell scripts in the ransomware's Java modules contain both Windows and Linux variants.
Due to the similarities in the email addresses, names of encrypted files, and the text of the ransom notes, the researchers suggest that Tycoon could be linked to Dharma ransomware (a.ka. Crysis ransomware), though this claim is not confirmed and analysis of the ransomware continues.
There is No Decryptor for the New Tycoon Ransomware
Currently, there is no decryptor for the latest version of Tycoon ransomware. Since it uses asymmetric RSA algorithm to encrypt the securely generated AES keys, the file decryption requires obtaining the attacker's private RSA key. However, “Factoring a 1024-bit RSA key, although theoretically possible, has not been achieved yet and would require extraordinary computational power”, security researchers say.





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.