
There’s a new wave of malicious spam going around that purports to contain a “critical Windows Update” that instead tricks users into installing the “Cyborg” ransomware, according to researchers. Researchers were also able to access the builder for the malware, which could then be used to make variants of the malware.
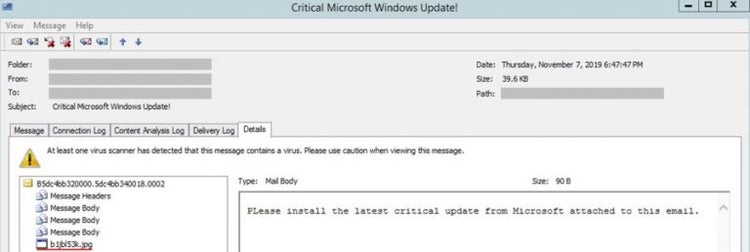
This email threat, recently uncovered by researchers with Trustwave, is unique among phishing emails. The researchers outlined the threat in a blog post that explained the file that contains the malware claims to be a .jpg picture file despite being an executable .exe file.
Another thing that sets the email apart is that it has two sentences in the subject line – “Install latest Microsoft Windows Update now! Critical Microsoft Windows Update!” – but the email body has just that one line. Malicious emails generally feature a longer message that has been socially engineered to trick and confuse readers into downloading malicious files.
Perhaps one of the most important elements of the analysis was that researchers were able to follow a trail from the executable file all the way back to the malware builder hosted on the developer platform Github.
The post says that the 7Zip file for “Cyborg Builder Ransomware V 1.0.7z” had been uploaded to the platform two days before the misterbtc2020 account hosted the Cyborg ransomware executable file.
This adds an entirely new dimension to the latest ransomware attack. Ransomware is used to attack governments and organizations. Having a copy of the ransomware available on a public software development platform like Github means that anyone could download a copy of it and create – and use – their own strain of Cyborg.
This fake email about a Windows Update contains all the usual elements of a piece of malicious spam. That was how researchers were able to discover it. Researchers said it was fairly obvious what the email was about given the subject line and a straight executable file that claimed to be a .jpg and wasn’t even contained in an archive.
The researchers let GitHub know about the ransomware on Sunday, November 17th. GitHub is still processing the report, and – as of the time of writing – the account hosting the ransomware is still active on the site.
It seems like the threat has been abated, though, with researchers noticing that there appears to be no more emails containing the downloader being sent. That said, there is still the potential that other variations could be made and released, given the builder is still available on the GitHub platform.
The ransomware could be built and then spread by anyone with a copy of the builder. It could be offered in a variety of different ways and formats to better get around email gateways and increase the chance of infection.
Ransomware, as a whole, appears to be a problem that is getting worse and worse. People are finding better and more creative ways to reach – and target – their victims. Research from last month suggests that ransomware attacks could reach new heights in 2020, mainly for campaigns that go after specific targets.
While it seems like there was no specific target this time, there is evidence that the prediction over ransomware is coming true. Web hosting provider SmarterASP.net was targeted by ransomware last week that took down all the websites the company hosted for their customers.





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.