
In August 2020, Microsoft released a new security patch addressing 120 vulnerabilities, including two zero-day vulnerabilities. The fix focuses on the CVE-2020-1472 vulnerability and allegedly protects Microsoft’s customers from attacks that let attackers take over enterprise networks.
However, researchers at the security company Secura published a proof of concept for a Windows vulnerability that can allow attackers to become Domain Admins with just a few clicks. According to Tom Tervoort, a security expert at Secura, all the attackers need is a connection to the Domain Controller.
What is Zerologon?
The Zerologon attack exploits the CVE-2020-1472 vulnerability, which provides elevation of privileges within the Netlogon service. According to Secura’s research, the security bug results from a flaw in a cryptography authentication scheme used by the Netlogon Remote Protocol.
The Netlogon service is an authentication mechanism responsible for various operations, including allowing end-users to log in to a network. It is secured by an AES-CFB8 cipher that encrypts and validates authentication messages.
However, for the AES-CFB8 cryptographic protocol to work properly, the so-called initialization vectors must be unique and randomly generated with each message. The vulnerability exploits a flaw where Windows fails to do this.
Zerologon exploits the slip-up by sending Netlogon messages that include zeroes in various carefully chosen fields to obtain domain admin credentials.
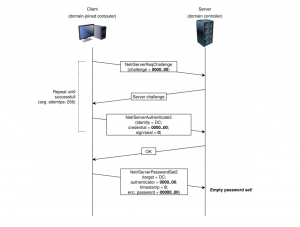
Figure 1: Zerologon Attack Process
Zerologon attack that replaces the domain password. Source: Secura
“By forging an authentication token for specific Netlogon functionality, he was able to call a function to set the computer password of the Domain Controller to a known value. After that, the attacker can use this new password to take control over the domain controller and steal credentials of a domain admin,” Tervoort explained.
An attacker could exploit the security bug to impersonate any computer, including the domain controller, and execute remote procedure calls on their behalf, as well as to change a computer’s and domain controller’s passwords.
Researchers warn that this attack has a huge impact. It can be used to deliver malware, spyware, and ransomware on the target network.
Despite addressing the vulnerability in the latest security patch, Microsoft provided only a temporary solution. The company promises to release a complete patch in February 2021.





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.