The threat of GrandCrab may be over but the hydra of ransomware lives on thanks to the birth of SNAKE ransomware. Researchers noticed the malware and believe that it could pose a major threat to business and enterprise security in particular.
Cybercriminals have started deploying ransomware threats to attack industrial control systems (ICS). These targeted attacks are believed to be the first instances of cryptolockers being explicitly built to control manufacturing processes.
There are multiple ransomware threats that perform targeted attacks at enterprises and industries. A recently found ransomware known as both Ekans and Snake ('Ekans' being 'Snake' spelled backwards) caused quite the stir after researchers discovered that it poses as a multilevel risk.
Table of Contents
Ekans Ransomware Could Stop Production Processes
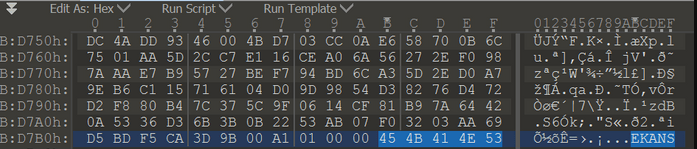
The ransomware was brought to the public eye thanks to the MalwareHunterTeam and Vitali Kremez. The ransomware earned the name “SNAKE” because of how it modifies the “EKANS” file marker for hijacked files.
Researchers report that Ekans ransomware is a heavily obfuscated threat that is specifically designed to attack industrial control systems. The threat is capable of causing severe disruptions of normal business operations, as well as extorting hefty ransoms from its victims.
Ekans performs a list of attacks aimed at stopping industrial system-specific functions. The ransomware force stops 64 processes that are related to security and management software, data backups solutions, ICS-related services, and services that correspond to virtual machines and remote management tools.
Researchers point out that Ekans' basic brute force attacks neither inject commands nor manipulate ICS processes. They merely interrupt the routine operations. Executed on the right system, however, these basic attacks could provoke unpredictable physical effects, even causing loss of future profits.
Ransom Extortion Is Still on the Menu
Once Ekans gains access to a computer system, it will delete backups and volume shadow copies from the device. The ransomware will then launch processes killing attacks that stop all services that might interfere with its further operations. This behavior is similar to the Clop ransomware virus, which was notorious for the amount of Windows processes it could kill.
After Ekans kills all targeted processes, it will proceed with file encryption. The ransomware will corrupt all files on the target device, skipping only the ones that are essential for the normal OS operations.
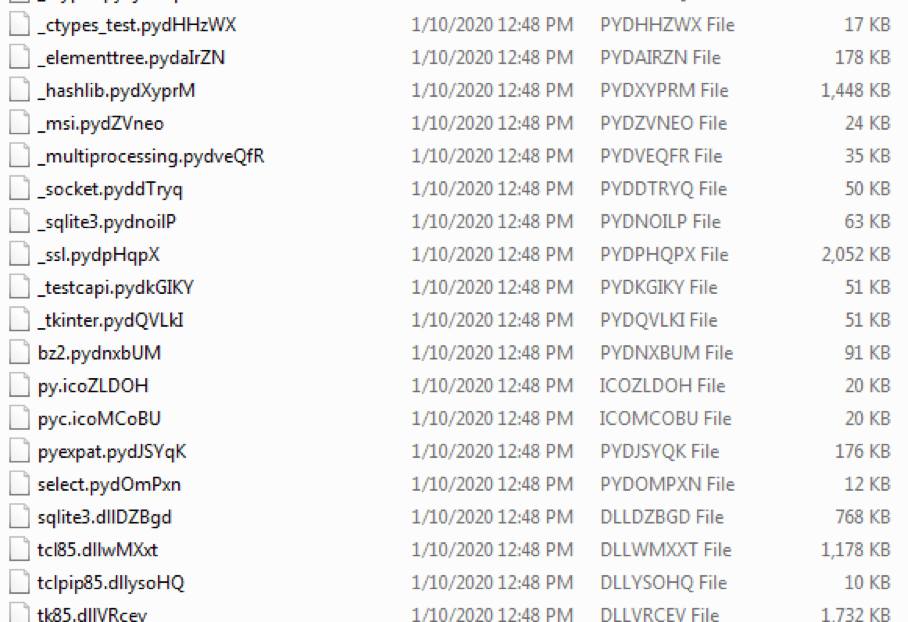
Folders and files whitelisted by Ekans:
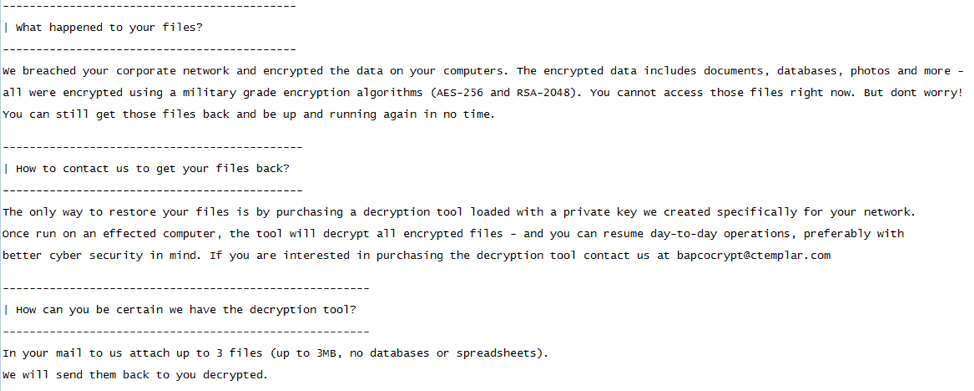
After Ekans is done with its encryption routine, it will display the encrypted files with the modified file names and a 'Fix-Your-Files.txt' containing the ransom note.
Ekans’ Infection Vector and Relationship to Other Malware
It is currently unknown how the ransomware reaches its victims. Ekans' close relation to other malware families such as MegaCortex and Ryuk suggests that the initial infection might be supported by another threat that preexisted on the target computer system. Malware-dropping Trojans Trickbot and Emotet, which have recently made the headlines for playing a part in massive targeted attacks, are also under a cloud of suspicion for dropping Ekans.
Also, researchers at Dragos note the ransomware's close link to the deadlier MegaCortex ransomware. The fact that the two ransomware share similar ICS-orientated characteristics means not only that Ekans is not one-of-a-kind but also that MegaCortex and other malware could be used in future attacks.
Researchers also point out that such ICS-orientated attacks indicate that the threat actors have specific targets in mind. They highlight the need for better cybersecurity in the manufacturing industries because sophisticated threats are now being directly used to influence computer networks that control operations in manufacturing and utility environments.





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.