
A phony decryptor for the infamous STOP Djvu ransomware has been double-corrupting data. Security researcher Michael Gillespie warns that an on-going malware campaign uses false promises for free file decryption to spread a new ransomware threat known as Zorab.
Table of Contents
STOP Djvu Ransomware is Used as a Bait
Despite having a higher infection rate than the infamous Maze, NetWalker, and REvil ransomware combined, STOP Djvu ransomware is rarely reported by the news outlets. This is because, unlike the other threats, STOP Djvu doesn't target high-profile targets but focuses on regular PC users.
Since it was first discovered in December 2018, STOP Djvu ransomware has been infecting victims non-stop, with 2019 being its most active year. With the threat of having 160 variants and over 116,000 confirmed victims, it comes as no surprise that the criminals behind Zorab chose this specific ransomware as bait for their malware campaign. Furthermore, STOP Djvu is usually spread via pirated content, such as cracked software. Most of its victims are unlikely to be able to afford the $500 ransom and, therefore, often look for a decryption solution online, leading them into becoming prey for Zorab.
False promises for free Stop Djvu ransomware decryption lure the unsuspecting users in yet another trap, infecting them with Zorab ransomware, which worsens their situation even further by adding an additional layer of encryption over their already locked files data.
How Zorab Ransomware Encrypts Data
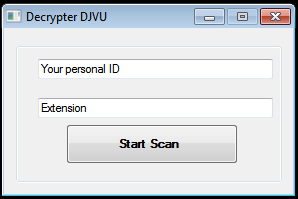
When STOP Djvu victims attempt a free file-recovery with the phony decryptor, they will be presented with software that, much like a legitimate tool, asks them to enter their ID and the ransomware extension. The victims will also be offered to scan their devices. However, if they click on the "Start Scan" button, an executable called "crab.exe" will be extracted into the %Temp% folder.
Figure 1: Fake Decryptor
This is a screenshot of phony decryptor, which asks the user to enter an ID and file extension. Source: Michael Gillespie via Twitter.
Crab.exe is the payload of Zporab ransomware, which will encrypt the user-generated data with the strong AES-256 encryption algorithm. The threat will add the .ZDB extension at the end of the encrypted files. Additionally, it will drop a ransom note in each folder that contains corrupted files.
Zorab's ransom note is a simple text file called "--DECRYPT--ZORAB.txt.ZRB." It contains a brief explanation of the victim's dire situation and lists instructions on how the threat operators can be contacted.
Ransom Note
—+-= ZORAB =-+—
Attention! Attention! Attention!
Your documents, photos, databases and other important files are encrypted and have the extension: .ZRB
Don't worry, you can return all your files!
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
if you want to decrypt your files The only method of recovering files is to purchase decrypt tool
This tool will decrypt all your encrypted files. To get this software you need write on our e-mail: zorab28@protonmail.com
What guarantees do we give to you?
Its just a business. We absolutely do not care about you and your deals, except getting benefits.
You can send 2 your encrypted file from your PC and we decrypt it for free.
+--Warning--+
DONT try to change files by yourself, DONT use any third party software for restoring your data Your personal id: [XXXXX]
Source: Emisoft
The ransom note is very generic, containing standard information and set phrases that almost all ransomware operators use. Even the warning at the end of the note is very common, used to scare the victims that only software developed by the criminals can recover the encrypted data, which is definitely not the case.
To Pay or Not to Pay?
The criminals behind Zorab ransomware don't list a standard decryption price. Instead, they engage the victim in negotiations. Additionally, they promise to decrypt one file for free as proof that they are able to hold their end of the deal. However, there is no guarantee that they will follow through.
Security experts advise the victims not to contact the ransomware operators because such activities are unlikely to have a positive outcome. Cybercriminals are usually experienced manipulators who use social engineering techniques to trick their victims into unwanted actions. Not to mention that paying the ransom is no guarantee of successful file decryption.





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.