A new ransomware dubbed Conti surprised security analysts with incredibly fast file-encryption and command-line operations. Security company Carbon Black reports that the malware is a unique twist of a modern threat that uses a rarely-seen high number of simultaneous CPU threads to lock its victim's data with speed and efficiency. The threat is primarily used in targeted attacks against enterprise organizations.
Table of Contents
What is Conti ransomware
Conti ransomware is not an entirely new threat. It was reported to the public in February 2020 and has been active ever since. However, isolated attacks from between November-December 2019 are also linked to the ransomware.
It is speculated that Conti is related to the infamous Ryuk ransomware. However, new research by CarbonBlack sheds light on the new threat, revealing hidden details and a unique and advanced structure.
Conti's attack follows a standard ransomware scheme. It infects the host, scans the files on the local system, as well as those on network shares, and locks the encryptable data. The ransomware uses AES-256 encryption via a hard-coded public key to encrypt the data and prevent the user from accessing it.
Following successful encryption, Conti drops a ransom note. A text file named CONTI_README.txt gets saved in each folder that contains corrupted data. The document contains a brief explanation of the situation and lists the attackers’ demands. A specific ransom price is not mentioned. Instead, victims are asked to contact the attackers via email.
Speedy encryption
Although on the surface Conti appears to be a standard cryptolocker, the threat stands out with quick file-encryption, used only by advanced malware threats. According to Carbon Black, Conti uses up to 32 simultaneous CPU threads to encrypt files. By applying threaded encryption, this ransomware improves its performance, corrupting data dozens of times faster than a standard ransomware operation.
Figure 1: Conti creating 32 simultaneous threads
![]() Caption: the malware uses the CreateIoCompletionPort() call to create 32 instances of this worker thread into memory. It feeds the created file list to the threads for immediate encryption. Source: Carbon Black
Caption: the malware uses the CreateIoCompletionPort() call to create 32 instances of this worker thread into memory. It feeds the created file list to the threads for immediate encryption. Source: Carbon Black
Of course, Conti is not the first multi-threaded ransomware. Other fast file-encryptors, such as REvil (Sodinokibi), LockerGoga, and MegaCortex, have been making the headlines for months. What sets Conti apart from the other fast encryptors is its implementation of command-line operations, advanced obfuscation techniques, and unique data targeting strategy.
Command-Line Capabilities
Only a small number of ransomware families have command-line capabilities that allow the malware operator to orchestrate the attack. Ransomware threats are usually designed to act autonomously without human intervention. However, Conti combines the best of both worlds.
Although Conti is designed to follow a standard procedure, encrypting the local data and any connected network share, the threat can also be operated remotely to target specific network shares or hard drives.
According to the research, Conti can be executed directly by an adversary that is monitoring the target environment. The attacker can instruct the threat to keep a low profile, only targeting specific network shares or local drives and then exit.
Alternatively, the attacker can use the command-line argument "-h," which points to a text file that contains lists of network host names. This operation allows the ransomware to go over hosts it routinely connects to and target specific machines.
Researchers warn that the command-line feature allows Conti to cause targeted damage that offsets incident response activities. Furthermore, by limiting the targeted devices, the attacker limits the overall "noise" of the attack, making the invasion less noticeable. Such a structure could help Conti remain unnoticed for days, allowing the malware operator to attack hundreds of systems until a user notices an encrypted file.
System Preparation
Before it attempts to encrypt any files, Conti will prepare the system for the operation. The ransomware will start by deleting the Volume Shadow copies. The threat will also use a Windows API called "Windows Restart Manager" to unlock files for encryption.
The Restart Manager, which is a component of Windows OS, is designed to close all running programs and open files when the OS starts. If the manager detects open files and unsaved data during reboot, it will alert the user to save their information. However, after a predefined amount of time, all executables will close and Windows will continue to restart.
Apps can also use the Restart Manager to unlock specific files. Conti exploits this feature to maximize the amount of damage. By processing each file through the Restart Manager, the ransomware ensures that they are unlocked and ready for encryption.
Figure 2: Implementation of Restart Manager
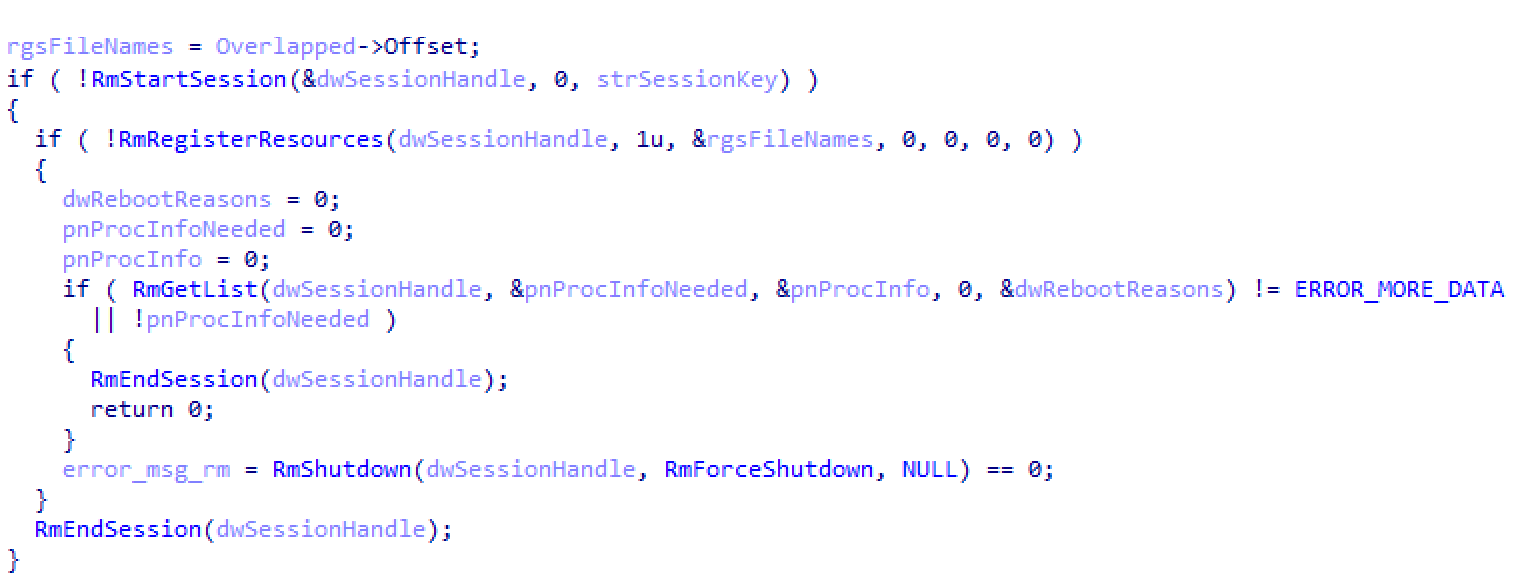 Caption: In this image, we can see a portion of the code used to call the Restart Manager on a file path. Source: Carbon Black
Caption: In this image, we can see a portion of the code used to call the Restart Manager on a file path. Source: Carbon Black
Anti-forensics mechanisms
While analyzing samples of the ransomware, Carbon Black faced multiple anti-analysis features that slow the ransomware detection and hinder any reverse engineering attempts.
A unique string encoding routine is Conti's primal form of resistance. The encoding method is applied to almost every string text, coming to a total of 277 individual algorithms (one per string). According to the research, nearly 230 of these algorithms are placed in dedicated subroutines. This structure expands the ransomware's code, making even a simple program look complicated and advanced, resulting in harder malware analysis that is time-consuming and unpleasant for the analysts.
Figure 3: Deobfuscated Value
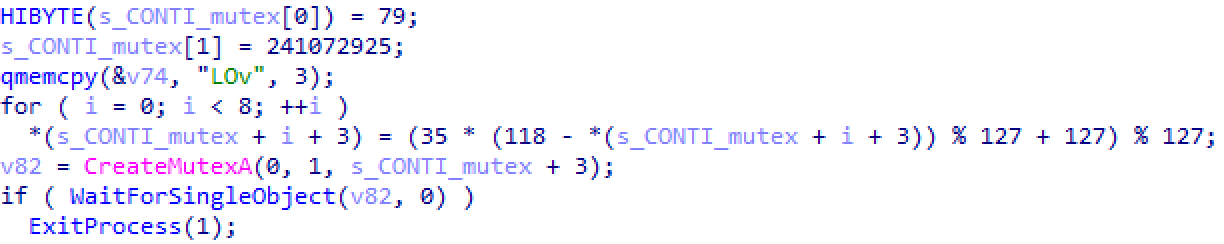 Caption: In this image, we can see the deobfuscated inline string for the mutex of the value "_CONTI_." Source: Carbon Black
Caption: In this image, we can see the deobfuscated inline string for the mutex of the value "_CONTI_." Source: Carbon Black
Another obfuscation hack is applied to various Windows API calls used by the ransomware. Although it's common for malware to scan API calls during execution, researchers point out that Conti goes one step further, decoding these routes on-the-fly. The malware resolves to the actual API and then stores it into a global variable that can be easily reached and used when needed.
Conclusion
Conti ransomware is an interesting threat that implements rare techniques. It not only follows the footsteps of destructive malware families but also breaks records. Researchers warn that in the wrong hands, this ransomware could become a deadly weapon.
There is currently no third-party recovery tool for Conti's encryption. However, experts advise against paying the ransom. Such actions do not guarantee results. They only encourage cyber attackers to continue their malicious operations.





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.