
Researchers have been investigating a malware campaign that targets online banking users in Brazil. The attackers used a malware called Vizom, designed to take over victims' devices in real-time.
IBM's researchers Chen Nahman, Ofir Ozer, and Limor Kessem have published an analysis of a new malware campaign targeted at Brazilian online banking users. IBM’s analysis showed how cybercriminals use the Vizom malware, which uses unusual DLL hijacking tactics to stay under the radar, to carry out remote overlay attacks.
Table of Contents
Infection vector
Attackers typically spread Vizom via malspam messages that use a popular video conferencing app as a lure. Upon infiltration, the malware will corrupt the AppData directory and begin its infection chain.
Figure 1: Infection Flow
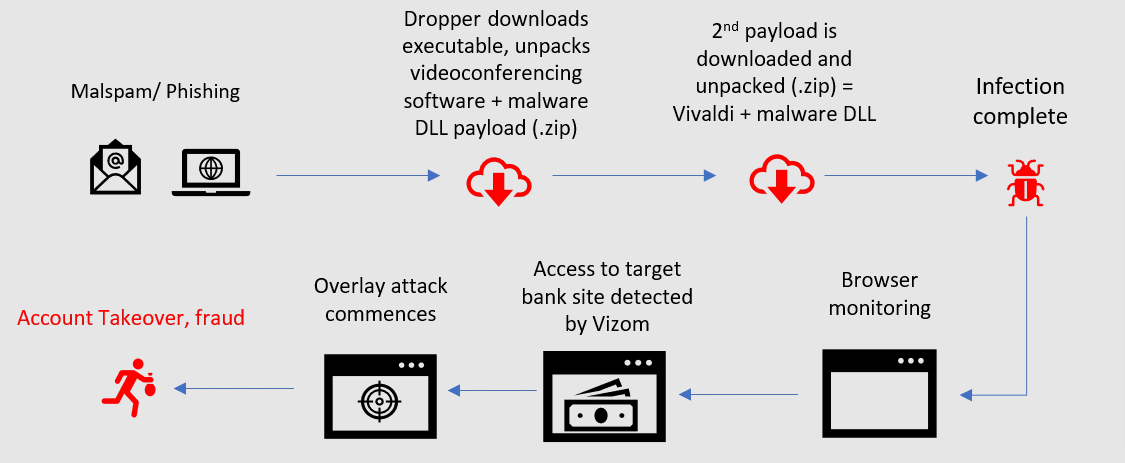
According to the research, Vizom's dropper delivers a .ZIP archive that computers unpack into the %temp% folder. The archive deletes itself after extracting all the data into the Temp folder.
Vizom's next steps take advantage of the inner mechanics of Windows’ operating system. As the OS often needs to load files without having fully qualified file paths, it will search for the correct location. Vizom's developers have found a way to exploit this design by saving its Delphi-based DLLs in the same directory as the executable that loaded it.
In the most recent campaigns, the target executable is "Cmmlib.dll," which belongs to popular video conferencing software.The malware tricks Windows to allow its malicious code to run via the main Cmmlib.dll executable by adopting this exploit.
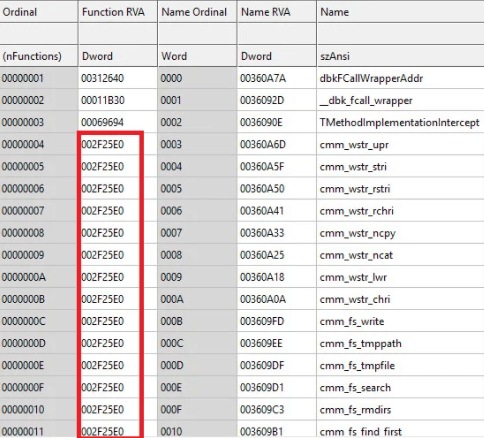
Researchers point out that Vizom's threat actor went a step further, copied and modified the whole export list of the legitimate DLL, so that the malware execution will run smoothly and won't be noticed by anti-virus software as all functions route to the same address.
Figure 2: Vizom's DDL Export List
Vizom uses the DLL hijacking trick to download and launch a RAT (Remote Access Trojan) as a second-stage malware. The threat will use the command prompt to launch "zTscoder.exe," which is yet another legitimate binary exploited to download a malicious .ZIP archive.
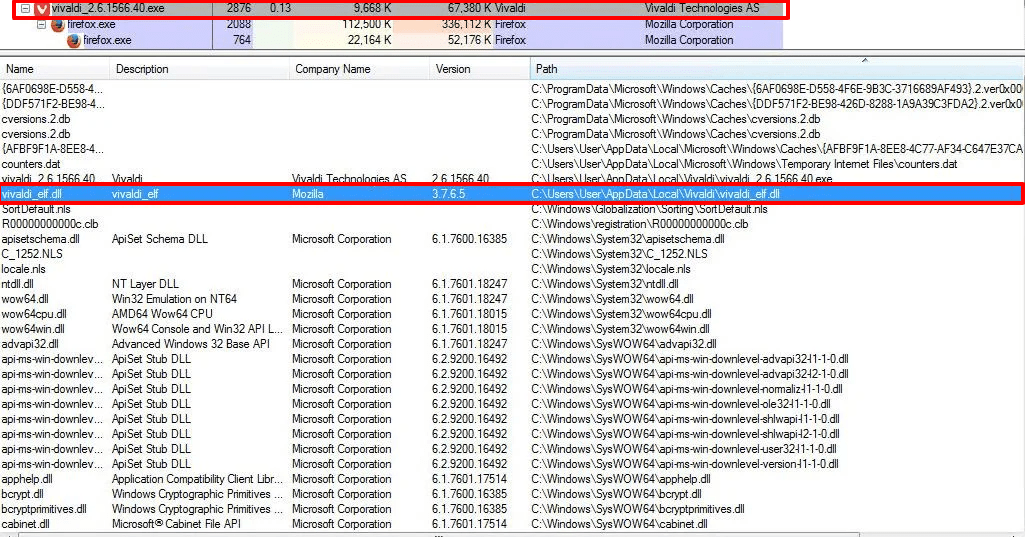
Similar to the first infection stage, Vizom will extract the newly downloaded.ZIP archive content, which delivers a weaponized executable of the legitimate web browser, Vivaldi, that the virus later exploits to camouflage the malicious DLLs.
Figure 3: Vizom Malware Corrupting AppData
Persistence
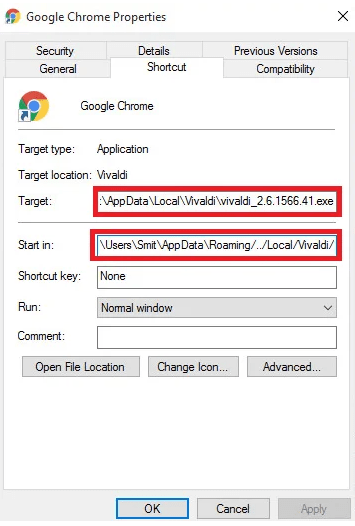
To establish persistence, Vizom will modify browser shortcuts to lead to its executable and keep it running in the background no matter what browser the user attempted to run.
Figure 4.1: Chrome Link File Used by Vizo
To avoid suspicion, Vivaldi will run the corresponding program (in this case, Google Chrome) as a child process to the primary Vivaldi process.
Figure 4.2: Running Chrome as a child Process
Meanwhile, Vizom will run in the background, monitoring the user's browsing and waiting for users to access an online banking website. When a window's title matches a Vizom's target list entry, the malware will alert the attackers to connect remotely to the victim's device.
Data Exfiltration
Unlike other sophisticated malware, Vizom does not hook the browser but monitors activity by comparing the window title the user is viewing to target strings of text designated by the hacker. Upon detecting a bank's web platform, Vizom will notify the attacker to start an overlay attack.
As Vizom has RAT capabilities, the attacker can take over a compromised session and deploy overlay content in intercept information transfer. The technique tricks the victim into entering sensitive information, such as usernames and passwords, into fake windows that imitate the target banking website’s design.
Vizom does this by generating HTML files that are then loaded in Vivaldi. The virus then launches a keylogger to capture the target data and export it as an AES256-encrypted package to the command and control (C&C) server.
Vizom will also exfiltrate screenshots from the infected device. The malware employs two different techniques to capture the victim's screen. Vizom could use either the PrintWindow API function, a common way to take screenshots on Windows, or the "settypebit" command, which initializes the Windows magnification library.
Conclusion
Vizom is just one of many banking trojans, such as Zeus Sphinx, TrickBot, and Ginp, operated by attackers whose only objective is to steal money from online banking users.
Researchers warn that although Vizom is currently operated in Brazil, attackers could adapt it to target other countries.





Leave a Reply
Thank you for your response.
Please verify that you are not a robot.